Malicious Office files: 20+ Years of Microsoft Office Exploits
Weaponized Office documents pose a large risk to organizations. From embedded active content, such as scripts and HTML code in Word and PowerPoint files to Excel macros, this is an attack vector every organization must pay attention to. About one million companies worldwide use Office 365 and 70% of Fortune 500 companies purchased O365 in 2020. As a result, nearly every business transaction involving a file transfer will likely be in a Microsoft Office format at risk of containing malware.
Not surprisingly, approximately 80% of all recent malware attacks (Q1-22) involved exploiting MS Office weaknesses (see Figure 1). Office vulnerabilities offer multiple opportunities to hackers, from initial system infection to remote command/code execution, often allowing the attacker to modify system files while remaining undetected. Follina and Trickbot are two recent examples of campaigns that operate by exploiting Office vulnerabilities. More about how these malware families exploit Office files later.
In 2021, Atlas VPN reported that approximately 43% of all malware downloads are malicious Office documents, a 3x increase from only 14% in 2020. The rapid expansion in the exploitation of MS Office flaws is concerning as most endpoint security vendors still focus their prevention efforts only on portable executable (PE) file types and cannot stop unknown malicious Office files from being downloaded and executed. While executable files do pack a punch, it is clear that attackers have shifted their tactics to malicious Office documents where they have the best chance to gain a foothold into an organization’s computing environment.
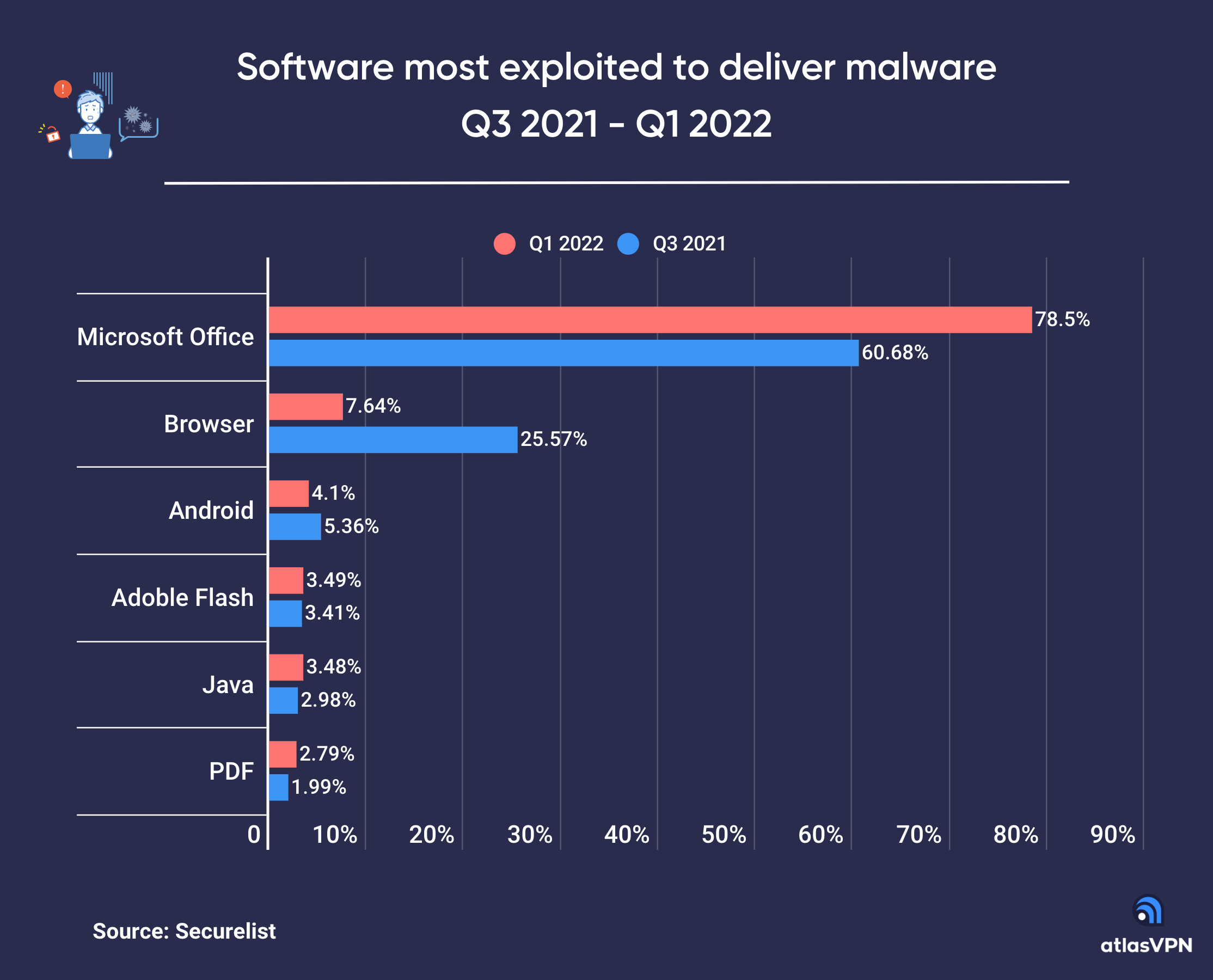
Recent attacks using MS Office flaws
Ever since Microsoft Office and digital documents have been around there have been vulnerabilities to exploit. Over 22 years ago, a vulnerability was discovered that allowed an attacker to successfully insert a Trojan Horse DLL into the same directory as a Microsoft Office 2000 document upon launch: CVE-2000-0854. This vulnerability scored a 10 out of 10, meaning total information disclosure, complete compromise of system integrity, and a total shutdown of the affected resource. Over the last two decades attackers have continuously found new ways to exploit the most widely used productivity suite. Organizations that don’t patch their systems quickly find themselves at significant risk.
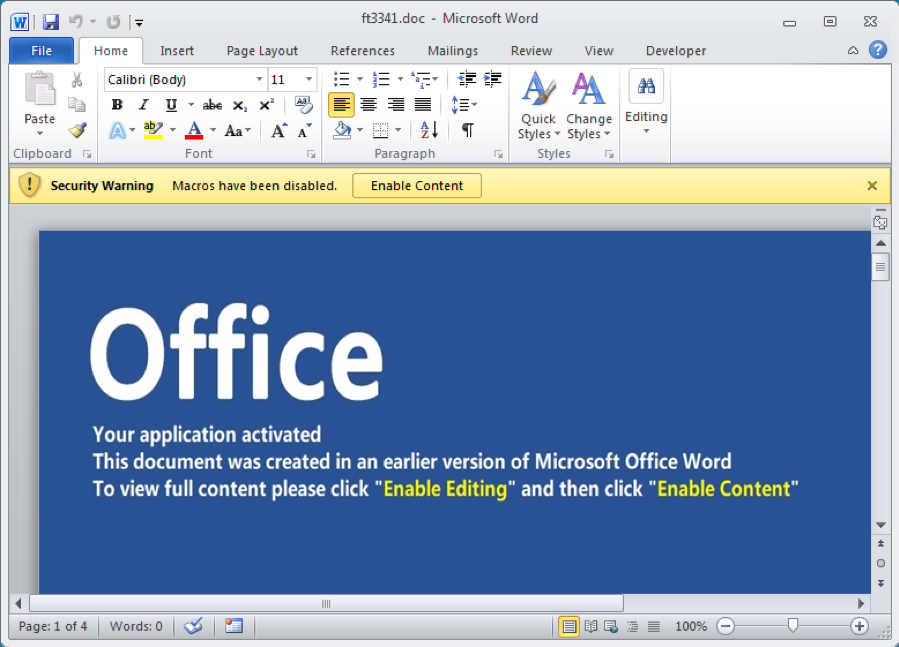
Recently, threat actors have ramped up their exploitation of MS Office files even further, as demonstrated by the recent malware family dubbed Trickbot. Trickbot most often begins its infection with a Word document (see Figure 2) that has embedded VBA code. While VBA code itself is not considered malicious, its presence in a Word document raises a red flag, and this technique is used by numerous attackers across several malware families. The document is written to trick the user into enabling macros (see screenshot below), at which point the VBA module containing malicious JavaScript code downloads the payload and establishes persistence on the system. Because of the amount of system information that Trickbot quickly collects, many other campaigns have been known to use it as an initial infection point.
An even more recent campaign exploiting MS Office vulnerabilities is known as Follina. What makes Follina unique is that it manipulates a bug in the MSDT (Microsoft Support Diagnostic Tool) that allows code execution. MSDT is a tool that is used to collect information about a Windows system and send it to Microsoft Support for investigation. This utility can modify local PowerShell policies to allow execution of code. Follina is executed using an HTML file that calls MSDT and allows it to execute a PowerShell code. In this attack, rather than just sitting by and waiting for users to happen upon a URL with the malicious HTML file, attackers use another technique that involves modifying the relationship file (RELS) within a Microsoft OOXML (*.docx, for example), causing MS Office to automatically open the HTML file that then executes the code.
Other campaigns have turned to obfuscation and padding in their droppers to help their VBA and scripts bypass endpoint security solutions. In the resurrection of the Emotet malware family, attackers disguised their actions by hiding code snippets in random cells within an Excel file, subsequently calling those code snippets from within obfuscated scripts written in different coding languages. You can read more about this example and several others in blogs from Deep Instinct’s Threat Research team.
How can you prevent malicious Office docs?
Microsoft Office and pdf attacks have grown in number and sophistication over the last few years. But what’s even more worrisome is that most endpoint security solutions, especially those in the Endpoint Detection and Response category, are only able to prevent both known and unknown files of the portable executable type, such as EXE and DLL files. Also, most EDR solutions lack static analysis to stop the threat until after the files have been executed and they see the behaviors, which is too late to prevent damage. This is precisely why you need Deep Instinct even if you have an EDR.
The importance of preventing malicious document files before they execute and hit local storage cannot be overstated, especially when it comes to unknown or zero-day attacks hidden in malicious files. In the case of ransomware, crypto-miners, and wipers, they work so fast that post-execution detection is too late. And as we saw with the Trickbot campaign, if the file hits a system, chances are the user will interact with it before an EDR will catch it.
Amidst all this bad news about the rise in exploitation of MS Office flaws there is some good news:
Deep Learning-driven static analysis provides a way to prevent malicious Office documents before they execute or enter storage. By scanning the full content of a file in under 20 milliseconds, Deep Instinct determines that the file is malicious and prevents it before it can write to disk, end up in your public or private cloud storage, or be uploaded through Web applications. Deep Instinct does not rely on known threat intelligence feeds and can stop unknown threats before they are seen in the wild.
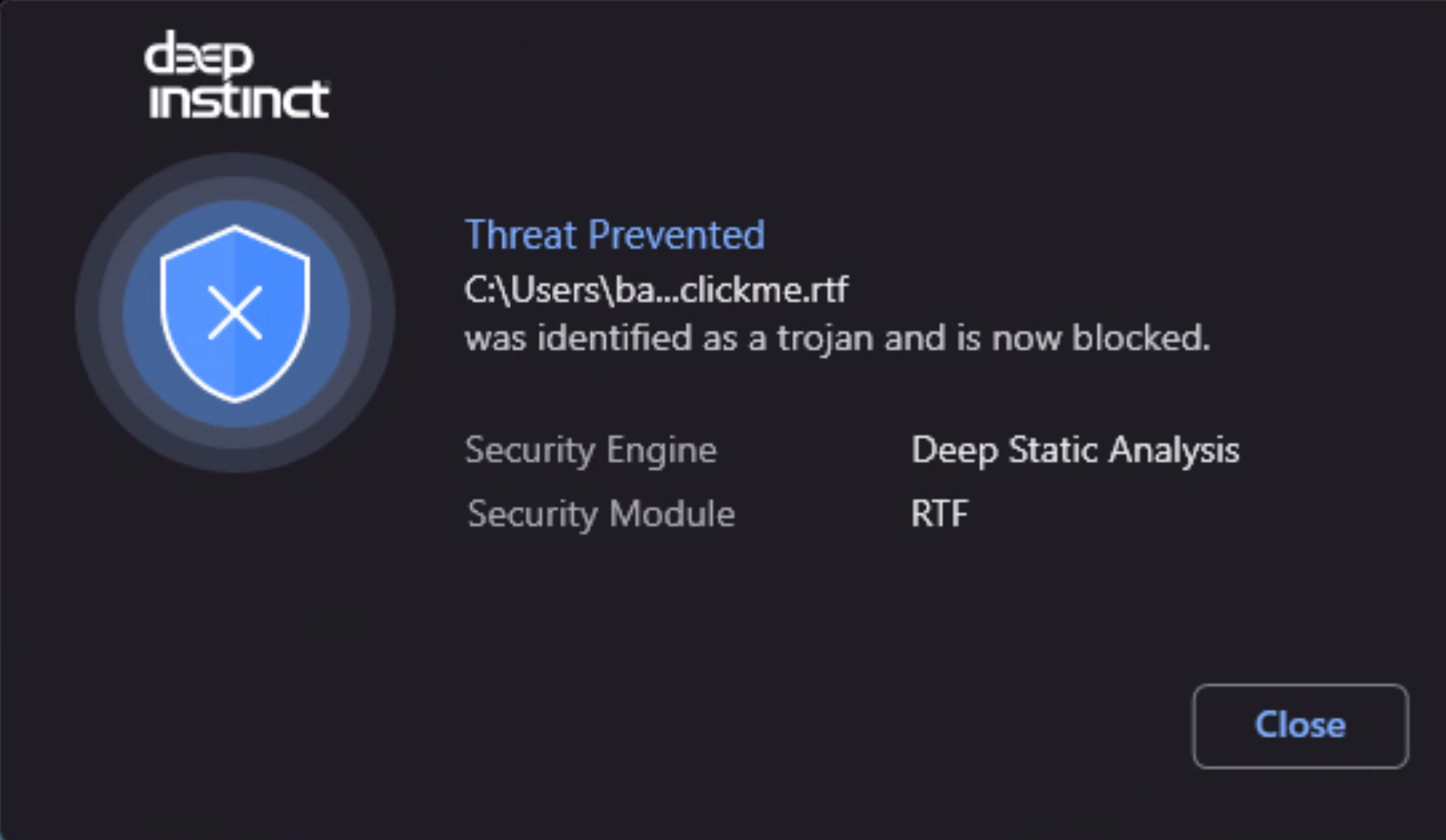
Deep Instinct is the only solution that prevented Follina before anyone knew it existed (see Figure 3 below). We prevent known and unknown malicious attacks hidden in files across all Office modules (such as OLE, OOXML, RELS, XL4, ActiveX, and LNK). With <0.1% false positives, a >99% unknown threat efficacy and a decision in <20 milliseconds, Deep Instinct is providing the enterprise with prevention capabilities to lower risk and focus on what really matters – your business.
If you’d like to learn more about our unknown malware, ransomware, and zero-day prevention capabilities we’d be delighted to give you a demo.
Further reading:
- How your regular microsoft office file is open to manipulation
- Unfolding the Follina zero-day vulnerability
- 8 reasons EDR is not enough
- Types of dropper malware in Microsoft Office
Resources :
- Malicious Office flaws exploited in nearly 80% of malware attacks
- New Variant of Trickbot Being Spread by Word Document

