Info-Stealer FormBook continues activity using a new file hosting service
By: blt786b6230d0ad1dfa
Background
FormBook is an info-stealer which first appeared on the scene as early as 2016. This malware has been marketed in underground hacking forums as having elaborate evasion capabilities and a powerful credential harvesting mechanism at a relatively low price. Since its creation FormBook has been widely used in malicious spam campaigns to infect victims and steal their credentials in multiple attack waves.
In the last days FormBook has been reported as having an uptick in its activity. As part of the recent wave of attacks, Deep Instinct prevented Formbook attacks targeting customers in the retail and hospitality sectors in North-America. However, threat intelligence suggests the campaign is not limited to that geography.
Analysis of a recent sample from this attack led to the discovery of a new malware-friendly file hosting service, used by threat actors as a point of distribution for their malware, something which is naturally frowned upon by legitimate file hosting/sharing providers. These types of services vary widely in their quality and their ability to remain active over long periods of time and be used repeatedly by multiple threat actors. Therefore, we’re happy to shed light on what we believe to be a new malware hosting service that could be used in other campaigns as well.
Infection Chain
As with many information stealing and credential harvesting malware, FormBook’s infection chain starts with a phishing Email containing a malicious attachment, which is usually an Office document or a PDF file.
In this specific attack wave, initial infection is carried out by means of a malicious RTF document, which exploits several vulnerabilities in Microsoft Office (CVE-2012-0158 – Office ActiveX Vulnerability, CVE-2017-11882 – the popular Equation Editor Vulnerability).
Once a victim opens the malicious RTF, and the exploit chain is carried out, Office’s equation editor (EQNEDT32.exe) will contact a bit.ly short URL (most likely used for URL filtering evasion purposes) and obtain a redirection to the actual malware payload to be dropped onto the victim machine in the user’s root directory \%USERPROFILE%\3.exe
[caption id="attachment_4137" align="aligncenter" width="1800"]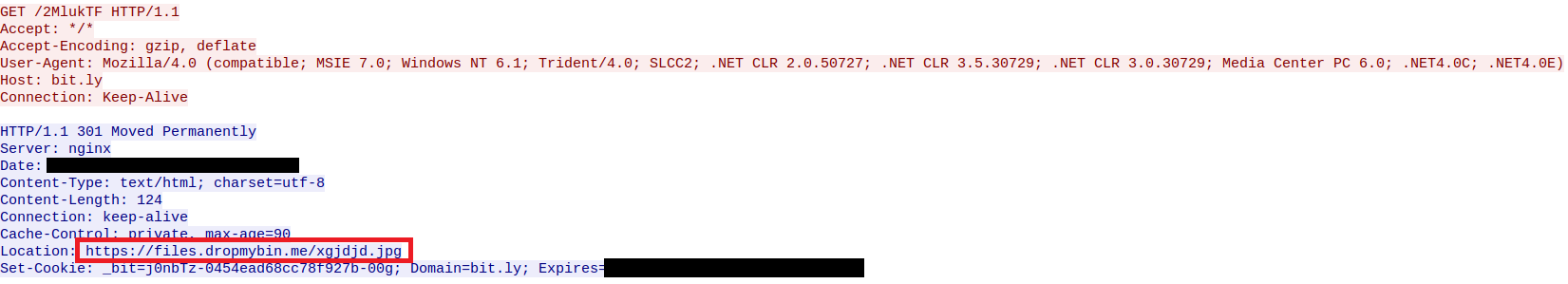 Redirection to the malware hosting service storing the malware payload, while the redirection may appear to be redirecting to an image, this is just a renamed executable file.[/caption]
Redirection to the malware hosting service storing the malware payload, while the redirection may appear to be redirecting to an image, this is just a renamed executable file.[/caption]
Once this payload is dropped and executed by EQNEDT32.exe, it will copy itself to \%APPDATA%\Roaming\<5-letter-string>\tysogn.exe and write an auto-run entry in the registry at HK_CU\Software\Microsoft\Windows\CurrentVersion\Run\ thereby achieving persistence and boot-survival on the infected machine.
FormBook will then proceed in its main task – steal as much information as possible with a focus on access to accounts, user names and passwords. It will scan the system for stored passwords in browsers and various other applications such as Email and FTP applications that may be installed on the machine. FormBook will send the stolen information back to its C2 server. It will also take a screenshot of the victim’s desktop and upload those to its C2, along with monitoring all browsers for user-typed passwords which it will grab as well. It will also act as a keylogger and maintain a log of the user’s keystrokes.
DropMyBin – A new Malware-Friendly Hosting Service
During the analysis of this attack, the domain from which the malicious payload was dropped (files.dropmybin[.]me) immediately caught our eye, and sent us crawling through known cybercrime forums where we found the following post, which was active only several days ago:
[caption id="attachment_4139" align="alignnone" width="1880"]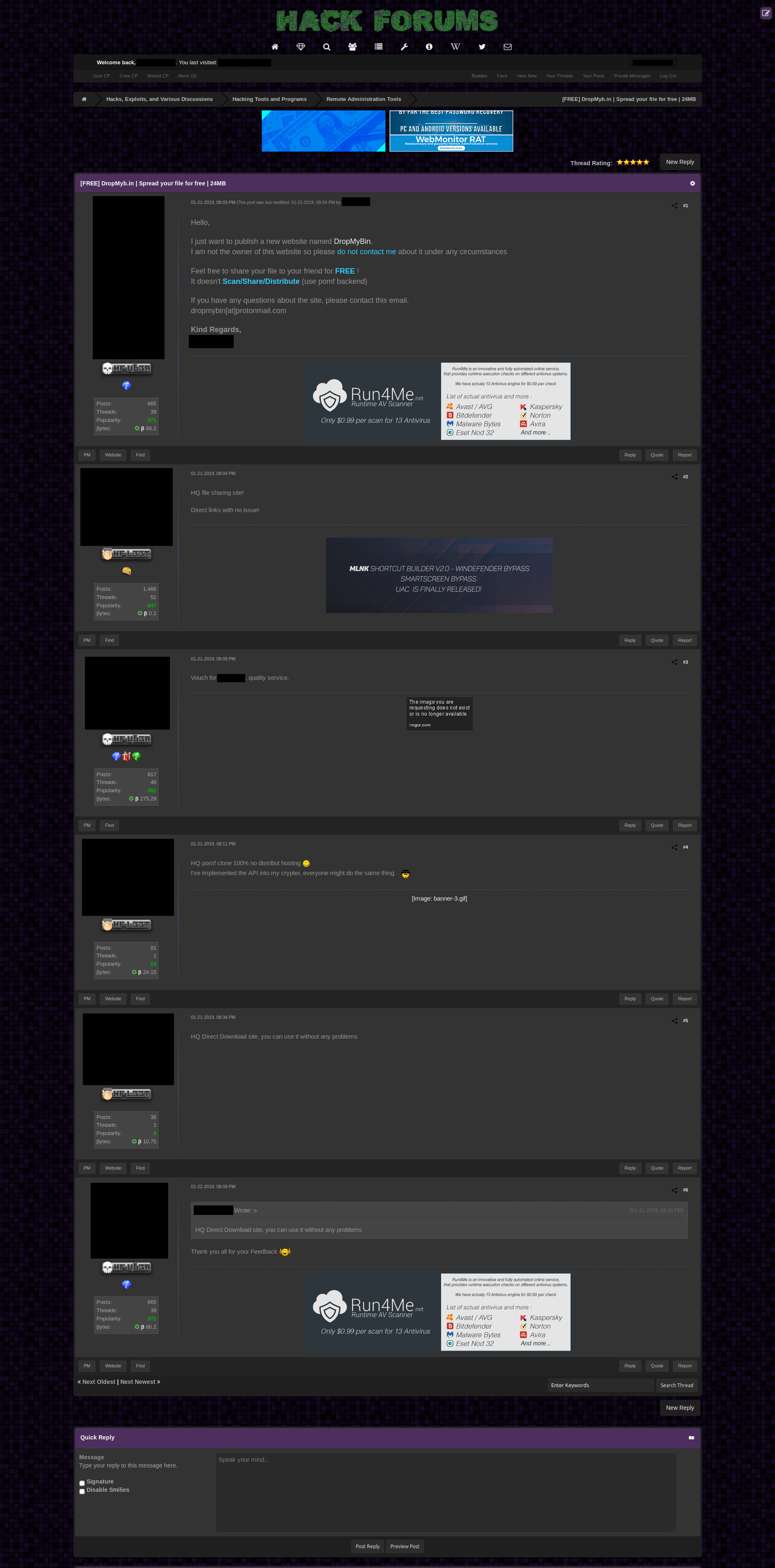 Known cybercrime forum post advertising the new service[/caption]
Known cybercrime forum post advertising the new service[/caption]
This discovery led us to investigate the mentioned domain and service, and while the “advertised service” website’s domain is dropmyb[.]in and not dropmybin[.]me, uploading a file dropmyb[.]in clearly reveals the connection when the uploader is provided with a link to his file on files.dropmybin[.]me.
[caption id="attachment_4136" align="aligncenter" width="601"] Following upload to dropmyb[.]in the uploader is provided with a link to the file on files[.]dropmybin[.]me[/caption]Both dropmyb[.]in and dropmybin[.]me have been registered on Jan. 17th and Jan. 19th respectively, and both employ Cloudflare, a reverse-proxy provider whose services are quite popular with various threat actors, to hide their real IP addresses from the world. Both have been documented recently by various threat trackers as being sources of malware infection.
Following upload to dropmyb[.]in the uploader is provided with a link to the file on files[.]dropmybin[.]me[/caption]Both dropmyb[.]in and dropmybin[.]me have been registered on Jan. 17th and Jan. 19th respectively, and both employ Cloudflare, a reverse-proxy provider whose services are quite popular with various threat actors, to hide their real IP addresses from the world. Both have been documented recently by various threat trackers as being sources of malware infection.
A particular point of interest arises when one examines DropMyBin’s FAQ page, which seems to hint that this “File sharing” service is operated by individuals based in Russia, and while the page declares no malware should be uploaded it clearly states that all abuse claims should be made to “appropriate law enforcement agency” as the operators are not qualified or trained to investigate and fight crimes. Seems like an invitation to upload and direct traffic to whatever one likes to…
[caption id="attachment_4138" align="aligncenter" width="674"]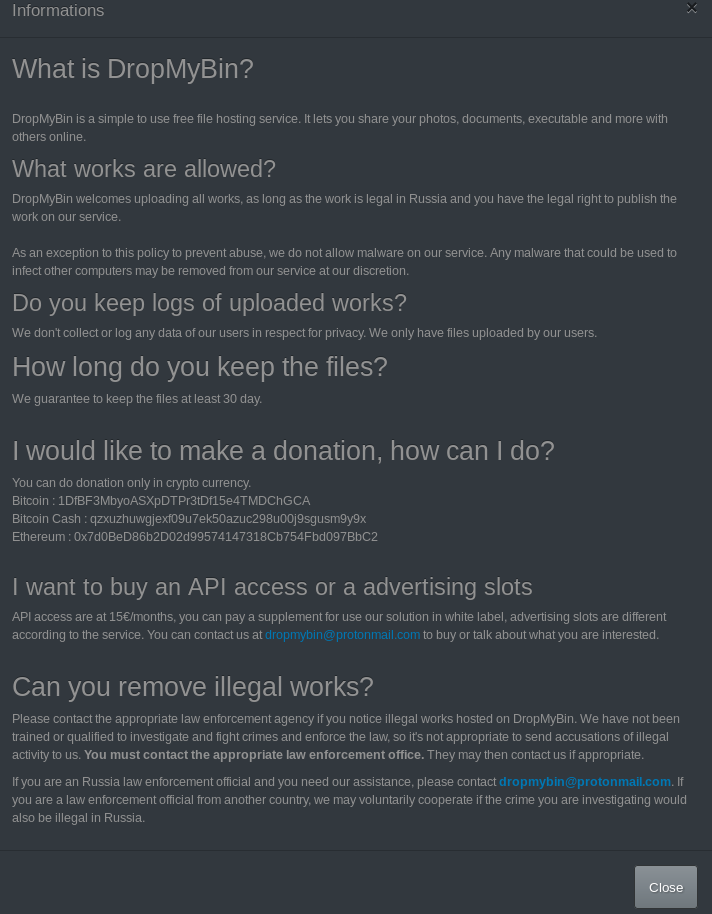 DropMyBin’s “terms and conditions”[/caption]
DropMyBin’s “terms and conditions”[/caption]
Our analysis indicated that various other families of spyware active these days, such as Lokibot and Azorult, have already, in a matter of days, been hosted on the service. Relevant indicators of compromise can be found in the “Additional IOCs” section.
Summary
FormBook, with its extensive collection and harvesting capabilities, is back in the game. This time around, it’s using a new malware-friendly file hosting services, which seems to be quickly gaining popularity among other threat actors. We strongly suggest employing a zero-trust policy with respect to the service DropMyBin until other information becomes available. Additionally, some of the droppers and payloads are not detected by a big number of security solutions out there, hence we’ve provided a list of all IOC’s currently available to us.
All discovered droppers and payloads are prevented by Deep Instinct’s advanced Deep Learning based solution.
IOCs
Analyzed samples:
RTF dropper
250da840ed2aa9fafc9c5f965cf5a131c5174795aebcbbc9d797673dac3b82fb
FormBook Payload
9af641d8fc43962b33e92f1bbdb49de9cf4066cccdcad07d6d4d7ffe7a2b877b
Malware Hosting Service:
dropmyb[.]in
files.dropmybin[.]me
FormBook C2 infrastructure
r2dummy[.]info
yatekipu[.]site
xcpcfw[.]com
timbaleepoxy[.]com
review-ih4ewkr0m5aqxl[.]cricket
thelan[.]win
ajexin[.]com
zdhuanka[.]com
ra-design[.]net
Additional hashes:
Droppers
44ad6c65a84c066ec80e62a80d1284afab726b5e71b5acafc431906ce3023011
f4a64a42023927de5763b41fc4db110d797b0b73d5532a03d2af1ba4c495941b
25283433c17c8160a0f9c11617ee7ed82c9e9b3f87f289ce2b1780547f02dc29
df1beec0b2ed0dbe4665e5c54126b18ff449e901a149b5102b9c2b9d0fb99c26
348bc9251aa7412574da3149f3f75c14acf6bbaabf4004936a46252174d310ec
86c1f9a5a98390ea5a565478bc596224cdc5805ed5b88a18b7898f8f88d08658
6620382b76f0ee7e2fdd3c85c96c2d43579d43b3febbd7e0b244a982b7c69961
058881724b98f5086824bb8db6e3d6e989026e87d3527471e4abbe6a326673fa
Payloads
9bbd0ef317cc49aecbb4ff4ada88ebbf4c68dd96be299e6a8cf46f8360c9f26f
d3e96fd2f8f0308c1b06de9f2ec16552e4979486c1c67c0de8a76f72e80adaf4
1b657370607457536ef4eb685247adf5fdc396b5cad2baa8c1c57e798c003ac8
4da0992ea55707cc077ecfeab1a7b5d6d0f59b2490548ec71bd412b022f02859
4233e00cb24d05df399a9f025940cc0fc46c413ede4498213f0bc97b2f7598fc
f5666f44902136f7e437ac789f7b1d734a63e9c9d3d06de77db6a5335a63b93e
0646054db76101edc9c06901564c7d8f39db228270e5cd83f53719b90dc6c308
81b02610374727061fbe673d832b177bd8de0ed05e8f8bfee12a3348317bffce
90959ae72468c4b656f4cac46202eb6629c4288e438f6c0733afa9bead4639ed
1f955a71dd6d9c82e252fb3501b13f196f5c0bf37c948853b261a9833f344888
d59b6c9d57ef1e877f47e8d8d3f8057dba7f2cf3a25ea3fe436e283823e1ef0a
988ff849e13ed0ca9ca8a6e4c5eae27f59fd54db2a75af7905550488e2158feb
5e4bbfd0a0ec4ad115e955ddc0219d0fdda191c9f95c3dadce2af567d9483fa8
0bb22d8dd0ff06495e0da807e3b07e533c3d0f4878c6431cc7eec1bbcafedf51
da5e2a2084ea1d84ab7667d326b76277512a702d0d7bb83902bb19b8384dc5ec
1b1367f8db929f1c9422f792f0e58bae10b9afb85aa2e630303dbc7d5e67cfcc
a9a1145cef577d5a31fca756fc6146ded5ad0c428cdc5a1557504b2cb33c145d
fe1061465bfd7d0af69bd26bbcd2ee1bac6f1ea455e25e0aad4af0004850b355
f31bded1dfdb851824a3316334618b6438fde46b3b9cdf532ed61343a6b55089
d690f2b9e8d1df3657fc609f4c6163659117f6ded10df006f9b4c90370246957
f937c2b3020f753ca5152bbde8f85db687434220144f9d372cefbdcf4519464a
468c50e0e09f85a3c79e8cb5c74863e52ff3482eb2f01904727572795aad8ec4
a5e744b416a2b5a66ed47b7654bafd051de4c7070c85b37e0bb303e384e378a8
94754ff3f59ea0cc91c8d7e6461867731a2dce1d3272c908bcc597a7a068935f
0994276d493fe85c0750f3da810275fb705206b55c8013be2162a621f2d4dacb
624940ea7bd17a935a75b7fdd79f45d2eb6b3870627a65f9e4315603350d61ef
01f42686bc9942d3863916d46226d5f958e1d01ab93b1d6cc35bf622aeae4a67
f597ff18004f193f7057b9ea45177454fb069d054ca52ba9aa2f555fbd75eddc
b7d57a7f26b49ae4c4ee25febb9f970a1d793fa4cb094f462f09a842e57642aa
d6726c0432d92c2051fc48c69a16add3ca2fedf9ea730417938001533447e2c7
78b71957661b5db92ecbcff2473758f4a4df511f344a6e55c1b5534758b5dd87
5d9d268900a160f44c4aee3554f34bc4efeaa8366a82f5ff5f24e5aaaef8abbe
ec98bf5b2a85e871d1a159bdf563175999f426c2be5d51510af86401915030f1
80154787452c2e2114e84e2933e18d78b4988fb7756c5f5f27a7120b674d6e6e

