Jedi Mind Tricks to Bypass Endpoint Detection & Response (EDR)
In Star Wars Episode IV, Obi Wan used his “Jedi mind tricks” to fool storm troopers into allowing Luke and him to pass through the security checkpoint with R2-D2 and C3P0 undetected – even though they were in fact the droids they were looking for.
Much in the same way, savvy cyber criminals have developed their own set of “Jedi mind tricks” to fool many security tools – EDR solutions included – into looking the other way while malicious shellcodes sneak past undetected. Bypass techniques are increasingly used by attackers to avoid detection while they do their damage.
This post will explore different evasion methods and propose ways to protect against them to ensure the attackers don’t land inside your environment.
Three Methods Attackers Use to Bypass EDR
Below are three ways that attackers can bypass EDR solutions: AMSI bypass, unhooking, and reflective DLL loading. Read more about each method and learn how Deep Instinct helps prevent these EDR bypass techniques.
1. AMSI bypass
AMSI (Anti-Malware Scan Interface) is Microsoft’s framework that allows third-party anti-malware solutions to have visibility into Microsoft components and applications, such as PowerShell, script engines, .NET framework, and WMI. EDR solutions use this framework to scan files, memory, and/or streams for malicious payloads.
Because these are the toolkits that cyber criminals frequently use in crafting attacks against Windows devices, it makes sense that the more advanced attackers would find ways around AMSI in order to be successful.
There are several different methods attackers may use to bypass AMSI, such as reflection, COM server hijacking, and memory patching. An example of a recent attack using AMSI bypass methods is the Agent Tesla remote access trojan (RAT) that used the memory patching method to avoid detection of its stage-2 loader and final payload.
How do you prevent AMSI bypass methods?
This all sounds like pretty scary stuff, right? The very interface that Microsoft created to enable endpoint security to not be evaded is now being evaded itself.
Deep Instinct prevents AMSI bypass methods using in-memory protection that terminates any process attempting to subvert AMSI. For a more detailed look into AMSI bypass methods and security tool responses, check out the slides from our Black Hat session, AMSI Unchained.
2. Unhooking
To understand the unhooking technique, you must have a base understanding of what “hooking” is. APIs (application programming interfaces) are the interface by which code is used to make things happen on a computer system. Windows has a set of APIs (such as syscall) that can be called to execute instructions that require direct system or kernel-level access. As stated in the previous attack method, most EDR solutions use the gateway ntdll.dll by “hooking” into it to watch for suspicious calls to memory.
Unhooking refers to a method that attackers can use to load a fresh, unhooked version of ntdll.dll AFTER Windows has already loaded the EDR-hooked version at process launch. At this point the EDR is flying blind to any code that is running and it is unable to monitor the return address for any API calls made, rendering it useless. A thorough hacker will go so far as to “re-hook” the EDR at the end of his operation to cover their tracks. You can read more about how unhooking works in this “red team” article about bypassing EDR to dump credentials.
What can we do to prevent unhooking?
Just as with direct system calls, the unhooking method attempts to evade detection by preventing an EDR from doing its job. Deep Instinct addresses this issue by preventing modification of our agent’s hooks by monitoring for changes to those memory regions. Any attempts to access these memory areas are deemed malicious and will be prevented.
3. Reflective DLL loading
Reflective DLL loading is a Remote Code Injection technique by which an attacker will load a DLL from memory into an existing process instead of loading it from disk. EDR solutions generally protect a system by monitoring DLLs as they’re loaded from disk, so reflective DLL loading provides another way to work silently under the EDR’s radar. This method is often used in conjunction with one or more of the other techniques we’ve already discussed and it is used heavily in the Cobalt Strike and Metasploit frameworks that are a big part of the modern attacker’s toolkit.
Is there any way to stop an attacker from using reflective DLLs?
Deep Instinct provides protection against this technique by monitoring allocation of local memory areas used in reflective DLL loading and preventing PE (portable executable) loading attempts from those memory areas. Figure 2 shows an example of Deep Instinct preventing this type of attack.
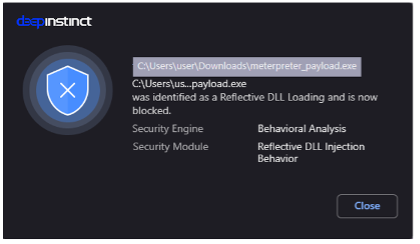
What does this mean for EDR?
We’ve seen just a few of the many ways that threat actors with the right toolkits – which are easy to find and implement even for the less sophisticated hacker – can bypass even the most advanced EDR protections. That’s because EDR’s strength lies in detecting malicious behavior after the threat has landed in your environment, which is too late to stop advanced attacks like ransomware.
We aren’t advising you drop your EDR – we are advocating for improving prevention. Prevention needs to be the first line of defense to stop known, unknown, ransomware, and zero-day threats. While EDR solutions are great at identifying known malicious threats and activity to identify an attack while it attempts to steal data and do damage, there is a big gap in true prevention to stop unknown threats before they can land on an endpoint, server, or enter storage.
We are at an inflection point where attackers are becoming increasingly adept at bypassing the security controls put in place. EDR is not enough to stop the most advanced threats. Advances in AI and solutions that employ deep learning are providing us with the armor to guard against these “Jedi mind tricks,” preventing unknown malware, ransomware, and zero-day threats from executing in your environment. Stopping these advanced threats before they can encrypt, exfiltrate, or achieve persistence offers the protection organizations need in an increasingly complex and harmful threat environment. The result is lower risk, improved SOC efficiency, and increased overall effectiveness of your entire security stack.
Don’t let attackers bypass your EDR. For more information, Contact Us or Request a Demo.
Further Reading:
- https://www.deepinstinct.com/blog/8-reasons-why-edr-is-not-enough
- https://www.deepinstinct.com/blog/evading-antivirus-detection-with-inline-hooks
- https://www.deepinstinct.com/blog/cobalt-strike-post-exploitation-attackers-toolkit
References
Agent Tesla Trojan ‘Kneecaps’ Microsoft’s Anti-Malware Interface
https://threatpost.com/agent-tesla-microsoft-asmi/163581/
A new BluStealer Loader Uses Direct Syscalls to Evade EDRs
https://blog.minerva-labs.com/a-new-blustealer-loader-uses-direct-syscalls-to-evade-edrs
BluStealer Malware Targets Cookies, Passwords, and Cryptocurrency Wallets
https://www.cyclonis.com/bluestealer-malware-targets-cookies-passwords-cryptocurrency-wallets/
Bypassing Cylance and other AVs/EDRs by Unhooking Windows APIs
https://www.ired.team/offensive-security/defense-evasion/bypassing-cylance-and-other-avs-edrs-by-unhooking-windows-apis
Cobalt Strike 4.4: The One with the Reconnect Button
https://www.cobaltstrike.com/blog/cobalt-strike-4-4-the-one-with-the-reconnect-button/
DLL Injection
https://pentestlab.blog/2017/04/04/dll-injection/

