Ursnif ups its game with sophisticated VBA and PowerShell combination Dropper
Intro
Ursnif (AKA Gozi), is one of the most enduring pieces of malware in the cybercrime threat landscape, being active for well over a decade now. Its code has been leaked repeatedly and has been used, modified and upgraded extensively; giving rise to many different yet similar variants of this banking malware which are delivered primarily through spam Emails with malicious attachments.
Deep Instinct recently prevented Ursnif being delivered to a customer environment by means of a sophisticated dropper which is disguised as a DHL invoice.
The Dropper
As mentioned above, the dropper, an Excel Spreadsheet, is designed to appear like a DHL invoice, which when opened prompts the user to enable the VBA macro contained.
Once the macro is enabled, it is executed and presents the victim with a decoy progress bar, likely intended to make the malicious document appear more legitimate and stall the victim while the malicious code is being executed.
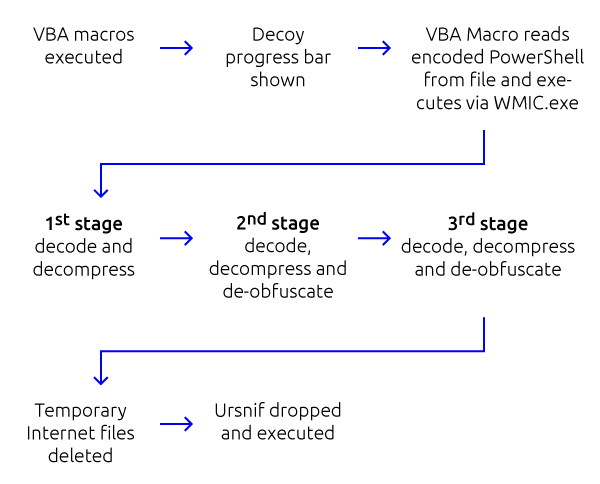
General infection and de-obfuscation flow is as follows:
[caption id="attachment_5888" align="aligncenter" width="739"]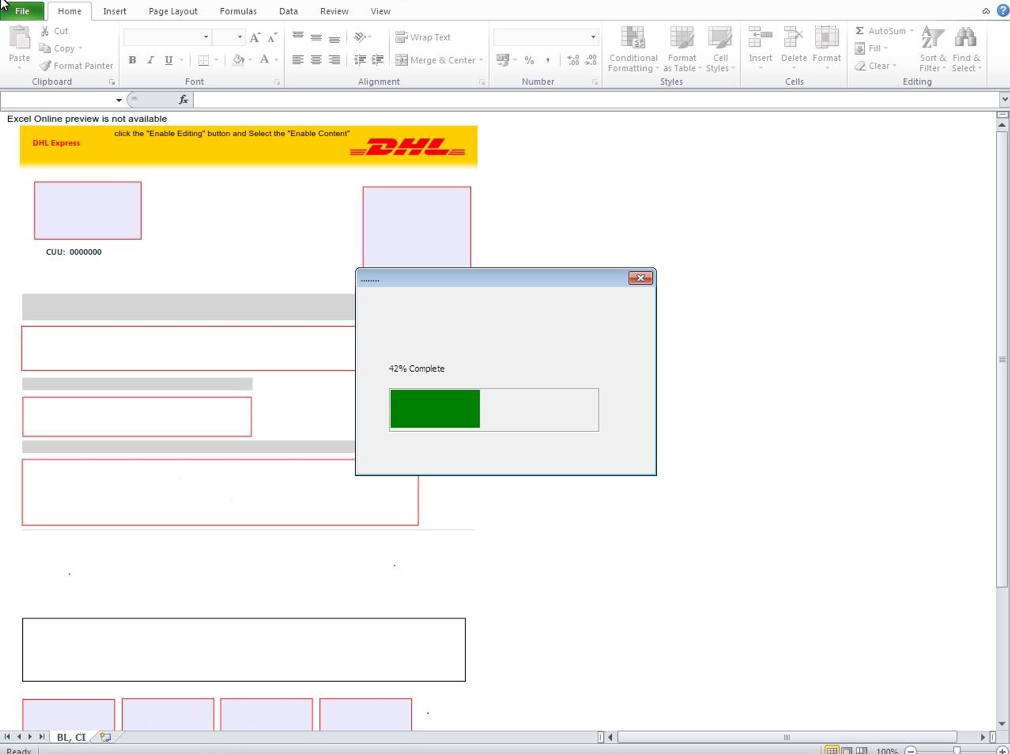 Decoy progress-bar displayed to victim after macros are enabled[/caption]
Decoy progress-bar displayed to victim after macros are enabled[/caption]
The VBA macro is obfuscated and contains many random-generated “comments” intended to make the code appear more legitimate and lower the chances of it being caught by security vendors.
[caption id="attachment_5879" align="aligncenter" width="600"]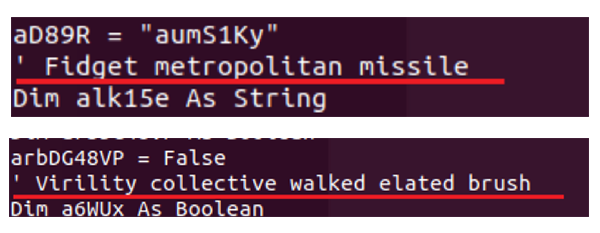 “Comments” intended to make the code appear more legitimate[/caption]
“Comments” intended to make the code appear more legitimate[/caption]
After the decoy progress bar is presented to the victim, the VBA macro reads a portion of the Excel file, which contains a compressed and base64 encoded PowerShell command, which is in turn executed by WMIC.exe (Windows Management Instrumentation Command-Line Utility) after being called for by the VBA using a Shell() function.
[caption id="attachment_5885" align="aligncenter" width="920"]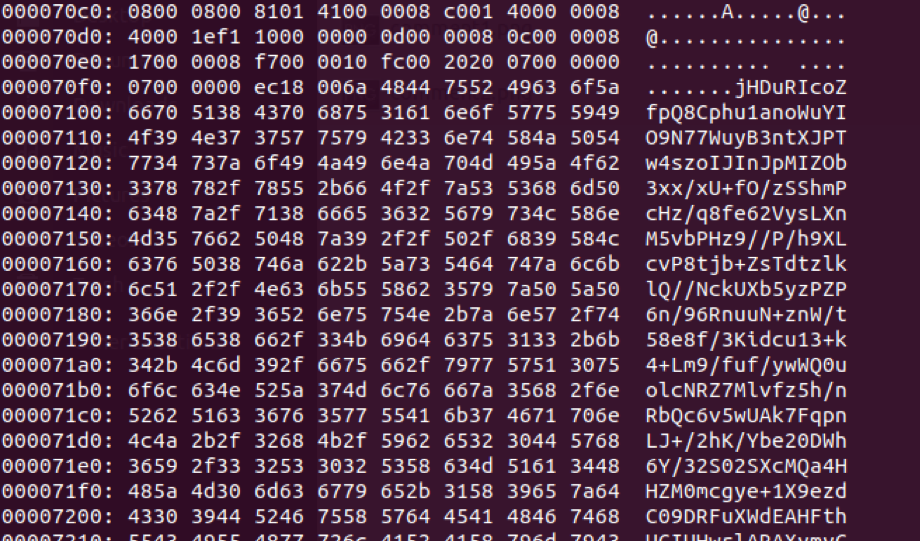 Compressed and base64 encoded PowerShell command contained in the Excel Spreadsheet[/caption]
Compressed and base64 encoded PowerShell command contained in the Excel Spreadsheet[/caption]
[caption id="attachment_5886" align="aligncenter" width="1093"]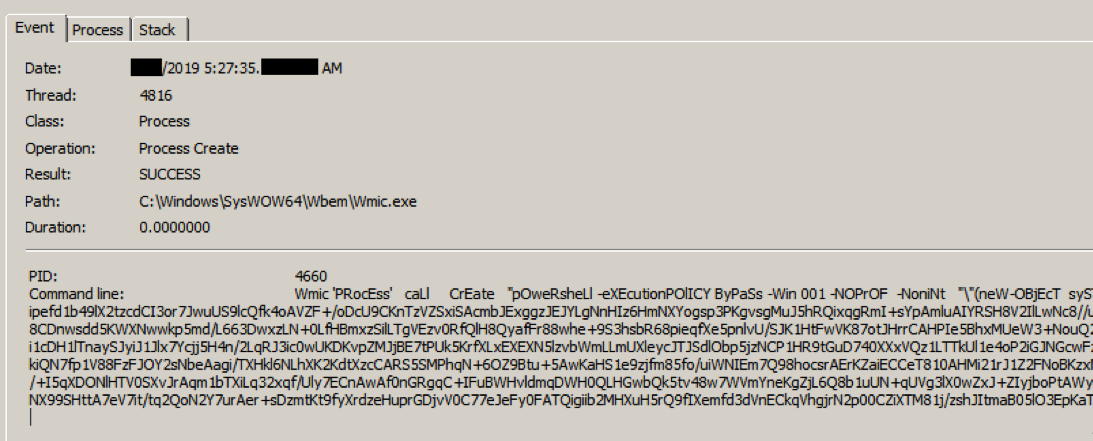 WMIC.exe executes PowerShell.[/caption]
WMIC.exe executes PowerShell.[/caption]
Analysis of this PowerShell code reveals complex, heavily obfuscated dropper code, with multiple layers of compression, encoding, and obfuscation.
Decoding and decompressing the initial command blob (shown above) reveals two similar compressed and encoded blobs, which are piped to a function named “ms”.
[caption id="attachment_5887" align="aligncenter" width="560"]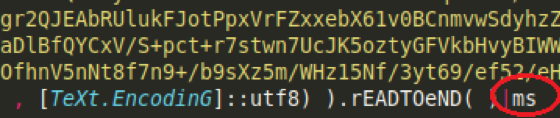 Function “ms” receives decompressed blob content[/caption]
Function “ms” receives decompressed blob content[/caption]
Replacing this function with a print function enables us to see the content of these blobs and some initial functionalities are revealed, as well as an additional obfuscated blob and an initial de-obfuscation loop, after which the code is again piped to function “ms”.
[caption id="attachment_5880" align="aligncenter" width="600"]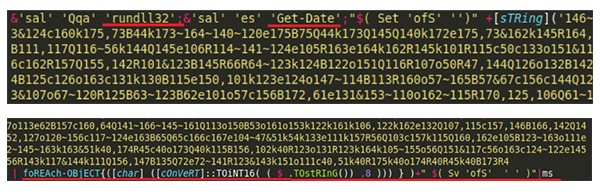 Initial functionalities (rundll32, get-date), initial de-obfuscation loop and again pipe to function “ms”.[/caption]
Initial functionalities (rundll32, get-date), initial de-obfuscation loop and again pipe to function “ms”.[/caption]
Repeating the function replacement trick enables to us to see below this 2nd layer of obfuscation and reveals another de-obfuscation function and yet another compressed and encoded blob, with the end result again being piped to function “ms”, again.
[caption id="attachment_5881" align="aligncenter" width="600"]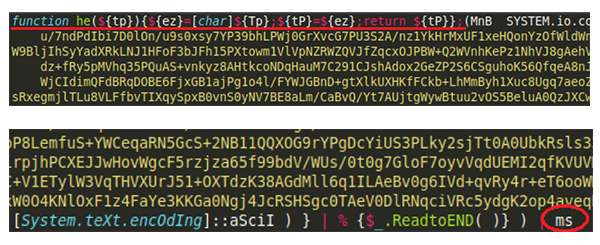 De-obfuscation function (character replacement), final pipe to function “ms”.[/caption]
De-obfuscation function (character replacement), final pipe to function “ms”.[/caption]
Decoding and decompressing the above blob, finally reveals function “ms”, which itself is obfuscated, however, some light manual de-obfuscation will readily reveal the code’s final functionality:
[caption id="attachment_5882" align="aligncenter" width="600"]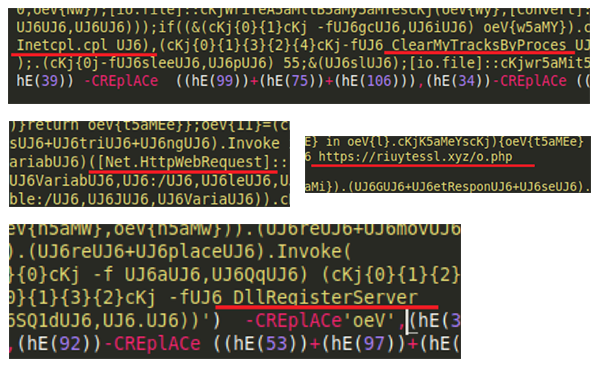 Final main functionalities – delete temp internet files, download and execute payload from URL.[/caption]
Final main functionalities – delete temp internet files, download and execute payload from URL.[/caption]
The end result of the above is as follows:
- Execute: rundll32.exe InetCpl.cpl ClearMyTracksByProcess 8
This deletes temporary internet files (top image above)
- Download executable payload file from hxxps://riuytessl.xyz/o.php?<current_timestamp> to %appdata%/Local/Temp/ (middle images in above)
- Execute: rundll32.exe /s <downloaded_file_path>, DllRegisterServer
This executes the payload, after which Ursnif will launch its own instance of iexplore.exe and will attempt to reach its C2 server. (bottom image in above)
Ursnif payload
The Ursnif payloads are delivered to the victim by a mutation “factory” very similar to what we reported approximately 8 months ago.
While each file is individually unique (has a unique file hash in order to circumvent file-reputation based mechanisms), much like what we previously reported 8 months ago - the mutation is limited to a single file section (.text), with the other file sections being exactly identical.
[caption id="attachment_5883" align="aligncenter" width="600"]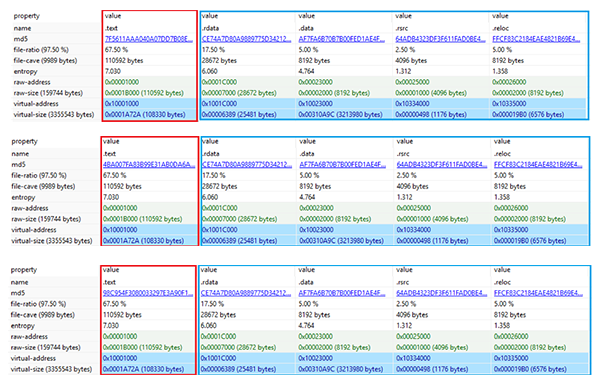 In red – mutated .text section, in blue – identical sections.[/caption]
In red – mutated .text section, in blue – identical sections.[/caption]
Additionally, all of the mutated samples feature the function same exports and share the same fake file metadata
[caption id="attachment_5884" align="aligncenter" width="600"]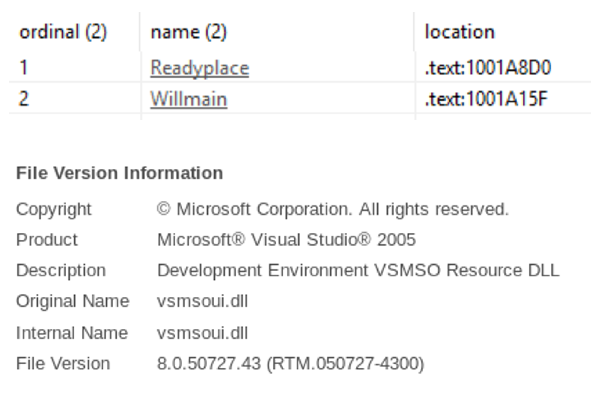 Functions exported by Ursnif, Common Ursnif file metadata[/caption]
Functions exported by Ursnif, Common Ursnif file metadata[/caption]
Summary
All the effort that Ursnif’s operators have put into their mechanism for delivery, appears to have paid off and been well worth it. When this dropper was first uploaded to VT (slightly after we had prevented it in a customer environment) it was only detected by six out of 57 scanning vendors. This case highlights how threat actors are using increasingly sophisticated techniques to ensure that their malware is not detected and that analysis post-detection is much more complicated.
IOCs
Dropper, prevented and investigated sample
950841a89bb1d56e69eac5d320db7f76d74be1f2a53100194900f5dbbe21fe2b
Similar droppers from threat intel data
2f4e7dba21a31bde1192ca03b489a9bd47281a28e206b3dcf245082a491e8e0a
01aad214937a6a59200b96ff1e5a7736617cc204cfeb6eb5975ee3835993b76e
169002b38eb064ae2be7f04391ddf05929cbef94da1ea63bf19de4249e1241ae
b259b9da39a090fd2c605078dce36a5180620be17ad4f8fe1331beb7446fb7ec
Ursnif payloads
0b49302a5ddb8de03a3547c8a4ff7f900ff433bc0f3bc489d7548419075d05b6
251fd3548c5668250e8b7c1bbe7bbd24dff0573ec6f68e42ce19d91f6c468e90
2e358979ffcdda15f4c399cb0dfe502177f611193bb6dd26146dd2051ebd209b
48787fc23a844d0f9d28301caa2c06236d2bdf175b2f7b9f404095a9da9f91bf
513e2d4293dbe2be5d22ea9db7642b97678e12856a7d1141a55e87c9acd06b8d
53c6e56d88792a04513644d1e2fbd1fb4944e74a18a6c52c5245946bf4077344
6628e40e470faf394351353212c63ff9211486f7305f3e1b5730ba408557498f
6d21b25a738bfe75602da344fdedac5b13d08720e83f0e47e54a5999ab056ef8
76516c3aeeab238cb03152def2e78d14cac1cbf6c3bbf68740328c54d5d1e562
775e3dc524453dd563f8a8d48ffb2574f156d9704ad4e4277518267ad9c5a6b0
8f462abcf57b0fa215ec14b4cc7fce8cb22c54b5405c8490e8baa07de215b466
ae7d806f94fd5c5a2b614b8dcc5e5e6750e9a591206595cc2f14a67e987454e2
b4aa944de735fec4cc644aac85cb2f4646d730c6a14574acb857f899a653e90b
d3c317ca9aea2ae1fcfcdd2468725f12b9ec2d75e01010595ccae6b0b67eb87b
d44ffe507c21241f6782c95eb44b45827cadb17aace7ccd4dcb49b76c541ce2b
d6458426892f9c8fb80ca14e685bdf491022cc4896c455489440a3f90da5731b
da3d96cbdfff3f49ba9bdda109f927e6f241861eff5770c67719879552a0ca2d
de5cd6b3f410035b43abd6a8988c484ffe46eacfb81a5ca938a5a00f05852831
ee05b5ea7082fedb1052b999c1e3b2f9746b755da978d39983e31095e756685f
fb8d1f54615dec4fc97dbb36bfe816bb01c189c341f385e6f7dc9be1303e1381
Mutation “factory”
hxxps://riuytessl.xyz/o.php
Ursnif C2
hxxp://irwhfgowe.xyz

