What Makes PowerShell a Challenge for Cybersecurity Solutions?
PowerShell[1] is a command-line shell interface that leverages the .NET framework. Its main purpose is to assist in task automation, however, unlike other shells like Bash, fish, and Zsh, PowerShell is not only a shell, but also an interpreted language with the ability to run scripts.
PowerShell has several compelling qualities which make it a natural choice for automation development:
- It is pre-installed on every Windows operating system from Window 7 onwards
- It has been open source since 2016
- It is supported over Linux and MacOS, as well as Windows
- It offers direct access to Win32 API
For as popular and powerful as these attributes make PowerShell for the developer community, these qualities also make it an ideal tool for post-exploitation, thus making it popular to threat actors in recent years.
Common Attack Vectors
Script-based cyber-attacks have been gaining popularity since 2017 due to their ability to perform file-less attacks. These attacks usually involve only a small number of files during the infection chain; and in some scenarios no files may be involved in the infection chain at all.
Threat actors have begun using file-less attacks in greater frequency because they are more difficult to detect. Since most infection happens in the victims’ memory space rather than the file system, file-less attacks have a higher success rate at evading detection by anti-malware products, many of whom base their detection on filesystem scanning.
PowerShell is one of the best malware dropper options — with a simple script an attacker can easily download and execute payloads from the Internet. We have seen recent attacks involving PowerShell as a component for communicating with the C2 servers and downloading the payload to initiate the infection chain.
The Tools of the Trade
With the rise in popularity of PowerShell amongst red teams and pen testers—and after many successful attacks involving it—researchers and developers have started creating PowerShell post-exploitation frameworks. Using these frameworks, even individuals without in-depth knowledge of cybersecurity and OS internals can create legitimate threats.
Below is a short overview of the most popular frameworks:
- PowerShell Empire[2]
post-exploitation, open-source framework helps to achieve:
- Lateral movement (e.g. Pass-the-hash / Invoking PsExec)
- Credential dumping using Mimikatz
- Persistence
- User information collection (e.g. clipboard data and keylogging)
- Privilege Escalation through UAC Bypass
Although the project is no longer supported, the Empire framework offers several modules and features which make it a favorite amongst red teams.
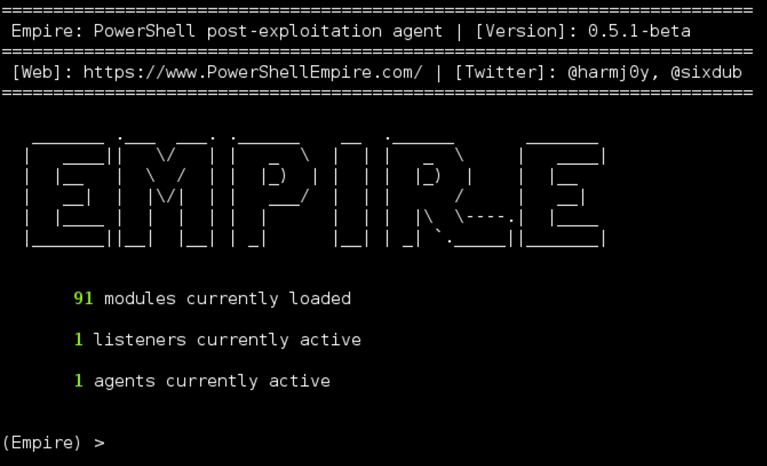
Figure 1 – PowerShell Empire framework (taken from
https://www.powershellempire.comNishang is another well-known post-exploitation, open-source framework that offers a set of attacking abilities such as:
- Creating backdoors on victims’ machines
- Escalating privileges in multiple ways
- Network scanning and brute force for lateral movement
- File-less attacks – executing malicious payload in memory
- PowerSploit[5][6]
is also a popular open-source, offensive framework that offers a variety of PowerShell modules and scripts. PowerSploit offers several benefits including:
- Audio capture using the Get-Microphone Audio module
- Keylogging using the Get-Keystrokes module
- Creating scheduled tasks for persistence using the New-User Persistence Option module
- It also includes a set of code-injection techniques
These frameworks offer a large collection of offensive capabilities that can potentially cause severe damage to organizations that are not aware of the risks.
There are many other open-source frameworks and paid products as well, including the notorious Cobalt Strike[7] paid penetration testing toolkit publicly leaked a few months ago which employs PowerShell in its Beacon component.
AMSI – How Does it Help?
Many of today’s attacks utilize PowerShell scripts that are obfuscated and difficult to detect. Starting from Windows 10, Microsoft has created an interface through which any anti-malware product can integrate. This interface is called AMSI – Antimalware Scan Interface.[8]
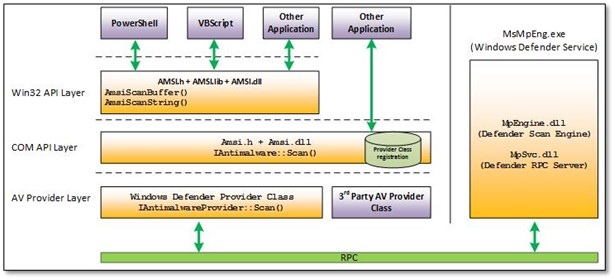
PowerShell scripts will often arrive encrypted, obfuscated, or will simply try to download the payload from a third-party website.
For simplicity, let’s say we want to prevent the execution of ‘Evil PS’ string. Heuristics and signature-based anti-malware would simply add a rule to block the desired string or regex and the following execution will be prevented:
- powershell.exe Write-Host 'Evil PS'
But what if we try breaking up the strings?
- powershell.exe Write-Host(("{1}{0}" -f 'v','E')+'i'+("{2}{1}{0}" -f 'S','P','l '))
Would all cyber security products still work? And what if we put more complexity into the equation and add simple base64 encoding?
- powershell.exe Write-Host([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String(("{1}{0}" -f 'pbC','RXZ')+'BQ'+("{2}{1}{0}" -f '=','w=','U'))))
And if that’s not enough we could still hide our payload in pastebin.com like I did in the following example (trust me, it’s there[9]):
- powershell.exe Write-Host([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String(("{1}{0}" -f 'zZUJhc2ljUGFyc2','KHdnZXQgLVV')+'luZyBod'+("{2}{1}{0}" -f 'IpLkNvbnRlbnQ=','9yYXcvTlZVa0tZOW','HRwczovL3Bhc3RlYmluLmNvbS'))))
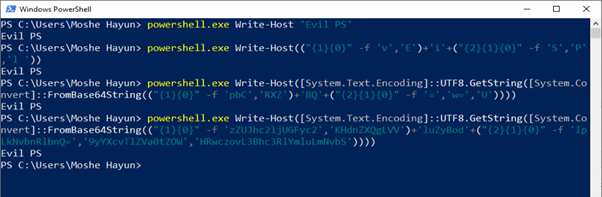
Figure 3 – PowerShell simple obfuscations[/caption]
Do Simple Obsfuscations Really Work?
In a PoV we conducted, we took one of the PowerSploit modules which uses Mimikatz for credentials harvesting and removed a single character at the end of line just to make it unknown on VirusTotal. We then uploaded it to test the results. 32 different engines in VirusTotal managed to detect it immediately.
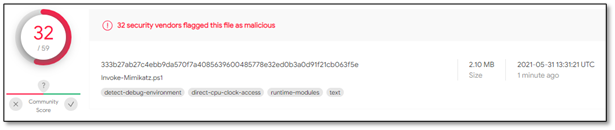
Figure 4 – Invoke-Mimikatz module on plain text
When trying to run the plaintext script, the Deep Instinct agent immediately detected it.
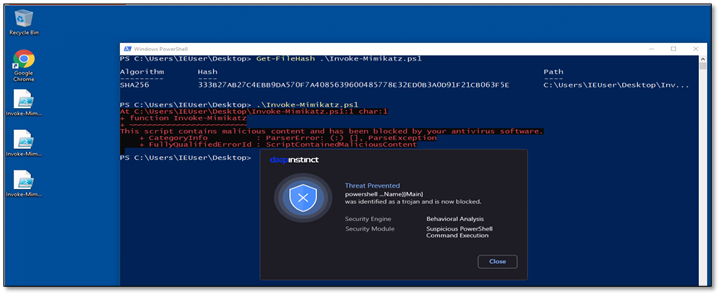
After simply base64 encoding the entire script and uploading it again, we managed to reduce the detection of a few more engines and dropped down to 11 detections.
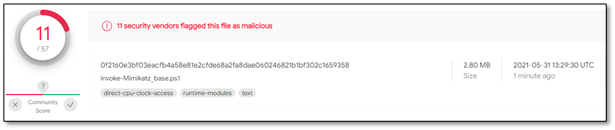
Figure 6 – Invoke-Mimikatz module after encoding with base64
In this example, the Deep Instinct agent is still able to detect the malicious payload.
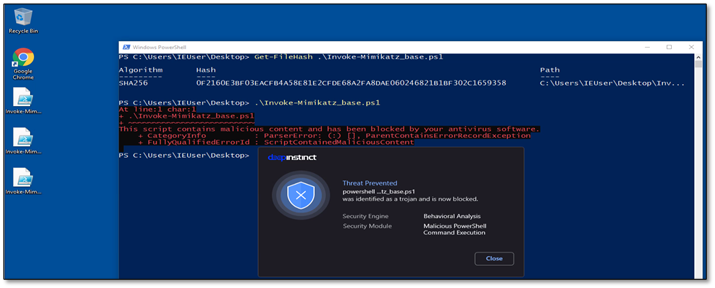
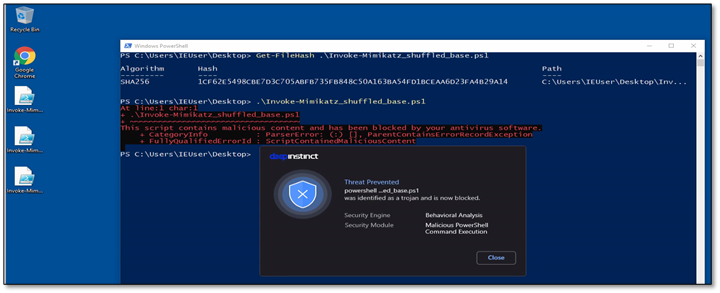
Eventually, we took the base64 Invoke-Mimikatz module, shuffled it using a few basic concatenating methods in PowerShell, and we got 0 detections in VirusTotal!
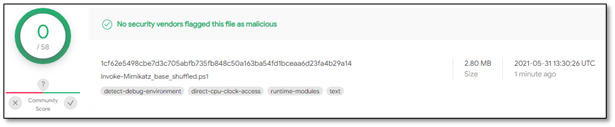
Figure 8 – Invoke-Mimikatz module after encoding and shuffling the data
Although we played with the file and tried to hide its true nature, the Deep Instinct agent still detected a risk and tagged this script as a Malicious PowerShell Command Execution.
The purpose of AMSI is to strip attackers of the ability to enable cybersecurity vendors to focus on the payload and not on the encryptions and obfuscations.
In order to use the AMSI interface, Microsoft has released documentation guides for developers and researchers.
Although there have been few successful attempts to bypass AMSI detections, it is still a strong interface that can assist in preventing most of the PowerShell attacks.
Deep Instinct vs PowerShell
Deep Instinct has several solutions to handle PowerShell attacks. In addition to behavioral protection mechanisms, Deep Instinct prevents malicious PowerShell scripts through the deep learning that lies at the core of our neural network technology. This allows us to detect known and unknown threats, including those that are PowerShell based.
If you’d like to learn more about our industry-leading approach to stopping malware, backed by a $3M guarantee, please download our new eBook, Ransomware: Why Prevention is better than the Cure.
References:
[1]https://github.com/PowerShell
[2]https://github.com/EmpireProject/Empire
[3]https://github.com/samratashok/nishang
[4]https://kalilinuxtutorials.com/nishang/
[5]https://github.com/PowerShellMafia/PowerSploit
[6]https://attack.mitre.org/software/S0194/
[7]https://deepinsarchive.wpengine.com/2021/03/18/cobalt-strike-post-exploitation-attackers-toolkit/
[8]https://docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal
[9]https://pastebin.com/raw/NVUkKY9b

