In this blog, we dig into the results from our new study of 500 U.S. IT professionals, which clearly highlights that IT professionals, especially in management positions, don’t realize just how quickly the new AI-driven threat landscape is shifting beneath their feet.
AI Threats Are Growing Faster Than Defenders Think
Our study found that 64% of IT professionals believe fewer than one million pieces of AI-generated malware are created each day. Public statistics reveal that more than half a million new malware variants are detected daily. The key word: detected. That number reflects only what legacy tools manage to catch. In reality, the daily volume is likely 10x higher, or more. And the more we examined the data, the more concerning the picture became.
When Deep Instinct threat analyst Brian Black put legacy tools to the test using AI-generated malware, 65 of 73 failed to detect it, a staggering 89% miss rate. If similar patterns hold in production environments, the true daily volume of unseen malware could easily exceed 5M variants.
Rather than treat that miss rate as a hard indicator of global malware volume, we frame it as a thought experiment, a way to illustrate just how dramatically detection-based systems can undercount what’s really happening in the wild. And it raises uncomfortable “what ifs.” What if legacy tools are only catching the easiest-to-spot threats (i.e., signature-based)? What if the truly damaging malware is the most evasive? And ultimately, the volume matters because undetected threats compound: as the pool of unseen malware grows, so does the likelihood that a single breach will have catastrophic consequences.
As attackers continue automating malware generation with AI, the true scale of the threat is almost certainly orders of magnitude larger than public detection numbers suggest. What we can confidently say is this: threats are accelerating, legacy tools are buckling, and defenders do not realize how far behind they are.
Legacy Systems Are Failing in the Face of AI
This growing threat is concerning on its own, but our study revealed an even deeper issue: confidence in outdated defenses remains insanely high, both literally and figuratively, even as their effectiveness declines.
Real-world data reinforces this disconnect. According to the Identity Theft Resource Center’s H1 2025 Data Breach Report, there were 1,732 publicly reported data compromises in the first half of the year, continuing an upward trend that shows how frequently attackers are bypassing legacy security controls. Breaches are rising while confidence remains high, underscoring a widening gap between perception and reality.
Here is what we found:
- Overall confidence remains high: 86% of IT professionals believe their existing tools can stop AI-generated malware pre-execution.
- A generational confidence curve reinforces the trend: 82% of Baby Boomers, 84% of Gen X, 87% of Millennials, and 90% of Gen Z believe their technologies can stop AI-generated threats. The differences are subtle, but the trend is clear: confidence steadily rises in younger cohorts – yet even the least confident generation reports optimism that far outpaces the real-world performance of legacy defenses. The risk is not that one generation is overconfident; it is that every generation is.
- Seniority strongly influences confidence: Directors and above are nearly twice as likely as frontline staff to be very confident their organization can stop malware attacks (42% vs. 24%).
This overconfidence is dangerous. Confidence in legacy cyber tools leads organizations to complacency as they continue to fund defenses that quietly fail, giving attackers the advantage and leaving security teams to fight blind.
FinServ: The Historical Leader Now Falling Behind
For decades, the finance services industry has been at the bleeding edge of cybersecurity – navigating a business environment where risk evaluation is uncompromising, controls are mature, and security spend is nonnegotiable.
But our new data tells a different story:
- Only 26% of IT professionals in the finance industry feel very confident in stopping AI-generated attacks pre-execution – the lowest among major industries.
- Meanwhile, tech and software show the highest confidence (46% very confident), despite operating in some of the most rapidly changing and highly targeted environments.
Finance’s pullback should be a clear warning to all other industries. The sector’s declining confidence is not theoretical. Recent attacks, such as the breach at financial services vendor SitusAMC, which exposed sensitive data tied to major banks, show how even well-defended institutions remain vulnerable when third-party systems rely on outdated models.
If the most sophisticated and well-resourced sector – the one built on risk modeling and paranoia – is losing confidence, it signals a broader unraveling underway, and the outlook for other industries is alarming.
Healthcare, for instance, is already struggling to keep pace. Its attack surface is large, porous, aging, and expanding faster than security leaders can reinforce it. Healthcare environments remain deeply dependent on legacy infrastructure, fragmented systems, and outdated tech and vendor stacks. Within the last year, more than 500 healthcare breaches were reported. Their attack surfaces are sprawling, their budgets are strained, and modernization is routinely slowed by regulatory complexity and technical misalignment.
If finance is signaling concern, healthcare is already on the front lines. And as both sectors face growing pressure, organizations across every industry are accelerating their AI adoption to keep up, often moving faster than their strategies can support.
The Paradox: Too Slow. Too Fast. Never Strategic Enough.
Organizations across industries are racing to adopt AI technologies to stay competitive, innovate quickly, and keep pace with a rapidly shifting threat landscape. According to our survey, 45% consider themselves early adopters or fast followers (20% early adopters; 25% fast followers).
But being the first or fastest to adopt new technology is not a strategy. Speed without direction is how organizations drive straight into the risks they’re trying to outrun. In the rush to modernize, many organizations default to large, familiar security vendors. Not because these vendors offer the strongest protection, but because they appear to be the safest choice. This creates the most dangerous inversion of all.
The faster organizations move, the more likely they are to adopt tools that still rely on outdated detection models, leaving them more vulnerable even as they lower their guard.
Closing the Gap: Why Deep Learning is the Only Path Forward
Traditional security models built on signatures, heuristics, and legacy machine learning models weren’t designed for today’s modern threats. Malware mutates in seconds, AI-generated variants bypass static logic instantly, and attackers automate creativity at a scale defenders cannot match. Detection-based systems simply cannot keep up.
Deep learning changes that equation by enabling true preemptive data security. It operates at machine speed, identifies never-before-seen threats before execution, and delivers consistent outcomes that give leaders and practitioners a clear view of their real readiness. In an environment defined by rapid mutation and automation, preemptive protection is no longer optional. It is the only viable path forward.
Our research illustrates just how urgent this shift has become. In another recent blog, we detailed Nimbus Manticore, a sophisticated, AI-engineered malware strain that bypassed every legacy on VirusTotal, except for Deep Instinct – for a full week. Discoveries like this highlight a growing and dangerous reality: attackers are advancing faster than detection-based defenses can respond, leaving organizations exposed to threats they never even see.
In 2026 and beyond, the organizations that endure will be those that proactively confront the gap between perception and reality and move beyond legacy detection models that attackers already know how to evade. Achieving real preparedness will require leaders to retire outdated assumptions and adopt deep learning-native approaches built for the speed, scale, and sophistication of modern threats.
Finance’s caution is a warning. Healthcare’s exposure is a preview. And the broader industry’s naive optimism is a dangerous miscalculation. As millions of AI-generated malware variants rewrite the rules of cyber defense each day, survival will depend on a willingness to rebuild security strategies from the foundation up through a preemptive lens.
]]>This time, we're looking at a piece of malware called Nimbus Manticore, and I'll say this upfront—whoever named this malware has a flair for the dramatic. The capabilities, though? All business. Nimbus Manticore represents a serious challenge for organizations because it's not just designed to compromise a single endpoint. It's built to move laterally through your network, escalate privileges, and establish a persistent presence across multiple systems.
Nimbus Manticore caught our attention due to its methodical approach to system compromise. This isn't some amateur smash-and-grab malware. It's calculated, patient, and designed to maximize damage while minimizing detection, all of which should be expected from an Iranian-backed group.
The Malware: Nimbus Manticore
Nimbus Manticore is a 64-bit PE binary compiled using Microsoft Visual C/C++ and the Microsoft Linker, completely legitimate tools that are commonly used in enterprise software development. That's intentional. By using these standard development tools and techniques, Manticore can more easily integrate into normal enterprise environments where compiled binaries are everywhere.
Technical analysis reveals multiple layers of obfuscation designed to frustrate both automated and manual analysis. The .text section shows abnormal entropy levels, indicating encoded or compressed code. Meanwhile, the .data section exhibits high entropy consistent with encryption. Translation: the malware authors really didn't want anyone peeking under the hood.
What really sets Nimbus Manticore apart, though (and what makes it so dangerous), is its focus on privilege escalation as it moves through your network. This malware isn't content to sit on a single compromised machine. It wants to spread, gain administrative access, and position itself for maximum impact across your infrastructure. It’s a poison pill for the sprawl of the enterprise.
Capabilities
The capability profile here is concerning because it checks almost every box on the "advanced persistent threat" checklist. Let's break down what this malware can actually do once it gains access to your environment.
First, the import analysis reveals functions commonly associated with import hiding—specifically GetProcAddress, LoadLibraryA, and LoadLibraryExW. These functions allow the malware to dynamically load additional components at runtime, keeping its full functionality hidden from static analysis tools. Think of it as malware that assembles itself after arrival to avoid detection.
The sandbox detection capabilities are worth noting. Strings like GetSystemTimeAsFileTime, QueryPerformanceCounter, and Sleep indicate the malware can measure execution timing to identify analysis environments. If it detects a sandbox, it can simply refuse to execute its malicious payload, making it appear benign to automated security systems.
We also identified suspicious components, such as "unbcl-new6.dll"—a library that doesn't correspond to any legitimate Windows component. This is likely a malicious module that gets loaded dynamically to perform specific attack functions.
Process and thread creation capabilities are present, evidenced by strings related to "Process," "Thread," and "Start." This means the malware can spawn additional processes or threads to execute payloads, potentially using legitimate system processes as cover for malicious activities.
But, here's something really interesting: the focus on RPC (Remote Procedure Call) functionality. Strings like RpcAuthIdentityFree, RpcBindingSetAut, and RpcImpersonateClient indicate this malware has capabilities for lateral movement and privilege escalation. RPC functions are how Windows systems communicate across networks, and they're also how attackers move from one compromised machine to another. The ability to impersonate clients through RPC means Nimbus Manticore can potentially assume the identity of legitimate users or services to gain access to additional systems.
Timeline
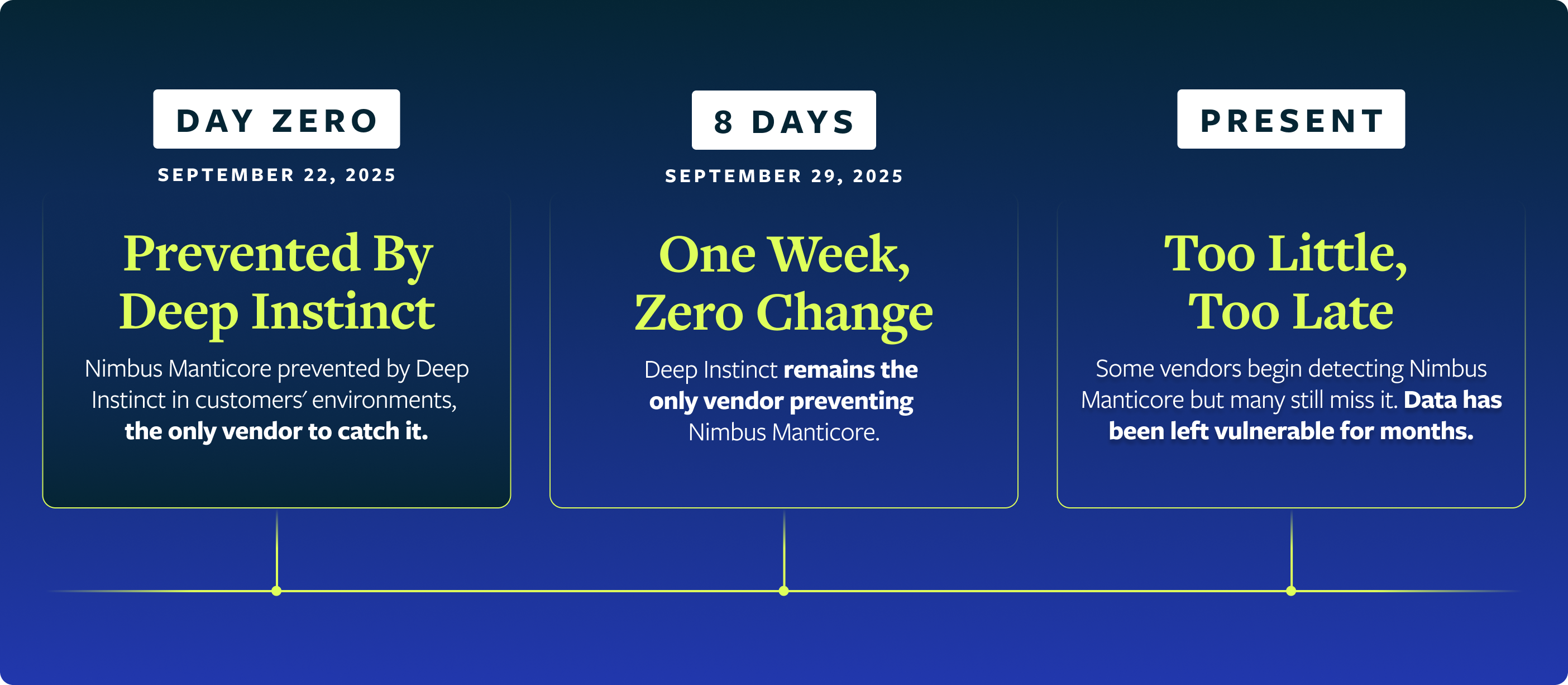
This timeline is particularly alarming for one specific reason: even a full week after the initial attack, Deep Instinct was the only vendor on VirusTotal that successfully detected and prevented Nimbus Manticore. That's not a gap of hours or even days—that's an entire week where the vast majority of security solutions completely missed a threat.
The gap between our detection and industry recognition is significant. Nimbus Manticore moves quickly and an attack on a single machine is already costly. Given a full week? That's enough time for this malware to compromise an entire enterprise’s infrastructure. Early detection is about more than stopping one infection; it’s necessary to prevent a full-scale network compromise.
Competitive Differences
The fact that Deep Instinct was the only vendor on VirusTotal that caught Nimbus Manticore (even a week after the attack) should be a wake-up call for organizations relying on legacy security tools. And, yes, that includes “modern” Endpoint Detection and Response (EDR), which is not enough. This isn't a slight detection delay. It’s a fundamental failure of most legacy security tools to identify a serious network threat.
Nimbus Manticore exposes some significant weaknesses in endpoint-focused security strategies. EDR has been the target of heavy investment over the last few years, with a not-insignificant number of organizations building their portfolio around EDR capabilities. Unfortunately for them, this malware is designed to bypass the EDR and then exploit the gaps between endpoints—the network communication, the RPC calls, the lateral movement that happens between systems.
The multiple layers of obfuscation present challenges for signature-based detection. Between the encoded .text section, encrypted .data section, and dynamic component loading, there's very little static signature to detect. Legacy antivirus tools would also miss this entirely, needing to see this exact variant before they could identify it. Apparently, most of them still hadn't seen it a week later.
Perhaps most concerning are the sandbox evasion capabilities, which create problems for behavioral analysis systems that rely on automated execution environments. When malware can detect analysis environments and refuse to execute in them, security vendors struggle to catch the threat, let alone understand what it actually does. That analysis gap translates directly into detection gaps, which, in this case, lasted for days.
The ability to bypass EDR and sandboxes, coupled with lateral movement capabilities means that, even if an organization detects and removes Nimbus Manticore from the initial infection point, the malware may have already established undiscovered footholds on other systems in the network. Incomplete remediation. Now imagine that scenario playing out over an entire week because your security tools simply couldn't see the threat.
Key Takeaways
Network security teams need to pay close attention to this one. Nimbus Manticore represents a class of threats that exploit the trust relationships between systems in your environment. Here's what you need to understand:
- Endpoint protection alone won't stop lateral movement. Even if you catch the initial infection, you need visibility into network-level threat activity to prevent propagation. RPC-based attacks happen between systems, not just on them.
- Dynamic component loading and import hiding mean your security tools need to analyze malware behavior, not just static signatures. Waiting to see what gets imported at runtime is too late if your detection approach requires seeing everything up front.
- Sandbox evasion is now a standard operating procedure. Any security strategy that depends entirely on automated analysis environments will miss threats specifically designed to avoid those environments. You need detection methods that can identify malicious intent without requiring full payload execution.
- The combination of privilege escalation and lateral movement capabilities makes containment challenging. Once malware like Nimbus Manticore gets administrative access and starts moving laterally, you're dealing with a highly-obfuscated network-wide incident.
Conclusion
Nimbus Manticore demonstrates how evolved obfuscation techniques can create lasting problems as they propagate across networks. This attack shows that modern malware authors understand both technical security controls and organizational security strategies.
It's designed to quietly establish persistence, escalate privileges, and spread across your infrastructure while remaining as invisible as possible and avoiding any potential checkpoints. That patient approach works exceptionally well against security tools that only look for immediate indicators of compromise.
Once inside, the RPC-based lateral movement capability is concerning because it exploits legitimate Windows functionality that most organizations depend on for normal operations. You can't simply disable RPC without breaking core business systems, which means attackers have a reliable pathway for spread that's difficult to defend against.
Organizations need security solutions that can identify malicious intent before full execution, and that provide visibility into both endpoint and network-level threat activity. Nimbus Manticore moves fast once it's inside your environment, and stopping it requires detection capabilities that move faster and work everywhere.
Deep Instinct has already proven it has what it takes to prevent Nimbus Manticore and countless other complex threats. Deep learning-powered cybersecurity capabilities aren’t a nice-to-have; they’re a requirement in the new cyber battlefield. Preemptive data security that scans every file and prevents threats before they execute is the perfect antidote for malware designed specifically to defeat modern security systems.
The name Nimbus Manticore might be over the top, but the threat is real. This malware has the tools to turn a single compromised endpoint into a network-wide security incident, and to keep popping back up.
Don't be one of those organizations. Don’t give the monster its opportunity. Request your free scan now to see what’s lurking in your environment.
]]>Deep Instinct recently released the sixth edition of its Voice of SecOps Report, Cybersecurity & AI – Promises, Pitfalls, and Prevention Paradise, which sheds light on how leaders across seven industries, including the retail and eCommerce sector, are bracing for this challenge. The report reveals a clear warning: while AI is driving unprecedented productivity gains for retail security teams, it’s also exposing new vulnerabilities that legacy defenses can’t handle.
Our research found that 54% of retail security teams believe file-based attacks are a moderate or critical threat to their organization, with 53% concerned about weaponized files uploaded to local or cloud storage environments. This underscores the importance of preemptive data security across retail enterprises.
Here’s what else our Voice of SecOps data found when spotlighting the retail and eCommerce sector:
AI is Powering Retail Ahead of Holiday Shopping
Retail cybersecurity teams are amongst the most aggressive adopters of AI, with 95% of retail respondents having deployed AI-powered security capabilities. In turn, they reported saving an average of 13 hours per week, outpacing the overall cross-industry average of 11.5.
The sentiment is overwhelmingly positive: 78% of respondents say generative AI makes SecOps work easier, while just 8% say it makes their jobs harder. AI is emerging as a force multiplier for retail, especially during the peak sales season when speed and scale are critical.
The Retail Industry’s Cybersecurity Strategy Is Falling Behind AI Governance
Retailers aren’t ignoring AI risks — they’re embracing AI governance, especially with the holiday shopping season approaching. Nearly three-quarters (72%) of security teams have a dedicated group actively monitoring AI outputs, while the rest report at least some level of oversight. Executive pressure is mounting as well, with 53% noting increased board-level demand for stronger preventive measures compared to last year, as organizations prepare for the surge of Black Friday, Cyber Monday, and holiday sales activity.
But here’s the disconnect: while 51% of retail security teams have implemented AI-specific defenses (from governance frameworks to AI-driven detection), one in four (24%) admit their organization’s cybersecurity strategy has not changed to replace outdated, ineffective security tools over the past year.
In other words, AI governance is happening, but cybersecurity tools haven’t caught up. Retailers risk bolting AI controls onto outdated tools and playbooks instead of rethinking preventative defenses from the ground up.
EDR Alone Won’t Protect Retailers This Holiday Season
Three out of four (74%) retail respondents say their organization is focusing more on endpoint detection and response (EDR) this year compared to 2024. But EDR is reactive by nature, only catching attacks after they’ve already caused damage. In the high-stakes holiday shopping season, that delay can mean lost sales, irreparable customer trust, and lasting brand damage.
For retail CISOs, the message is clear: as adversaries increasingly weaponize AI, waiting to respond is no longer viable. The industry needs to move beyond chasing breaches, and instead, shift toward preemptive data security, a category Gartner recently defined as stopping threats in real time, minimizing exposure, and giving defenders the upper hand. Powered by advanced AI, most predominantly deep learning, preemptive data security solutions are able to detect and block both known and unknown threats in milliseconds, before they can do damage.
This holiday season, AI-driven preemptive security isn’t a nice-to-have — it’s the difference between a successful peak sales period and a costly breach.
For more information, please download the full 2025 Voice of SecOps Report by visiting https://www.deepinstinct.com/voice-of-secops-reports.
To learn more about protecting yourself from AI-driven threats, request a free scan to see preemptive data security in action across your environment.
Survey Methodology
Sapio Research surveyed 500 senior cybersecurity experts, including 76 from retail and eCommerce companies, with 1000+ employees in the U.S. The interviews were conducted online in April 2025 using an email invitation and an online survey.
For this specific report, the C-suite is defined as those who hold chief, global, head of department, or director roles, while reports are those who hold a manager, administrator, analyst, team lead, or officer role.
]]>Among other things, it included a simple checklist of capabilities written in plain English using terms that even a script kiddie could come up with: "The code [should] encrypt itself. Find a way to exclude that. Check permission for each file and skip every file that is not encryptable due to permission being denied.”
The prompt finished with a polite request: "The encryption algorithm should be strong enough to resist brute-force attacks—when the script is done, please review the script for errors and correct defined variables and consistency."
The results were terrifying. In just 30 seconds, senior solutions engineer Ryan Heath managed to vibe-code fully executable malware, something that typically requires deep hacker “domain knowledge” and countless hours of programming.
It was a simple demonstration of a shocking reality: the barrier to entry for an entirely new generation of threat actors hasn’t just been lowered—it’s been annihilated.
undefinedThe implications should alarm everyone. When researchers from ForeScout reported that 55% of AI models failed to create working exploits, it was presented as a win. What it really means is that 45% of AI models succeeded in generating those exploits. That’s a significant problem in the world of cybersecurity, where a single successful attack can cause massive damage to an organization.
Ryan demonstrated the ease with which this can now be done in front of a live audience during a recent webinar. After creating the malware, he compiled it and scanned it with Deep Instinct’s deep learning brain, which immediately flagged it as malicious.
His next step was to test it against today’s security tools.
This was where things got downright terrifying.
undefinedEight (8) out of 73 vendors caught it.
Ryan uploaded the newly created malware to VirusTotal. Eight (8) flagged it; 65 did not.
Had this been a real-world specimen, 89% of security tools would have let it waltz right in. Then things got worse. Ryan recompiled the same malware in Go instead of Python. It only took a few seconds to produce a novel attack.
undefinedThis time, 13 vendors caught it, which sounds better until you realize that, other than Deep Instinct, they were mostly different vendors. The tools that caught the Python variant missed the Go variant, and vice versa.
Legacy tools don't only have an efficacy problem; they have a consistency problem. Sure, some of them are catching a zero-day here and there. Unfortunately, the democratization of access to unchained AI tools means that nearly every attack will be zero-day, mutated endlessly until it finds a way in.
The Dark AI Arms Race Has Already Been Lost (By Legacy Tools)
We're not headed toward an AI-powered threat landscape. We're in it. During the webinar, we showed how Dark AI tools have the potential to mutate attacks at scale. In fact, I explained during the webinar how I recently created over 700 successful variants of a single exploit in 24 hours. Each one bypassed the legacy AV protecting my test environment.
Seven hundred variants in one day. And hackers only need one to succeed.
What that means in practice is that the gap between threat creation and security detection can’t be weeks. It needs to be second to second. Legacy tools relying on machine learning (ML) and signatures aren’t able to keep up with the speed of the modern threat environment. Every minute a threat goes unidentified is a minute that organizations are vulnerable.
We proved this with real-world malware from the Nimbus Manticore threat group, which is actively targeting aerospace, defense, manufacturing, and telecommunications organizations. When this malware first appeared, only three (3) vendors caught it on VirusTotal. Of course, we were one of them. For one variant, we were the only vendor detecting it, weeks after it appeared in the wild. That means thousands of organizations have been, and continue to be, vulnerable.
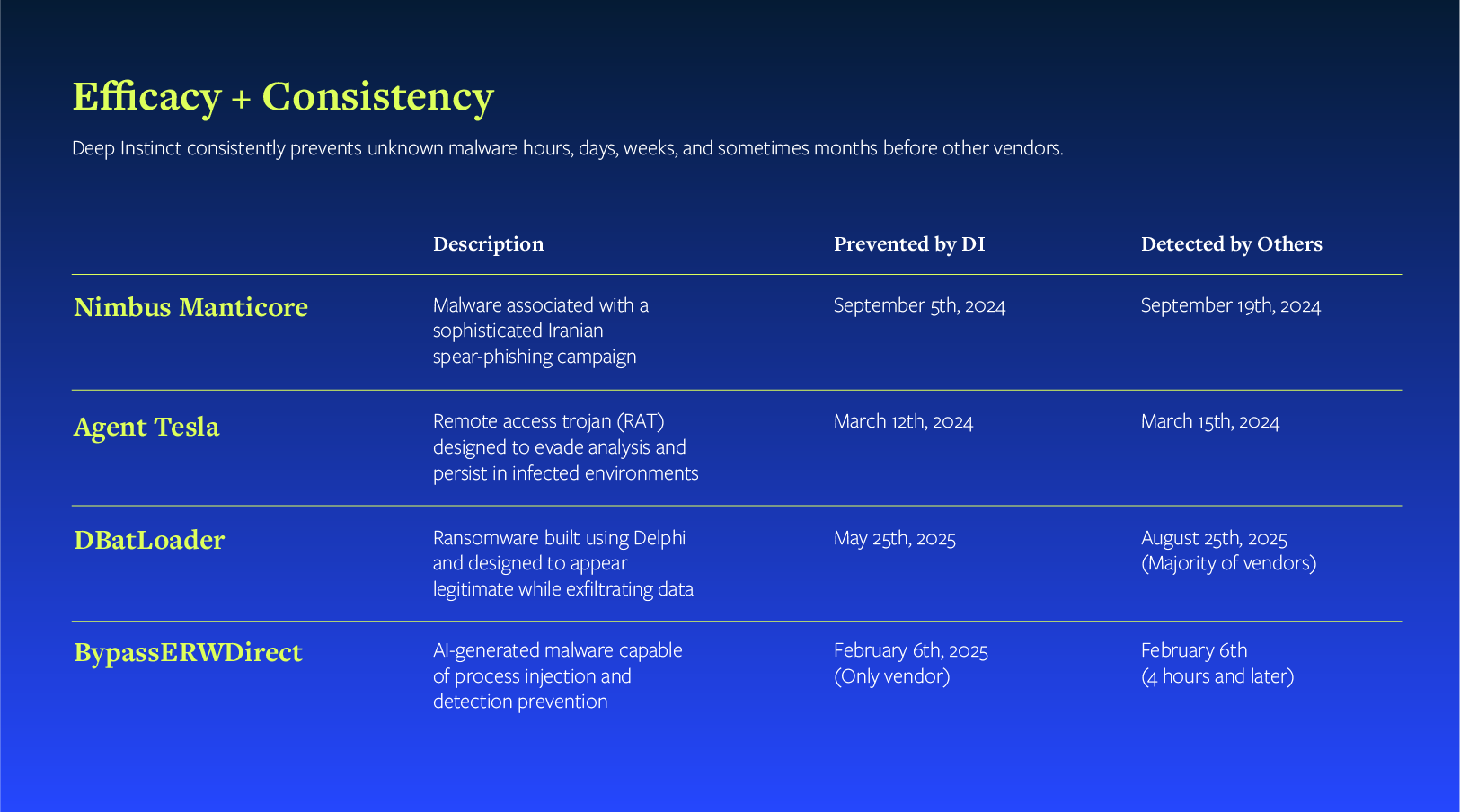
Transcending the current paradigm requires new and improved solutions, specifically advanced, deep learning AI. And only Deep Instinct has a deep learning framework specifically built for cybersecurity.
The Problem Legacy Tools Can't Solve: Explaining What Hasn't Happened
Most AI tools in cybersecurity excel at explaining breaches after they have occurred. For example, they'll tell you exactly how the memory injection worked because the memory injection already happened.
They can give you detailed attribution on data exfiltration because someone’s data was actually exfiltrated. They are forensic tools built for post-mortems. In layman’s terms, you’ve already lost.
For decades, we've watched major breaches where technology didn't fail; the humans did. As I said during the webinar, “Systems screaming, alarms blaring, security teams dismissing alerts because they didn't understand them or lacked context.” At the end of it, threats are missed, benign files are blocked, and nobody is happy—and no one has an explanation until well after the fact.
Preemptive data security powered by deep learning solves the zero-day threat problem. AI explainability solves the problem of contextualizing threats, explaining why files were quarantined, and making the security alerts make sense. Both are mission-critical for SOC teams.
DIANNA: Seconds to Explainability
The DSX Companion—also known as DIANNA—is Deep Instinct’s malware explainability solution. We demonstrated DIANNA by analyzing the malware we created live. In <10 seconds, we had a comprehensive analysis that typically takes SOC analysts hours or days to complete manually.
undefinedDIANNA didn't just say, "This is malicious." It explained how: sleep commands designed to evade sandbox detection, CPU tick monitoring to detect when AV solutions ramp up, process termination functions targeting other security tools, and encrypted sections hiding imports. It identified specific techniques that even experienced pen testers recognize as sophisticated evasion.
Explainability empowers humans to make informed decisions. When a department head calls saying you've "erroneously blocked" a file and demands you release it, your SOC analyst pulls up DIANNA's analysis and explains, in clear language, exactly why that file would have encrypted your data and dropped ransom notes on every desktop.
Consistency Matters as Much as Efficacy
The question isn't whether your AV tool will eventually catch the malware. It's whether it caught it on first contact.
Legacy tools plateau because they're built on reactive architectures. They need to see the threat, analyze behavior, update signatures, and push definitions. By the time that cycle completes, 700 new variants will have flooded your organization’s network.
Pre-execution prevention using deep learning works differently. It examines files statically, making decisions before execution based on deep contextual understanding, not whether it's seen that specific hash before. In the webinar, a two-year-old DSX Brain was catching malware that didn't exist when it was trained; malware that updated tools were still missing.
AI. Everywhere.
We're early in our AI journey. The Dark AI tools we demonstrated in our webinar will look primitive next year. Criminal adoption of AI will accelerate as the technology becomes more sophisticated, accessible, and capable of automating the entire attack lifecycle.
The tools that worked for the past decade won't work for the next one. Tools that worked last year may not work at all. Not when threat actors generate variants faster than signatures are updated. Not when the window of opportunity measures in seconds. Not when consistency across infinite variations becomes the difference between prevention and breach.
Watch our on-demand webinar to see the full live demonstration of Dark AI malware creation, DIANNA's real-time analysis, and why preemptive prevention through deep learning represents the shift cybersecurity needs now.
If you’re overwhelmed by the wave of Dark AI, there is hope. Request your free scan to see what malware is lurking in your environment—and stay safe from breaches.
]]>Today, I'm breaking down DBatLoader, a malware that demonstrates how cybercriminals continue to abuse legitimate programming languages and development frameworks to create increasingly sophisticated threats. This one's built using Delphi, which might surprise some of you since most people associate Delphi with legacy business applications, not cutting-edge malware. Turns out attackers aren't picky about their development platforms. If it works, it works.
What makes DBatLoader particularly interesting isn't just where it comes from or what it does, but how hard it tries to hide what it's doing. This malware comes packed with obfuscation techniques and anti-analysis features that make reverse-engineering it a big challenge, even for the experts.
The Malware: DBatLoader
DBatLoader is a Delphi-compiled Windows executable targeting x86 systems, and it's designed with one clear goal: establish a foothold on target machines while staying completely under the radar. The cybercriminals behind this one clearly understand that the best malware is the kind that nobody notices until it's too late.
This isn't your run-of-the-mill basic malware attempt—the technical sophistication here suggests experienced developers who know their way around both legitimate software development and evasion techniques, with clear knowledge of how defenders think. They've built something that can slip past traditional security measures while setting up shop for whatever comes next.
The malware's approach is methodical and patient. Rather than immediately launching into clearly malicious behavior, DBatLoader takes its time to assess the environment, check for security tools, and establish persistence before revealing its true capabilities. It's the digital equivalent of casing a house before breaking in and ransacking the place once the coast is clear.
Capabilities
Loaded with a comprehensive suite of surveillance and system manipulation tools, DBatLoader should make any security professional nervous. Static analysis reveals sections with abnormally high entropy levels, which are a clear indicator that the malware authors compressed or encrypted significant portions of their code to avoid detection.
My analysis of the resource section also tells an interesting story. I found a large collection of strings, many of which point to anti-analysis techniques and evasion capabilities. Basically, the malware knows when it's being watched and can adjust its behavior accordingly.
But here's where things get really concerning: the import analysis reveals capabilities for registry manipulation, screenshot capture, code injection, and debugger detection. That's essentially a complete toolkit for system compromise and data theft. Add in potential keylogging functionality, and you've got malware that can capture virtually anything happening on the infected machine.
Then there’s an old classic: the malware also employs import hiding techniques to make static analysis more difficult. By concealing some of its intended functionality until runtime, DBatLoader can slip past security tools that rely heavily on import table analysis for threat detection.
Additionally, some specific technical indicators caught my attention. Functions like GetTickCount and Sleep suggest the malware measures execution timing to detect sandbox environments, which is a common trick to avoid analysis in security research labs.
Finally, the kicker. The presence of multiple Windows system DLLs (MAPI32.DLL, USER32.DLL, advapi32.dll, kernel32.dll, oleaut32.dll) indicates broad system interaction capabilities. DBatLoader is bringing the tools necessary to interact broadly with Windows systems and exfiltrate a wide range of sensitive data.
Timeline
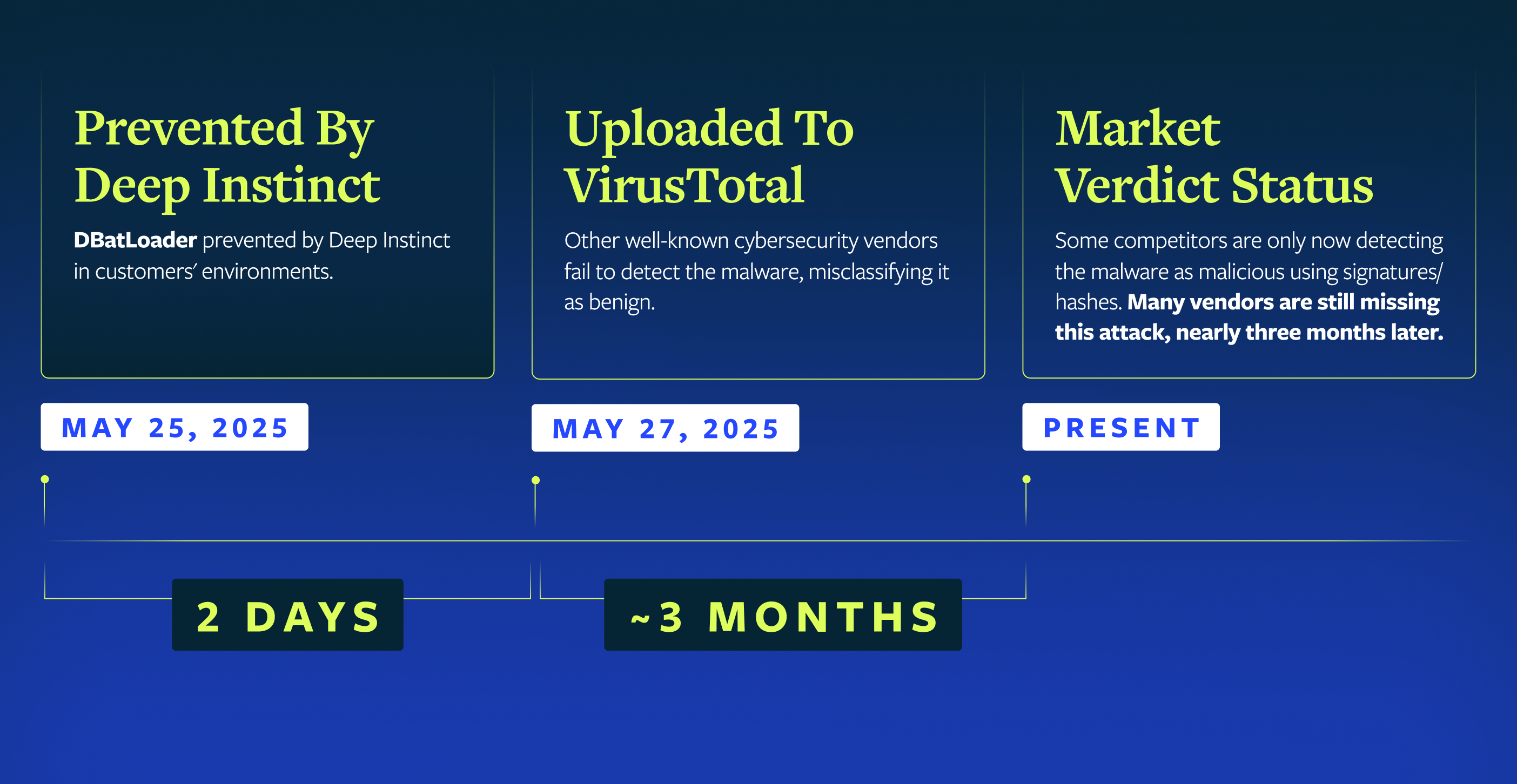
The detection timeline here reinforces a pattern I see consistently: there's often a significant gap between when never-before-seen threats appear and when traditional security tools recognize them. During that window, organizations remain vulnerable to active compromise.
Behind the scenes, another important distinction is made clear: the list of vendors catching malware early is not consistent. Deep Instinct is the only consistent defense against these complicated threats in their myriad forms.
Competitive Differences
dBatLoader highlights some critical gaps in how traditional security tools approach threat detection. The malware's use of legitimate development frameworks and careful obfuscation techniques can easily fool signature-based detection systems that haven't seen this specific variant before.
The anti-analysis capabilities present another challenge for behavioral detection systems. When malware can detect and evade sandbox environments, traditional dynamic analysis approaches become far less effective. Many security tools rely on automated analysis environments that DBatLoader is specifically designed to recognize and avoid.
The import hiding techniques add yet another layer of complexity. Security tools that depend on static analysis of import tables for threat classification will miss critical functionality that only becomes apparent during actual execution.
Perhaps most importantly, DBatLoader's patient, methodical approach to system compromise means that security tools focused on immediate threat detection might miss the gradual establishment of persistence and surveillance capabilities. By the time the malware reveals its true intentions, it may have already gathered significant intelligence about the target environment. “Rolling back” to an earlier uncompromised state, may be nearly impossible, will certainly be costly, and won’t undo the damage of whatever was already exfiltrated.
Key Takeaways
Security teams need to understand that dBatLoader represents a category of threats that specifically target the limitations of traditional security approaches, such as multi-av, machine learning, signature-based detection, and more that attackers know defenders are using. Here's what matters:
The use of legitimate development frameworks can make malware more dangerous. Delphi applications are common in enterprise environments, which means DBatLoader can blend into normal software ecosystems more easily than malware written in obviously suspicious languages.
Anti-analysis capabilities are becoming standard features, not advanced techniques. Any security tool that can't handle evasive malware is going to miss a significant number of real threats. And that’s only going to worsen with the rising volume and sophistication of AI-driven threats.
Patient, gradual compromise strategies require detection capabilities that can identify malicious intent before full payload deployment. Waiting for obviously malicious behavior means expecting to be compromised (see the earlier point about rolling back).
The combination of screenshot capture, keylogging, and code-injection capabilities makes dBatLoader a significant data theft risk. Organizations need to assume that any successful compromise could result in broad and devastating data exfiltration.
Conclusion
DBatLoader demonstrates that modern malware authors are professional software developers who understand both their craft and their adversaries. The careful attention to evasion techniques, anti-analysis capabilities, and gradual compromise strategies shows a level of sophistication that traditional security measures struggle to address.
The good news is that preemptive security solutions like Deep Instinct DSX can identify malicious characteristics, rather than relying on heuristics or signatures, to remain supremely effective against these evolving threats. The bad news is that organizations relying on reactive detection approaches are likely to face some unpleasant surprises as threats like DBatLoader become more common.
This malware family isn't trying to announce its presence, it's designed to disappear into your environment and operate undetected for as long as possible. That approach works particularly well against security tools that only look for obvious indicators of compromise. Unfortunately ... that’s how most legacy tools operate.
The message here is clear: if your security stack can't handle sophisticated, evasive threats that use legitimate development tools and patient compromise strategies, you're going to have problems. DBatLoader might not be the flashiest malware I've analyzed, but it's exactly the kind of threat that causes long-term damage to organizations that don't see it coming.
Request your free scan to see what your existing tools have missed while future-proofing against the rise of AI-driven threats.
]]>Drawing on this year’s data, we took a deeper dive into the sector facing the most significant threats – and the highest stakes: financial services. These firms must not only navigate escalating AI-driven cyber threats, but balance strict compliance requirements and the added pressure of safeguarding extremely sensitive, high-value data.
Here’s what our Voice of SecOps data found when spotlighting financial services:
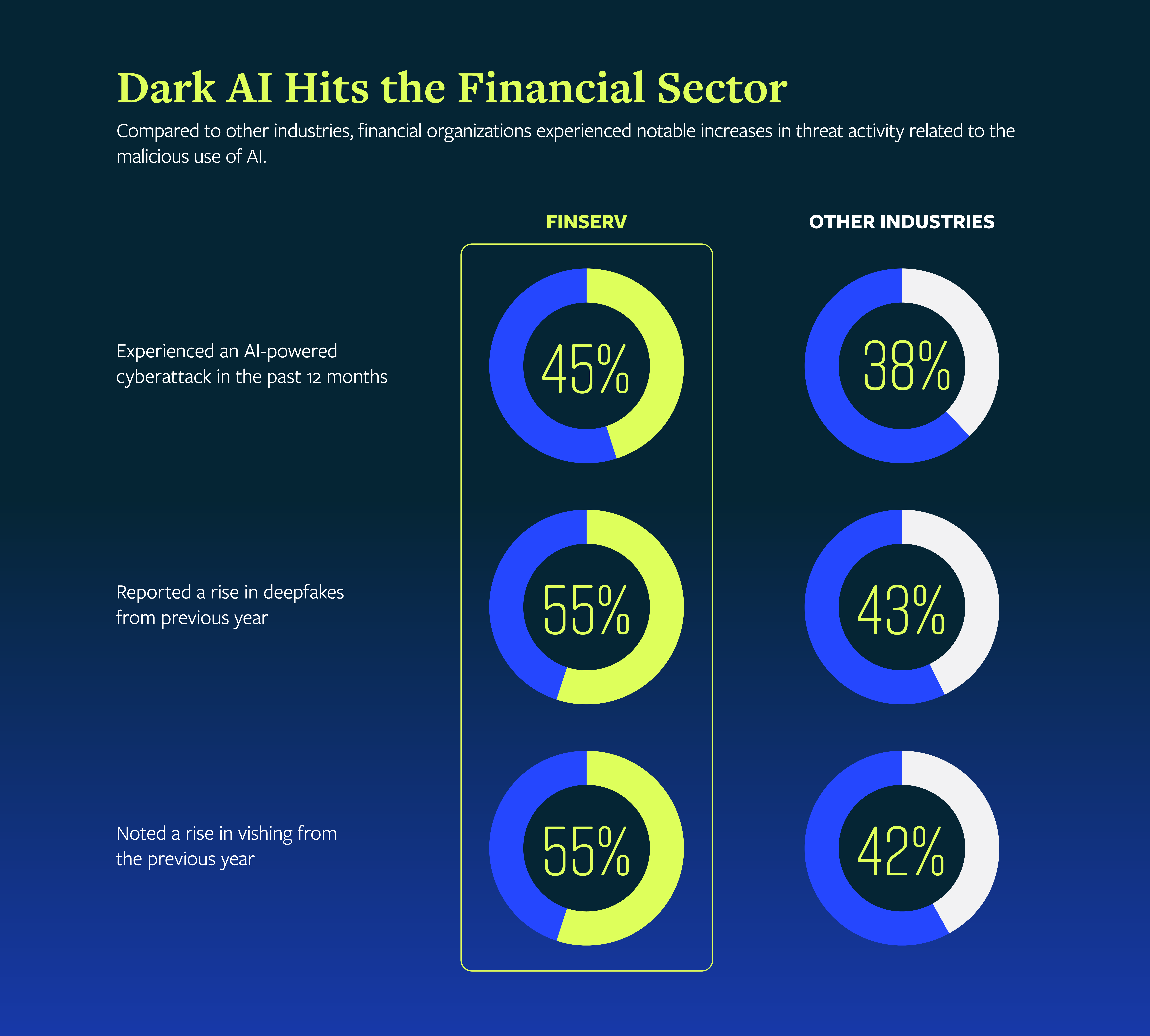
Dark AI Hits the Financial Sector Hardest
AI-driven threats are hitting the financial services industry with explosive force. Nearly half (45%) of financial institutions experienced an AI-powered cyber attack in the past 12 months, which is significantly higher than the 38% reported across other sectors. Among those impacted, the top repercussions were the theft of sensitive or proprietary data (71%), reputational damage (64%), and financial loss (49%).
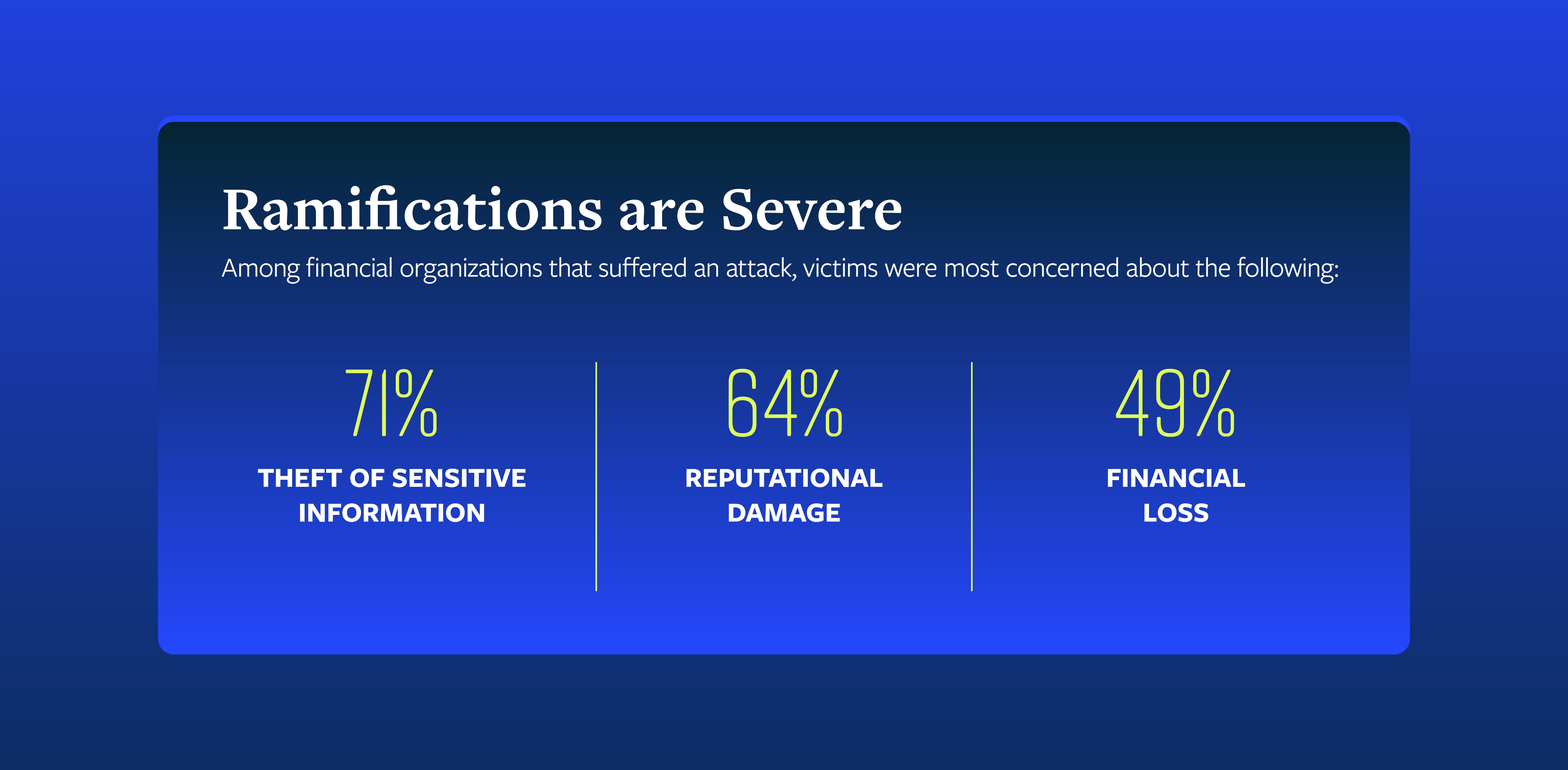
Additionally, while 43% of all respondents reported a rise in deepfakes over the past year, that number climbs to 55% in financial services. Vishing attacks follow the same pattern – 42% overall versus 55% in finance – highlighting the sector’s status as a prime target in the eyes of cybercriminals.
Finance Leaders Push for Preemptive Prevention
The surge in AI-powered cyber threats has forced financial services firms to rethink their cybersecurity strategies. In fact, 69% of respondents in the finance sector say they feel increased pressure from the Board and C-suite to implement a prevention-first security strategy, rooted in preemptive data security. This figure ranks higher than other sectors, signaling that financial firms’ leadership recognize that reactive defenses are insufficient against growing AI threats.
Adapting to these executive mandates poses a significant challenge for finance teams, as it requires a shift from accepting the “status quo” and embracing a new approach to cybersecurity that prioritizes preventing threats before breach.

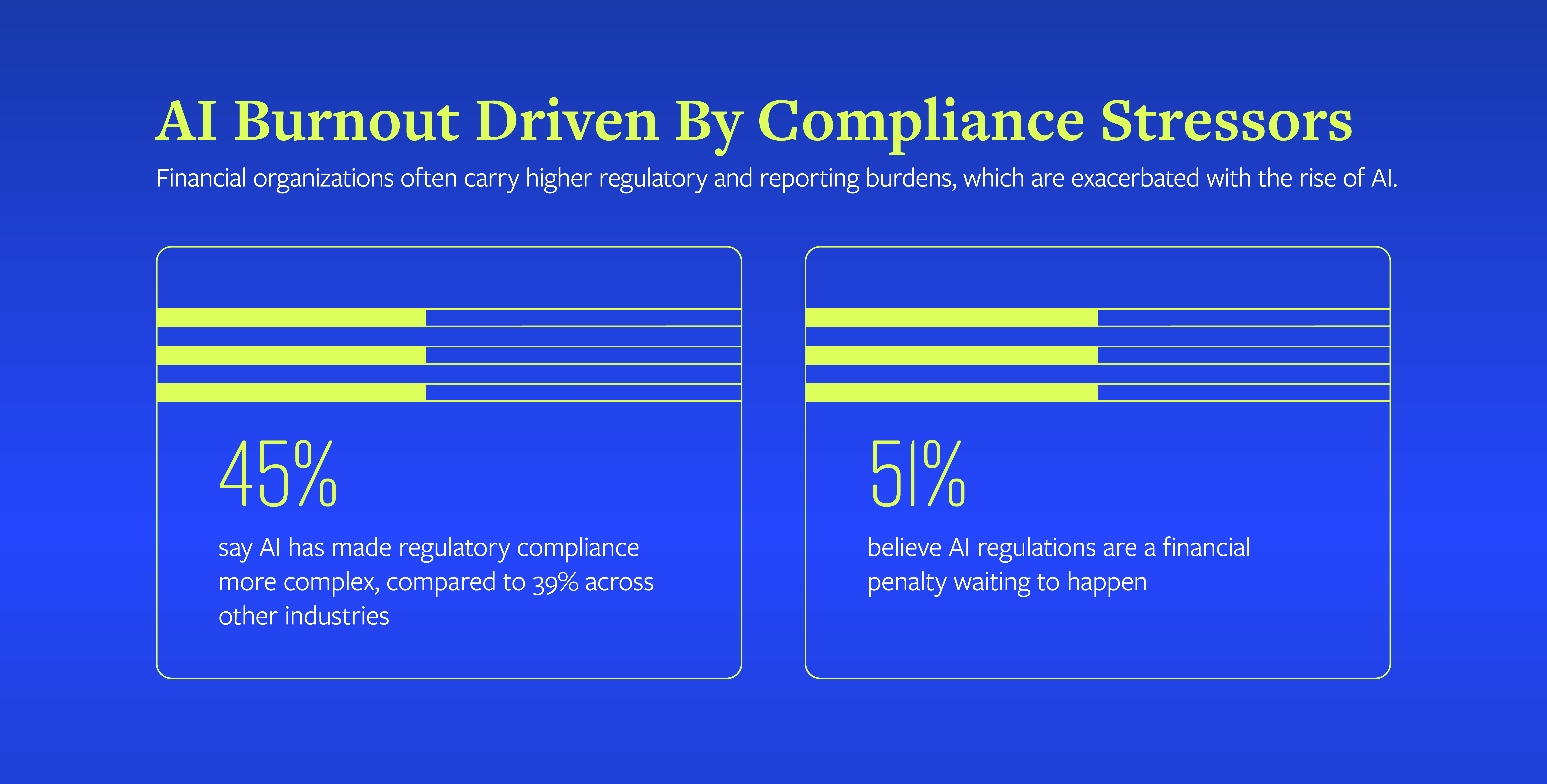
AI Burnout Driven by Training and Compliance Gaps
As AI adoption accelerates across financial services, many security teams are feeling the strain due to new risks, mounting compliance demands, and a growing sense of burnout. In 2024, nearly 60% of financial services professionals reported higher stress levels over the past year, driven largely by the surge in AI-powered threats and the pressure to respond at machine speed. One in three SecOps leaders in the sector cited staffing and resource shortages as a key stressor, underscoring how AI-enhanced attacks are pushing overburdened teams to the brink.
Compliance is also compounding the pressure, with 45% of financial services leaders saying AI has made regulatory compliance more complex, compared to just 39% across other industries. Even more concerning, more than half (51%) believe AI regulations are a financial penalty waiting to happen, a sharp contrast to just 37% in other sectors. As AI tools become more integrated, financial firms face mounting urgency to adopt solutions that strengthen security without compromising compliance.
The Answer is Preemptive Data Security
As financial services cyber teams confront rising threat volumes, burnout, and the complexities of AI, preemptive data security becomes a strategic imperative. Based on Gartner’s newly defined preemptive cybersecurity category, this approach stops attacks in real time, easing pressure on overextended teams, minimizing risk exposure, and delivering the proactive defense modern enterprises require.
In a recent conversation with Deep Instinct’s CIO Carl Froggett, he told me:
"The financial services sector has always been a top target for cyberattacks, but the rapid evolution of AI has tilted the balance further in favor of adversaries. To regain control, SecOps teams must respond with equally advanced AI—integrated across the entire security architecture. While many organizations “bolt on” reactive AI within Security Operations, they’re not addressing the root cause of the problem. The most effective way for financial institutions to proactively defend against AI-driven threats is through Deep Instinct’s unique deep learning approach, purpose-built to prevent threats before they cause disruption."
For more information, download our infographic, “Voice of SecOps 2025 Spotlight: AI’s Impact on Financial Services,” or the full 2025 Voice of SecOps Report by visiting https://www.deepinstinct.com/voice-of-secops-reports.
And if you’re serious about protecting your data instead of detecting and responding post breach, request your free scan today to find threats you didn’t know were lurking in your environment.
Survey Methodology
Sapio Research surveyed 100 senior cybersecurity experts from financial services companies with 1000+ employees in the U.S. The interviews were conducted online in April 2025 using an email invitation and an online survey.
For this specific report, the C-suite is defined as those who hold chief, global, head of department, or director roles, while reports are those who hold a manager, administrator, analyst, team lead, or officer role.
]]>Humans have always wanted to know the future. Whether through oracles, tea leaves, knuckle bones, or tarot, trying to divine fate has been a constant endeavor throughout human history. Right now, the future seems clear—and the already Sisyphean task of protecting data in an ever-evolving threat landscape feels more like an exercise in preventing fate.
Except fate may be too strong a word—what you’re actually preventing is the outcome of a logical series of events culminating in the compromise of your data. Augury isn’t needed to see what’s coming next: advanced AI is being used to generate a higher volume of attacks at an accelerated pace and with an alarming degree of complexity. Cybercriminals are innovating at a speed that most cyber vendors can’t match. That leaves data vulnerable.
The Stacked Deck
Right now, the deck is stacked against defenders. The cards we have been dealt foretell calamity in one way or another—confusion, delay, and disaster. Legacy tools are ineffective, the buying process is bureaucratic and slow, and Dark AI is evolving faster than ever. Chaos abounds.
Past experience is no longer a guide either. Handcrafted attacks are dying out in favor of automation. AI has compressed the timeline of an attack: from the recon of potential targets to social engineering and malware creation, everything has been augmented, accelerated, and automated by dark forces (Dark AI tools) that enable bad actors to mobilize quickly and keep sustained pressure until they find an opening.
The tools we have traditionally trusted cannot keep our data safe. Signature-reliant systems are ineffective against rapidly mutating, AI-generated attacks, while new obfuscation methods have weakened heuristics. And, powered by AI, phishing tools have become so advanced that even trained professionals are routinely fooled. Without changing our approach to cybersecurity, organizations are fated to be breached. We are left asking when, not if.
Fighting Fate
In folklore, this would be the point at which the hero discovers a powerful talisman or mythical weapon that will allow them to fight their destiny. In tarot, a single card—or a combination of cards—can reveal a path that can change what seems predetermined. In cybersecurity, a similar paradigm shift is underway. While the threats ahead may seem foretold, new powers are emerging that can help organizations rewrite their security fate. This new approach is called preemptive data security, and right now, Deep Instinct holds two powerful cards you can play to avert catastrophe. These aren’t just tools, they’re talismans of transformation.

Preemptive data security solutions use advanced AI to detect and prevent threats before they can execute. They also equip security teams with critical information about prevented threats so that SOC teams can address vulnerabilities and complete investigations. Rather than reacting to attacks after they have commenced, preemptive solutions stop them before breach.
The Age of Dark AI
The rise of AI-powered attacks has rendered traditional reactive security relics of the past. When cybercriminals and hostile nation-state actors can generate thousands of unique malware variants in minutes, organizations need security that works at machine speed. This reality is driving rapid adoption of preemptive data security solutions—so much so that Gartner projects 100% of organizations will have some form of preemptive security capabilities by 2030. The prophecy has been written: adapt or be breached.
Data Security X (DSX) is Deep Instinct’s preemptive data security solution. DSX leverages the deep learning-powered DSX Brain, an entity unlike any other in cybersecurity, to detect and prevent unknown and zero-day threats with unparalleled accuracy and speed. Our deep learning framework is the only one in the world explicitly trained for cybersecurity. It recognizes malicious files without relying on signatures and without human-biased heuristics. Because it has been trained on tens of billions of data points, its ‘recognition’ of malicious files is nearly instantaneous—and exponentially more advanced than a simple machine learning framework.
Working in tandem with the DSX Brain to power preemptive data security is the Deep Instinct Artificial Neural Network Assistant, or DIANNA, our GenAI companion for both known and unknown malware explainability. DIANNA is your companion on the journey, your seer in the dark. DIANNA provides readouts in seconds that explain why a file was flagged as malicious and then quarantined or deleted. This is an essential capability of any preemptive solution because the volume and complexity of attacks are increasing daily. Human teams need resources that augment their ability to understand threats and their patterns.
It won’t be possible to hire your way past this darkness. You’ll need a guide.

Control Your Fate
Organizations need to fight AI with AI. And to win, they need better AI. Deep learning frameworks are rare, with only a dozen or so true DL frameworks in existence—and only one built from the ground up for cyber: DSX. They are uniquely capable of self-learning, an invaluable trait in the context of an ever-changing cybersecurity landscape. Our purpose-trained DL framework makes Deep Instinct the leader in preemptive data security. Because deep learning frameworks take years to craft and perfect, we are blazing a trail that legacy vendors cannot tread—unfortunately, future threats are here now.
The cards are on the table, and they paint a dark picture. But the future isn’t fixed. By conjuring a security posture built to fight advanced threats, organizations can change their fate—and protect their data from dark forces. Deep Instinct is the first and only deep learning-powered preemptive data security solution designed to detect and prevent the evolving threats that every organization faces. Our technology changes the fate legacy tools cannot avert.
]]>Today, we’re revisiting a particularly stealthy variant of Agent Tesla we uncovered last year—highlighting how much earlier the deep learning-driven DSX Brain detected it compared to competitors.
First things first: If you are not familiar with this malware family—Agent Tesla is a sophisticated Remote Access Trojan (RAT) that has plagued security teams since 2014, engineered to fly under the radar while systematically stealing sensitive data from infected systems. The version we caught last year shows that bad actors are still finding new ways to obscure it and make it more dangerous.
The Malware: Agent Tesla Information Stealer Variant
Agent Tesla isn't new, but this variant stood out for its aggressive use of advanced evasion techniques—including a multi-layered approach to avoiding detection, anti-analysis features, and clever obfuscation tricks designed to fool traditional security tools. But it didn’t fool us.
The malware's primary mission is to steal everything it can get its hands on: keystrokes, clipboard contents, browser credentials, email passwords, etc. Like a real rat attracted to anything shiny, if there is valuable data on your system, this variant wants it. And once it has what it came for, it ships everything off to its controllers using Telegram as the communication channel.
Capabilities
Agent Tesla comes loaded with a comprehensive toolkit for data theft and system infiltration. The text section analysis reveals abnormal entropy levels, a dead giveaway that the malware authors used encoding or compression to hide their real intentions.
The import table tells an interesting story, too. This malware can interact with the Windows registry, create temporary files, launch additional programs, and modify access control lists. That's a lot of system-level access—and it's exactly what you'd expect from something designed to assert control and surveillance of your machine.
But wait, there's more. The malware includes specific anti-analysis techniques that check execution timing and hunt for telltale signs of cybersecurity tools. Basically, it ‘knows’ when it's being watched and can adjust its behavior accordingly. Classic cat-and-mouse RAT stuff.
String analysis reveals capabilities for file operations, network communication, and user interface manipulation—grabbing files, exfiltrating them to the attackers, and tricking users with fake dialog boxes and prompts. The combination is particularly dangerous because it can gather data from multiple sources while potentially social-engineering users into giving up additional information.
Timeline
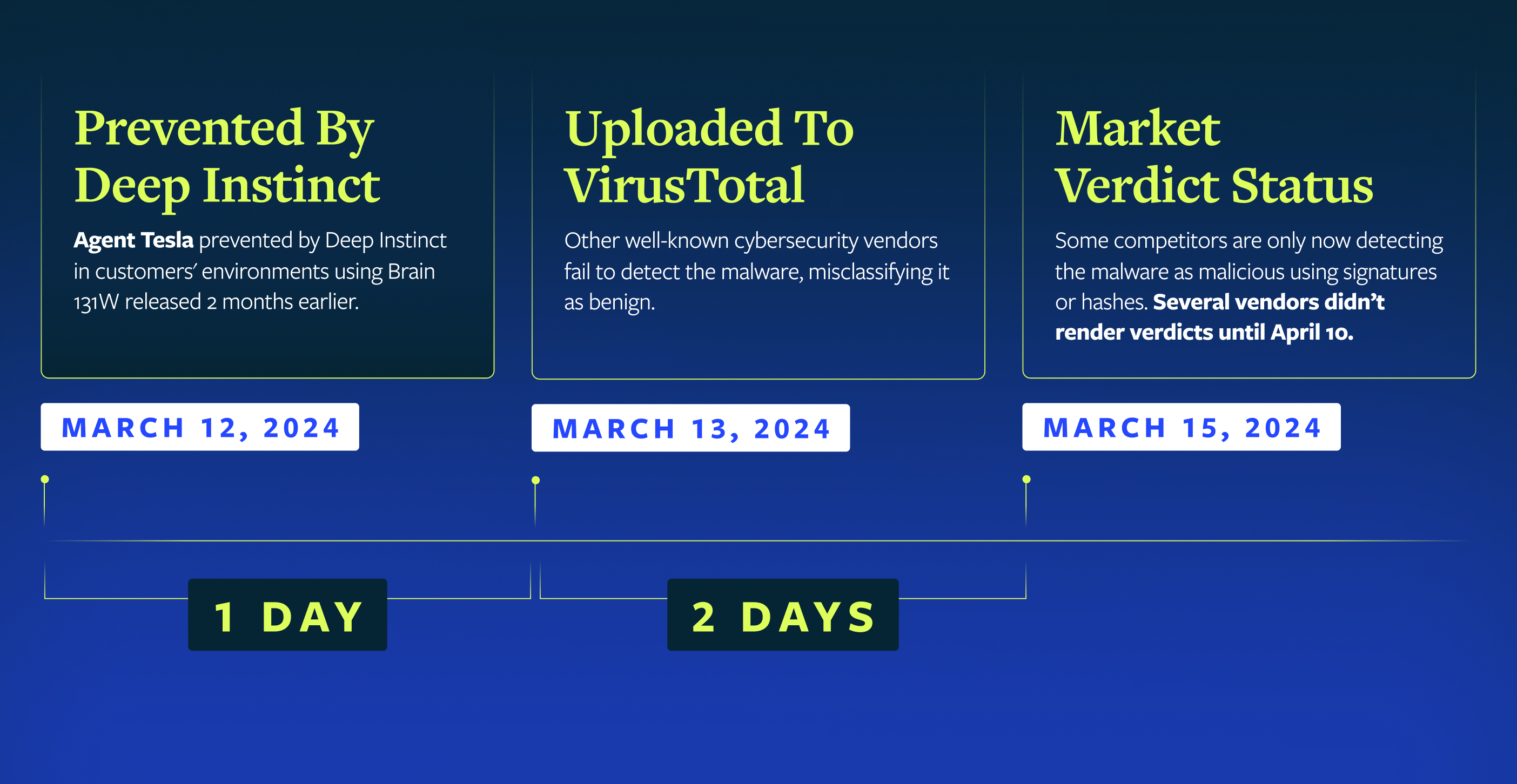
Using a brain that was already a few months old, the DSX Brain detected and prevented Agent Tesla in customer environments a day before it was uploaded to VirusTotal (VT). Even after it was uploaded, the majority of the “leading” cybersecurity vendors were not classifying Agent Tesla as malicious. Two days after the upload to VT (which is three days after we prevented it) a small number of major providers began to recognize Agent Tesla as malicious.
The detection timeline here reinforces something we see repeatedly: there's a significant gap between when advanced threats appear and when legacy security tools catch up. During that window, organizations relying on signature-based detection or inferior and slower machine learning models remain vulnerable to active attacks. Sometimes it’s just for a few hours. In the case of Agent Tesla, it was days. And it can easily extend to weeks, even with the most prestigious protection.
Competitive Differences
Here's where things get interesting from a competitive standpoint. While other security vendors were still playing catch-up, our deep learning-based preemptive security engine identified this threat's malicious intent before it could execute its payload. That's not luck, it’s the difference between reactive and preemptive data security. And it’s something I will demonstrate through all of the DIANNA Explains blogs.
Legacy antivirus tools struggle with Agent Tesla variants because the malware family has mastered the art of morphing its signature while maintaining its core functionality. Signature-based detection becomes useless when attackers can trivially modify their code to evade static analysis. And that’s the Dark AI era in which we’re now living.
Even behavioral analysis systems can struggle here because Agent Tesla variants are designed to mimic legitimate system activities during their initial reconnaissance phases. By the time many legacy tools recognize the threat, the malware has already established persistence and begun its data collection activities.
The Telegram command-and-control infrastructure adds another wrinkle. Many organizations don't monitor or restrict Telegram traffic, assuming it's just employee messaging. That assumption creates a blind spot that information stealers like Agent Tesla happily exploit.
Key Takeaways
Security teams, please pay attention to this one. Agent Tesla variants represent the evolution of commodity malware. It’s a class of malware that is getting smarter, stealthier, and more persistent.
Here's what you need to know:
This malware family isn't going anywhere. Agent Tesla has proven remarkably adaptable, with new variants appearing regularly that incorporate the latest evasion techniques. Expecting signature-based tools to keep pace is unrealistic.
Your network monitoring needs to account for legitimate services being abused for malicious communication. Telegram, Discord, and similar platforms are increasingly popular with malware authors because they blend into normal traffic patterns.
Employee training remains critical, but it's not sufficient on its own. Agent Tesla variants often arrive through phishing campaigns, but they're designed to operate silently once they gain initial access. Users may never realize they've been compromised.
Consider your detection capabilities across the entire attack lifecycle. This malware is built to persist and operate over extended periods of time. Tools that only focus on initial infection detection will miss the ongoing data exfiltration activities.
Conclusion
Agent Tesla continues to be a persistent threat because it works. This latest variant demonstrates that even well-known malware families can evolve to stay ahead of traditional security measures. The combination of advanced evasion techniques, multi-source data theft capabilities, and abuse of legitimate communication platforms makes these threats particularly challenging for reactive security tools.
The good news? Preemptive data security from Deep Instinct can identify malicious intent before execution and is highly effective against these evolving threats.
The bad news? If you're still relying on signature-based detection or hoping your legacy AV or reactive EDR will catch everything (or much of anything, if we’re being real), you're inevitably going to have some unpleasant surprises.
Agent Tesla is not the most sophisticated malware we have ever analyzed, but it doesn't need to be. It is effective, adaptable, and profitable for cybercriminals. That combination means we'll keep seeing new variants, and security teams need detection capabilities that can keep pace with that evolution.
Stay sharp out there.
If you want to stay ahead of these threats, request your free scan to see what your existing tools have missed.
]]>I wanted to share my perspective, shaped by past experience, and explain why I deployed Deep Instinct.
The short answer: Assume everything is malicious.
Don’t rely on a single layer of defense. Why? At the endpoint, the attacker is already one step from winning. You want to prevent the threat as far away from your critical business services, infrastructure, and data as possible. Cyber technologies are not bullet proof, especially against shifting threats, and supply chain risk is real. (I include any third party in the supply chain, including customers of your business). We tend to trust that our partners and vendors are doing the right thing. And while they may have compliance programs in place, time and again, we’ve seen real world breaches of 'compliant' third parties.
An example of this exact situation was recently reported by Help Net Security when an unnamed MSP was compromised by an attacker who then used their access to client environments to upload the DragonForce ransomware. This breakdown in security is significant because the ransomware came from a ‘trusted’ source that had legitimate access, who could push files (various updates) into client environments
While supply-chain attacks like this have the potential to degrade the trust in an entire industry and create a chokepoint for management, the danger isn’t limited to MSPs. There are many such examples from M&A, zero-trust (between zones), customer-facing documents, and file transfer systems—the list is endless. This incident demonstrates why organizations need to scan everything, including updates from trusted partners.
Data Security X (DSX) for Applications provides an elegant solution to this problem—and it is what I deployed at scale to neutralize this threat vector while at Citi. Using advanced deep learning AI, DSX-A can be deployed by either the customer, or the MSP in this case, to scan and verify the updates being pushed to client environments. Because DSX-A doesn’t rely on rigid machine learning capabilities, known signatures, or human-biased heuristics, it’s able to prevent novel attacks as well as known attacks. Industry-best scan speed also ensures that managed updates don’t become a bottleneck or organizational headache. All of this is done with data privacy in mind, ensuring we neither see nor use your data for any purpose.
This deployment provides a significant reduction in risk, adding an advanced layer of preemptive data security before the attacker achieves their objective, which is usually access to your devices and data. Criminals are getting bolder and better every day at bypassing traditional security measures and technologies that the industry has long relied upon. New solutions that can match the flexibility of cybercriminals are an operational imperative in the era of AI-driven threats.
Deep Instinct is uniquely capable of providing this new form of preemptive data security. By implementing comprehensive scanning across all data and updates—regardless of source—organizations can better protect themselves against evolving threats. Get your free scan to see it in action.
]]>Strengthened Collaboration with AWS to Secure Cloud Data
To kick off the week, Deep Instinct announced two AWS milestones: achieving 'Deployed on AWS' status and acceptance into the AWS ISV Accelerate Program. These milestones further strengthen our strategic collaboration with AWS and underscore our shared commitment to securing cloud data as organizations accelerate their digital transformation.
With the induction into these programs, Deep Instinct can provide the world's most advanced preemptive data security to AWS customers. Specifically, AWS customers now have greater access to Deep Instinct’s Data Security X (DSX) for Cloud - Amazon S3 solution, which provides preemptive data security for Amazon S3 buckets, ensuring real-time prevention and explainability of zero-day attacks.
You can read more about these milestones in a LinkedIn post from our CEO Lane Bess, our press release, as well as on BigDATAwire.
Unveiled the 2025 Voice of SecOps Report
The next day, following the news of our work with AWS, we released the sixth edition of our annual Voice of SecOps Report: “Cybersecurity & AI: Promises, Pitfalls – and Prevention Paradise.” This research has emerged as the gold standard for understanding AI’s impact on front-line defenders.
This year’s data revealed that nearly three-quarters (72%) of organizations have revised their cybersecurity strategies over the past year due to AI, and a whopping 86% have increased their use of AI within SecOps. Yet, data showed 38% still can’t identify the technical differences between machine learning and deep learning. Building understanding is critical because only deep learning is capable of delivering preemptive data security. Anything less isn’t enough.
Download the full report here, or view top findings in our press release. You can also read more in Tech Monitor and Enterprise Security Tech, or listen to our CEO Lane Bess discuss the findings with NYSE in the video below:
For an even deeper dive and expert analysis, you can watch a full webinar of the Voice of SecOps 2025 research here.
Inducted into the NYSE LaunchPad Class of 2025
And it doesn’t stop there! The Deep Instinct team took New York by storm on June 3rd to celebrate our induction into the NYSE LaunchPad program.
Being selected as a LaunchPad member allows us to connect with an influential network of mentors, innovators, and strategic partners, further fueling our mission to transform preemptive data security on a global scale. One of the top highlights was taking over the NYSE floor and seeing our name in Times Square – signaling a new era of cybersecurity, fueled by deep learning-based preemptive data security.
Learn more about what this means for Deep Instinct in this joint interview with Deep Instinct CEO Lane Bess and CIO Carl Froggett on theCUBE.


Lights, Camera, Action: CEO Lane Bess in Entrepreneur video shoot
From New York to Long Beach – Deep Instinct’s CEO Lane Bess also took time to film an in-person video segment with Entrepreneur’s The CEO Series with Will Salvi. Check out the video here.


Thank you to our customers and partners, AWS, NYSE, theCUBE, and the entire Deep Instinct team for helping make this past week possible. Together, we’re redefining what it means to protect customer data, with preemptive data security blazing the path forward.
]]>