Malicious JARs and Polyglot files: “Who do you think you JAR?”
Throughout 2022, Deep Instinct observed various combinations of polyglot files with malicious JARs.
The initial technique dates to around 2018 when it used signed MSI files to bypass Microsoft code signing verification. A year later, in 2019, Virus Total wrote about the MSI+JAR polyglot technique. Microsoft decided not to fix the issue at that time. Then in 2020, this technique was again abused in malicious campaigns and Microsoft assigned CVE-2020-1464 to address the issue.
Despite being fixed, Deep Instinct observed in 2022 that the technique was still in use and included new types of polyglots which do not necessarily exploit the CVE; rather, attackers now use the polyglot technique to confuse security solutions that don’t properly validate the JAR file format.
What is polyglot?
A polyglot file is created by combining two or more file formats together in such a way that each format can be interpreted individually without an error.
This is a little tricky as you can’t make polyglots from any arbitrary combination of file formats, although there are quite a few options to choose from.
Why JAR?
JAR files are essentially ZIP archives. What’s special about ZIP files is that they’re identified by the presence of an end-of-central directory record which is located at the end of the archive. This means that any “junk” we append in the beginning of the file will be ignored and the archive is still valid.
Other file formats have a special magic header at the beginning of the file, and they should be read from the start, unlike JAR. One of these formats is MSI.
If those two are combined, we receive a file that is both a valid MSI and a valid JAR.
The 2022 Campaigns
Throughout 2022, Deep Instinct observed StrRAT and Ratty samples being distributed as polyglots or as JAR files with junk appended in the beginning.
Both RATs are known threats. For StrRAT, there is a configuration extractor. For Ratty, we wrote a config extractor of our own, which we shared with the community in GitHub: https://github.com/deepinstinct/RattyConfigExtractor
While we couldn’t determine whether the files belong to a single threat actor or to several threat actors, the usage of the Bulgarian hosting “BelCloud LTD” has been observed in many of the samples.
Additionally, we found a few Ratty and StrRAT samples that shared the same C2 server.
For simplicity we will categorize the files by what is appended to them.
#1 MSI:
Sample 5e288df18d5f3797079c4962a447509fd4a60e9b76041d0b888bcf32f8197991
If we inspect the file with the Linux file command, we see it’s an MSI file:
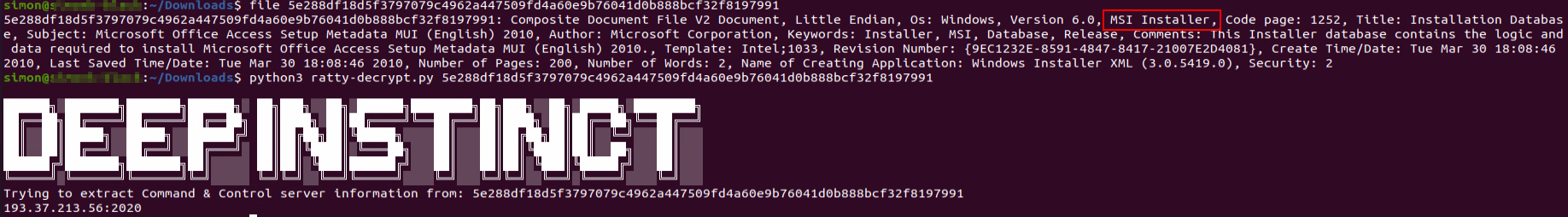
However, the file contains a valid JAR as well. Our Ratty configuration extractor was able to successfully extract the C2 server information.
This sample has been observed being sent using Sendgrid. While this is not unique, some of the StrRAT samples that were MSI+JAR polyglots have been sent via Sendgrid as well.
Some of the StrRAT samples using the MSI+JAR polyglot have been observed spreading with URL shortening services such as cutt.ly and rebrand.ly. In some cases, the samples were hosted on Discord.
#2 CAB:
CAB files have a unique magic header and are interpreted from the beginning to the end, which makes them a perfect candidate for a polyglot with JAR files.
We have observed both Ratty and StrRAT samples using CAB+JAR polyglots.
In particular, we found the Ratty sample f620c4f59db31c7f63e8fde3016a33b3bfb3934c17874dcfae52ca01e23f14de and the StrRAT sample 2f4c6eb0a307657fb46f4a8f6850842d75c1535a0ed807cd3da6b6678102e571 both using the CAB+JAR polyglot and using the same C2 server, donutz.ddns[.]net
![Figure 2: StrRAT and Ratty (CAB+JAR) linked to the same C2 server donutz.ddns[.]net](https://www.deepinstinct.com/image/bltfb077af360e7081e/63bee84a7a6762171d821d17/fig2-strRAT-and-Ratty-linked-to-the-same-c2-server.png)
#3 HEX Trash / Fake PE:
We are not sure if the files were made by mistake or on purpose by the threat actor, but those JAR files have HEX values appended to them:
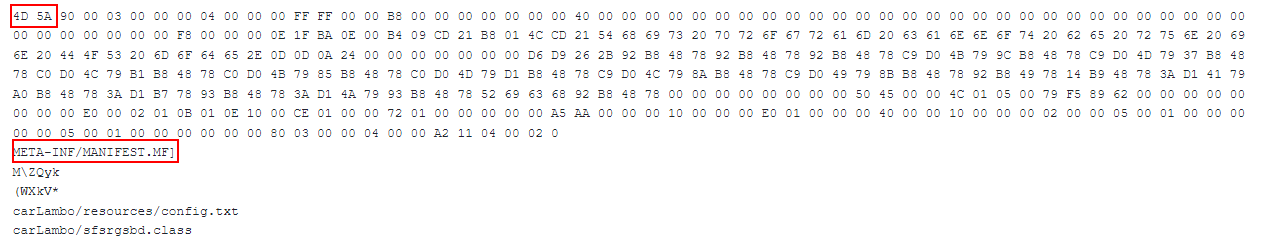
The appended textual hex value is of an executable file. While those files are not polyglots because the appended hex is just “junk” text, the Linux “file” command would return “data” such as the file type.
In this way attackers can confuse and bypass security solutions that would simply check the type of file using the Linux “file” command.
#4 Binary Junk:
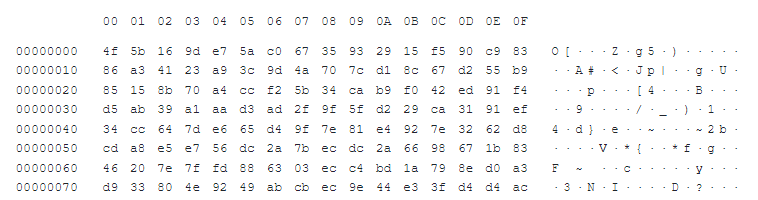
This variation is once again not truly a polyglot, and it is not clear if this is a mistake or if it was done on purpose. The appended content seems to be a part of some binary, but the appended data appears to be missing the beginning of the appended file.
The result is the same: a valid JAR file that is detected as “data” by checking the file type.
Is this effective? (YES!)
While Ratty and StrRAT are well known threats, some of those appended JAR files receive very low detections in VirusTotal:
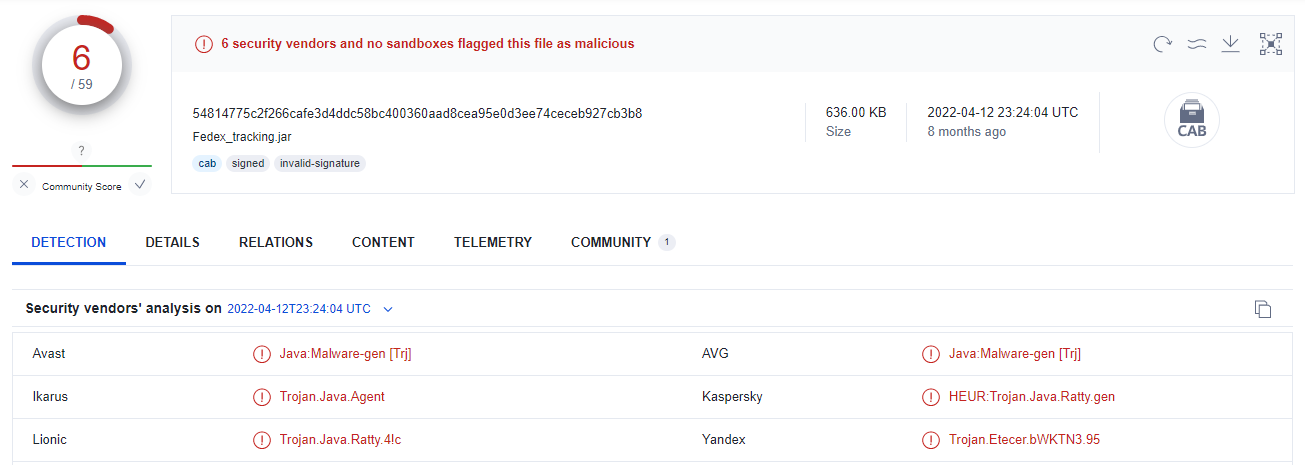
The VirusTotal detection rate doesn’t tell the true capabilities of specific vendors as some products behave differently when files are executed dynamically.
That said, we can clearly see that JAR files with appended content can stay undetected, at least until executed, even for known threats.
Can this be any worse? Yes, my friends, it can...
Let’s think about this from a detection engineering perspective. If we failed to identify a JAR file because we relied on the simple file type check, like Linux “file” command, the easy solution would be just to “scan” every file with the JAR extension. If you want to, you can even throw a validation that the file is a valid JAR by checking the presence of the end of a central directory record at the end of the file.
However, this is still not sufficient. JAVA does not care about the file extension and will happily execute a valid JAR file with any extension. The only downfall in renaming the “.jar” extension is that the JAR needs to be executed from the command line instead of simply clicking on it to execute.
We have created an HTML+JAR polyglot to demonstrate this:
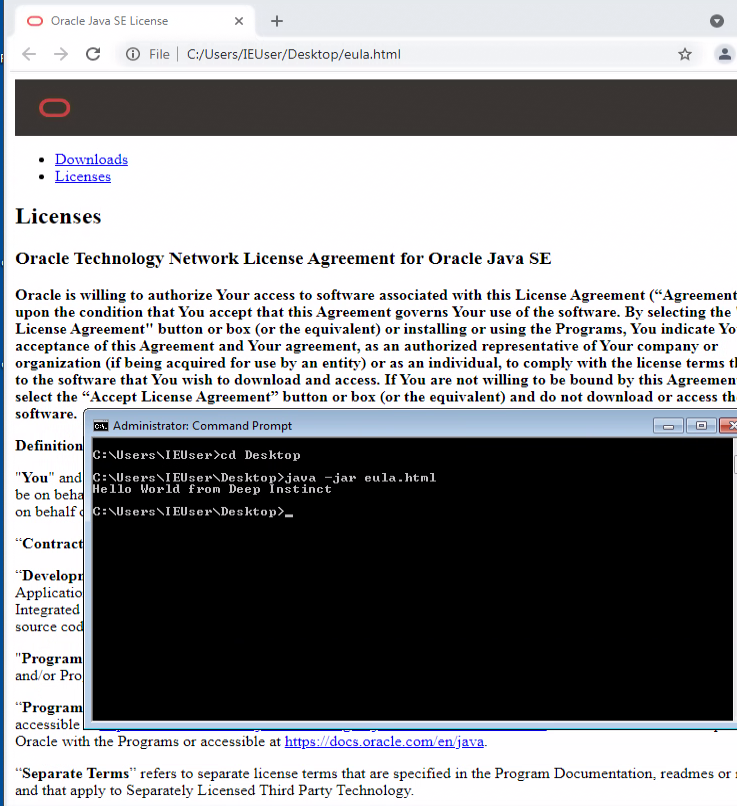
This file is also available in our GitHub along with the Ratty malware configuration extractor.
Conclusion
The proper detection for JAR files should be both static and dynamic. It’s inefficient to scan every file for the presence of an end of central directory record at the end of the file.
Defenders should monitor both “java” and “javaw” processes. If such a process has “-jar” as an argument the filename passed as an argument should be treated as a JAR file regardless of the file extension or the output of the Linux “file” command. Incident responders and the cyber community are welcome to use the Ratty malware configuration parser provided from Deep Instinct in case of infection to get to the IOC fast and quickly move on to remediation steps.
MITRE ATT&CK:
| Tactic | Technique | Description | Observable |
|---|---|---|---|
Initial Access | T1566.002 Phishing: Spearphishing Link | Attackers use URL shortening services that leads to the payload. | Rebrand[.]ly/afjlfvp |
Defense Evasion | T1036.001 Masquerading: Invalid Code Signature | Attackers append a signed MSI file. | 85d8949119dad6215ae0a21261b037af |
Defense Evasion | T1027.001 Obfuscated Files or Information: Binary Padding | Attackers append junk data at the beginning of the file causing “file” command to return a different file type. | cb17f27671c01cd27a6828faaac08239 |
Command and Control | T1102 Web Service | Attackers used Discord's content delivery network (CDN) to deliver malware. | https://cdn[.]discordapp[.]com/attachments/938795529683480586/941658014962823208/Package_info[.]jar |
IOC:
d51d269b62e55d4af8a4bd72dcf3c5115ad27fe5466640041c658c0325194451
534a4b0e17723755dd8cbdcdec309004ef59c3dfacb87fac86da4548780d2f1b
08921a6b0b2903b9c991acb869930c7cab3cbaf11e002be9c88400af48c3fa21
59a02230a78b87c97eebbf7cdba40ea17c7d9411d706fd255c2a6a025584fd9f
a9ac4ae704da346a0f3d2960b084d8f314c0fd60a934116e3c75647c713314b6
47fc7fc1658acfa2f7a0b388bea6b52787f186bf8297ce189a575d547dfbd8e0
a80add76ff8ad0e1c3bdab9459546fd724e1f4034248d1542aec1264c02d3857
f0e57c84ba1958cabf24cfec4a0d50be6b7bc0e45c639d08a53097494373ae9e
e7812ff64dbe51584d3090e008b464510dbb87ac860c68d89e224621755021f9
41ef2dfa736e9a24a1a29a373357ac249dad99f86f1cc0283ddd4765fa14e54a
8d801f58d10dbcd52739fa35aa862286c3fe9606411f0e5f7b8b3fd71f678cad
f79ba296aeab13be409ee3ef435f47a8888f7186a062fa481603ec32f3d6b678
262e6824f0c4c765e73a7041362d7a3a8d63dab1be91ecf5e80623ac6e2f389e
b6a0dcd8c9bc11794837e8f9350e2816ae7a60d148f3e6f436c2645f450feeab
f620c4f59db31c7f63e8fde3016a33b3bfb3934c17874dcfae52ca01e23f14de
54814775c2f266cafe3d4ddc58bc400360aad8cea95e0d3ee74ceceb927cb3b8
2f4c6eb0a307657fb46f4a8f6850842d75c1535a0ed807cd3da6b6678102e571
74c8d5e01e2bb52c6f5cd7863168085ff81bea970b5309ec180c2e1a299096df
f2b36a7df3d0b4d63bbbc529b7a27282e5626300e1353d2596866e4a82165f64
4f00914f63181c0afbfff41a95f5f1364c61d78ffb250ec8ef3102b3d3bd7003
a989289cd6df1b1c38dbda84eb3b286bb8fb7a2af9beb1e55b029dbf861bac83
521a2e7ee2558d83e29bceb68a8c4ea0ecce4bddcb05cc0d3b0365522f126d1f
19154b831614211de667c2aedd6a4b5b89d4bfc1e129eb402a6300ad2e156dcf
e3be7066e6922d7460dea80ca5b7fef8f4abc7b1f056d8f329c03b306e8ca9b0
788f1abb67d6f21cf299e2f67a2b414d169e8ab16cc8a61bf698e5c7f1482999
5e288df18d5f3797079c4962a447509fd4a60e9b76041d0b888bcf32f8197991
0c14d804efe1db9377bfe3d5e06ba37a4817cc4bd0f6404ed7d705219295e815
1056554bca75450d07fcc5df7c1ca4686a2fefbe76cc9fb60343364678ca8744
f2d7e93978c0991e376466810adf18262e4a7fb2864c7a87f22e3fa71adb6519
496251bb063e4ee3769139a34ccfbdd81ba52b004836da7aaabd5e5e67f87478
d00d85589908ba95536822dea356afb5a9148628a7e2207c6e850024c0ba434d
928551a303110983871266af840df71bf7427dcff242688c105f04d4aa87806b
e2d67077cbcab70d47a95b8da25a2a35fe1f1099ed71d8b06f8e78dd741fc2b7
d0703f8f70aff6e3975f3b7c8d037b5a0d3d1b8e4a91b2a6c65227c7932dded5
9e0468a7249fd6bc2b911434b0c7afa2a9d92473e2402a1a3ad357119c579d63
fe72f76f147bce32338a4b0b88c3d59dd3e85406ab1b3b273aab7cb7227fae52
964eceee84de3d0b8b3565100c1e45dab1b4b5ff7c61f03a198a56714c03ca32
d8c04d3a6e6e5058c10a56890a9dcf41ac5e47a22dc1002e89415ee0f37c7f05


