All Aboard the COVID-19 Train:
Since the outbreak of COVID-19, plenty of COVID-19 themed malware attacks have surfaced around the globe. Attackers take every chance they get to spread their malware, and the pandemic has given them ripe opportunities.
Based on data from D-Cloud, Deep Instinct’s Threat intelligence, and telemetry cloud environment, the number of attacks has overall risen. This is particularly seen in the number of malicious executables and Office documents, which are commonly used to deliver the former. We believe this to be linked to an increase in malware attacks and malicious activity during the pandemic. Our data is consistent with trends seen elsewhere, which also point to an increase in attacks since the beginning of the pandemic. For example, the amount of malicious Office documents, which were seen in the first half of 2020, is greater by 62% than the amount of the same type of files, which were seen in the first half of 2019. The increase correlates with waves of COVID-19 phishing attacks, which commonly use this type of file. A comparison for the same time periods in 2019 and 2020, shows the number of malicious executables went up by 40%.
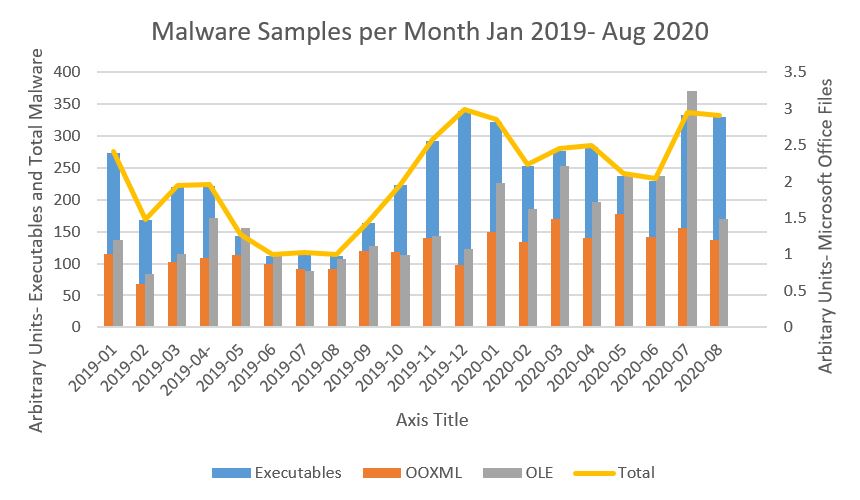
Figure 1: The number of new malware samples per month, since the beginning of 2019. In the graph, Microsoft Office documents are divided between the older format- OLE and the newer format- OOXML. The numbers are shown in arbitrary units, where the number of malicious OOXML files in January 2019 is set to 1.
When the first waves of this ongoing pandemic crashed, attackers directed their efforts towards phishing campaigns and mal-spam attacks, sometimes pretending to originate from legitimate sources, like the World Health Organization. Others chose to exploit the work-from-home model, in which corporate networks that were relatively secure, could now be accessed from insecure locations. Likewise, meetings that were usually done in closed doors were now held using vulnerable virtual communication apps.
Targeting the Good Guys
One would be forgiven for thinking that the organizations which stand on the front line in the fight against the pandemic would be left alone, too important to be targeted by malware at this difficult time. However, that has unfortunately not be in the case.
Since the outbreak, health organizations and their employees have been targeted more than usual, with an increase of more than two fold in targeted cyber-attacks against the World Health Organization, compared to last year. Spam and phishing campaigns were launched, some specifically targeting top officials at the WHO via both personal and corporate email addresses. Fake login websites for health workers have also been created, one even mimicking the World Health Organization’s eternal email system.
Sure, some threat actors initially stated that they wouldn’t target health organizations during the pandemic, but that doesn’t mean they kept their word. For example, the group behind the infamous Maze ransomware released a statement in March 2020 that it would avoid infecting medical facilities and research labs during the pandemic. Yet, just a few days later they released stolen data from “Hammersmith Medicines Research”, a London based lab that develops vaccines. That wasn’t the end of it, Maze infected more health facilities, not only interrupting their work, they also threatened to release patient records online if their ransom wasn’t paid. A threat would have exposed the compromised clinics to expensive GDPR lawsuits.
Come and Knock on Our Door
When organizations had no choice but to let their employees work out of their fairly secure offices and in their less than secure homes, suddenly the hacker’s job, just got a lot easier. They no longer had to work hard to craft malware samples that will pass corporate security solutions, they just needed to make unsuspecting employees open a malicious email attachment or download their malware from the internet. An example of an organization that was severely impacted by the shift to the work-from-home model is Cognizant, a Fortune 500 company. As the company was adjusting to its remote working environment they were attacked by Maze ransomware. The remediation and reperations costs were enormous, estimated to be between $50 to $70 million USD.
Moreover, the fact that many people use the same computer for work and personal use, and sometimes even share these devices with other family members, opens the door for even more malicious samples.
In addition, malware authors that decided to put more effort into the game, started looking for vulnerabilities to exploit in apps and services that became common during the pandemic, in order to reach a large crowd. An example of this is Zoom, which after experiencing a burst in popularity, suffered a string of security issues. One of which was a data breach in April that exposed over 500,000 Zoom credentials and a vulnerability that allowed arbitrary code execution on vulnerable endpoints.
Fake Android Apps
Many organizations and governments have launched applications that provide users with updated information about the pandemic. Seizing the opportunity, cyber-criminals used this surge of applications to launch their own versions, which are less helpful and more harmful. A common type of app is a “COVID-19 Tracker”, which gives information about infected people’s previous routes and current locations.
During the pandemic, the Ginp banking trojan launched an Android app pretending to be a tracker that showed users a (fake) number of infected people in their current area. The software stated that it could give more details about the infected people for 0.75 Euros. If the users chose to sign-up, they were asked to provide their credit card information, which of course would be stolen by Ginp, without ever having charged the card, nor providing the requested information.
Another malware that exploited the tracker theme is CryCryptor. On June 18th 2020, the Canadian government announced it would back the development of a nationwide voluntarily tracing app that would provide details of exposure to Covid-19. Just a few days later, CryCryptor launched ransomware pretending to be the app. Links to this fake app could be found in two Coronavirus themed websites, which the attackers had created. When the malicious software was downloaded, it asked for permission to access files on the infected device, on being provided, it used the permissions to encrypt targeted files, such as photos and videos, and left a ransom note in each affected folder.
Our Crystal Ball
True Machiavellians, cyber-criminals focus on what they think will serve their purposes best. For that reason, we expect new malware campaigns to evolve in line with COVID-19 trends and developments. As national governments adjust their COVID-19 related regulations to meet the changing spread of the virus, people have struggled to keep up to date. Attackers may seize on this opportunity to launch mal-spam campaigns related to COVID-19 regulations, malicious websites with “updated information” and perhaps fake apps on “updated regulations”. Another possible approach attackers might take, is to take advantage of the interest surrounding a future vaccine to send phishing messages with malicious attachments, pretending to have new information about a promising vaccine to resolve the pandemic.
The up-and-coming school year may also draw the attention of malware authors, especially those who prefer ransomware as their final payload. Like many organizations, schools and academic institutions had to adjust to the situation and change the way they operate, with many turning to online classes. This means that if ransomware finds its way from a student’s home PC into the school’s network or in a more targeted attack, it can paralyze the school. Without the possibility of turning to the ‘ol’ pen and paper’, the infected school district or college may easily cave in and be forced to pay the ransom.
A more permanent change that we will probably see, is the shift to a semi or full work-from-home model for the corporate workplace. During the pandemic, organizations realized that working from home has some advantages- many employees reported that they focus better at home, some even logged more hours, while companies discovered they can save a lot of money on facilities. If many organizations choose to permanently operate in a full or semi work-from-home model, hackers may well respond to exploit the situation, by crafting attacks that leverage the widened attack surface of remote working or by finding more vulnerabilities in software enabling remote working.
Naturally, a company that chooses to operate in a remote working environment needs to take this increased risk into consideration, on top of other risks it may face. Additionally, companies will need to equip employees with the right tools, such as endpoint security solutions and proper security training.
No matter how attackers choose to operate, users need to be more vigilant than ever, always keeping in mind that significant events, be it the COVID-19 outbreak or the upcoming U.S. elections, always draw attackers’ attention and that the next malware infection may just be one click away.

