Stopping PrintNightmare
[7/11 Update] Although Microsoft have released the KB5005010 security update that should resolve the PrintNightmare issue. Researchers have managed to completely bypass the security update and achieve both LPE and RCE on a fully patched system. In order to bypass this patch, the ‘Point and Print’ Windows policy must be enabled.
Last week was a busy one in cyber circles, with the Kaseya VSA ransomware outbreak and PrintNightmare both highlighting significant network threats for organizations.
PrintNightmare refers to a vulnerability in the Windows Print Spooler – an exploit that many may remember as the attack method used to destroy Iranian nuclear centrifuges more than a decade ago. This new vulnerability is actually two-pronged: the first is local privilege escalation, allowing a third party to establish admin or system-level rights to a computer from only low-level privilege, and the second allowing for remote code execution access.
PrintNightmare begins (CVE-2021-1675)
In early June, Microsoft addressed a vulnerability in the Windows print Spooler service. It first appeared with a medium CVSS score of 6.8 and was listed as a LPE (local privilege escalation) vulnerability.
Double trouble: from LPE to LPE + RCE
A week after the vulnerability was surfaced by Microsoft, the researcher who discovered the flaw published a video where he is allegedly demonstrating that CVE-2021-1675 is not just an LPE vulnerability but also a RCE vulnerability.
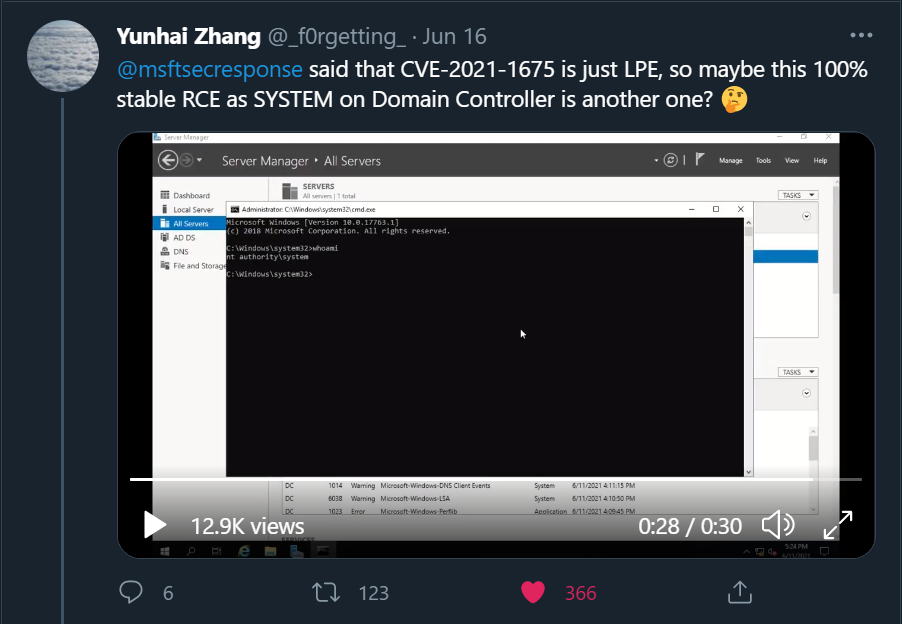
CVE-2021-1675> CVE-2021-34527
About two weeks later, on June 21, the CVSS score of CVE-2021-1675 was updated from a medium 6.8 to a critical 7.8, and the definition was updated from an LPE to RCE. In addition, a new CVE identifier was issued – CVE-2021-34527, also known as PrintNightmare.
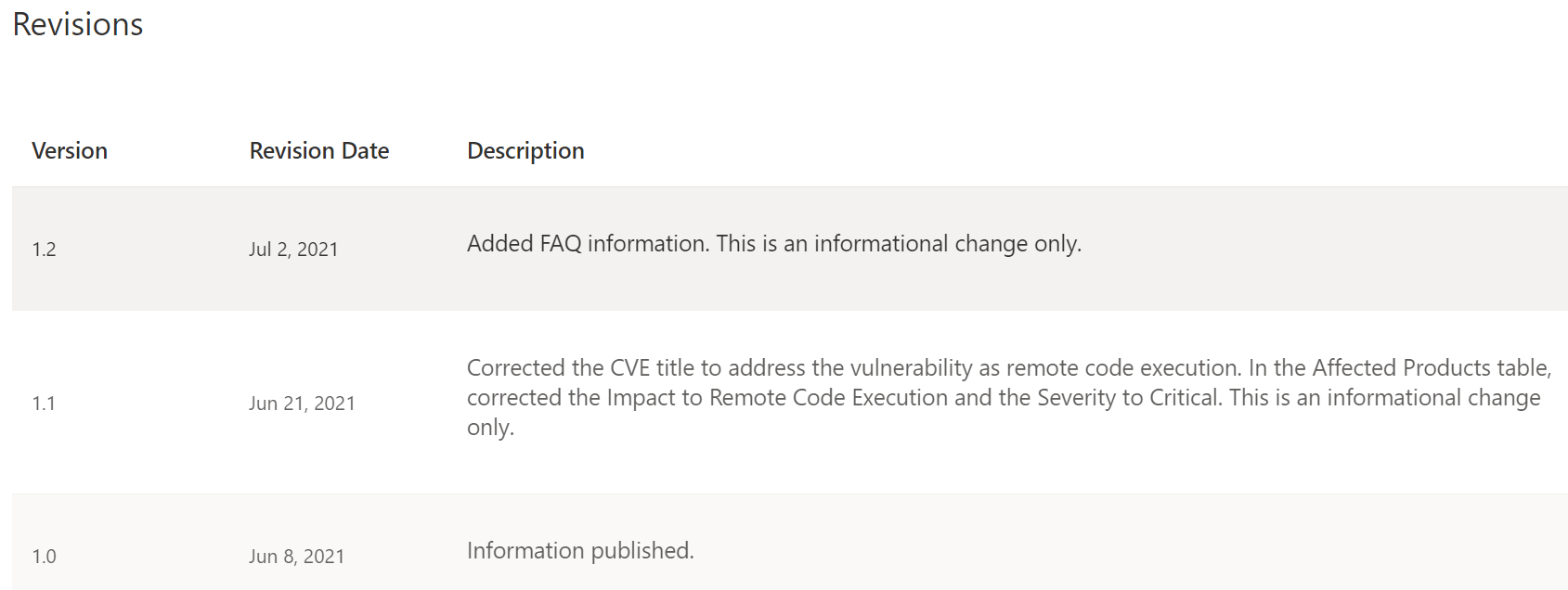
Now things get interesting. Microsoft issued two different CVEs on the same service in less than a month. According to Microsoft, these two CVEs are similar but distinct as they address different vulnerabilities in the RpcAddPrinterDriverEx function. The attack vector is also different.
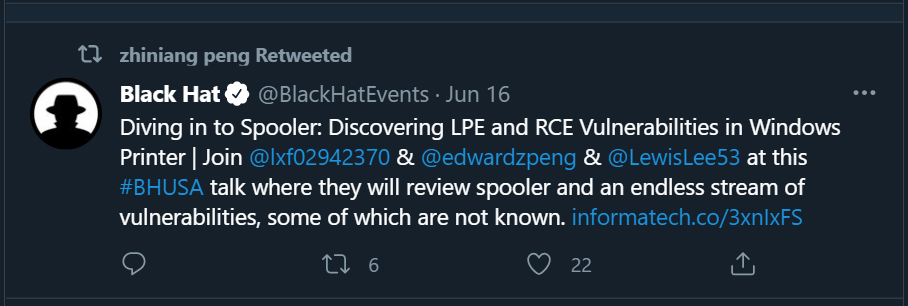
In mid-June another researcher from Sangfor security team retweeted a tweet from BlackHat’s official Twitter account announcing a research talk that would be given at BlackHat Las Vegas this year entitled, ‘Diving in to Spooler: Discovering LPE and RCE Vulnerabilities in Windows Printer.’
Will they present what we already know as PrintNightmare? Or perhaps the presentation will show that the spooler service is more vulnerable than first thought, bringing the potential for more vulnerabilities to come? The presentation is scheduled for August 8th, so this question will remain until then.
On June 29th another tweet and video was posted by the QiAnXin security team on Twitter showing a full RCE demo of CVE-2021-34527, but without any technical details. A researcher from Sangfor security team then published (some claim by accident) a public exploit POC to his GitHub account. After realizing their error – an unpatched exploit which is enabled by default on every Windows OS and a jackpot for hackers – they quickly removed this repository.
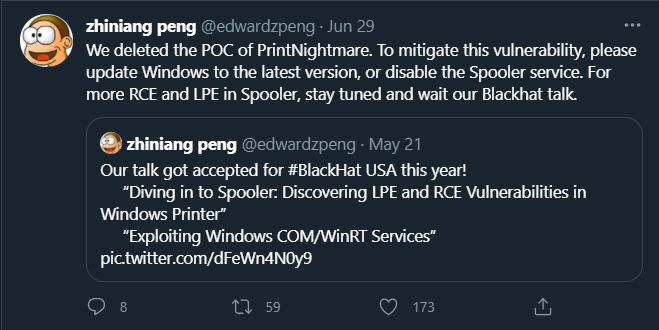
Figure 4 – the researcher who published the POC of PrintNightmare saying he deleted it[/caption]
But the damage had been done; by the time they removed the POC the code had been forked many times.
Here are a few working examples:
- https://github.com/afwu/PrintNightmare
- https://github.com/cube0x0/CVE-2021-1675
- https://github.com/calebstewart/CVE-2021-1675
Unfortunately, security updates for Windows Server 2016, Windows 10, version 1607, and Windows Server 2012 will be delayed for a short period, but they are expected soon.
What is the flaw and how can exploit be prevented?
The root cause of this vulnerability is at a function called RpcAddPrinterDriverEx, a simple function that is designed to allow users the ability to have remote printing.
To understand why this threat is so serious, let’s unpack two basic facts about print drivers:
- Print drivers have full execution abilities as a system on the machine by design.
- There is a flaw on the remote authentication function which allows any authenticated user to add a print driver, remotely. (the notorious PrintNightmare) Again, this is important because even users who have gained low-level access can attain admin or system-level access with this exploit.
Combining these two facts we now have an unpatched vulnerability where any authenticated user can gain full remote code execution abilities with system privileges.
The first question many will ask is a good one: Will Microsoft patches protect me?
While Microsoft’s patch doesn’t solve the issue completely, a combination of the patch and the right mitigations will provide strong protection.
The cyber security community joined forces and formed a scenario flow chart (below) to demonstrate when the exploit will work and when it will fail.
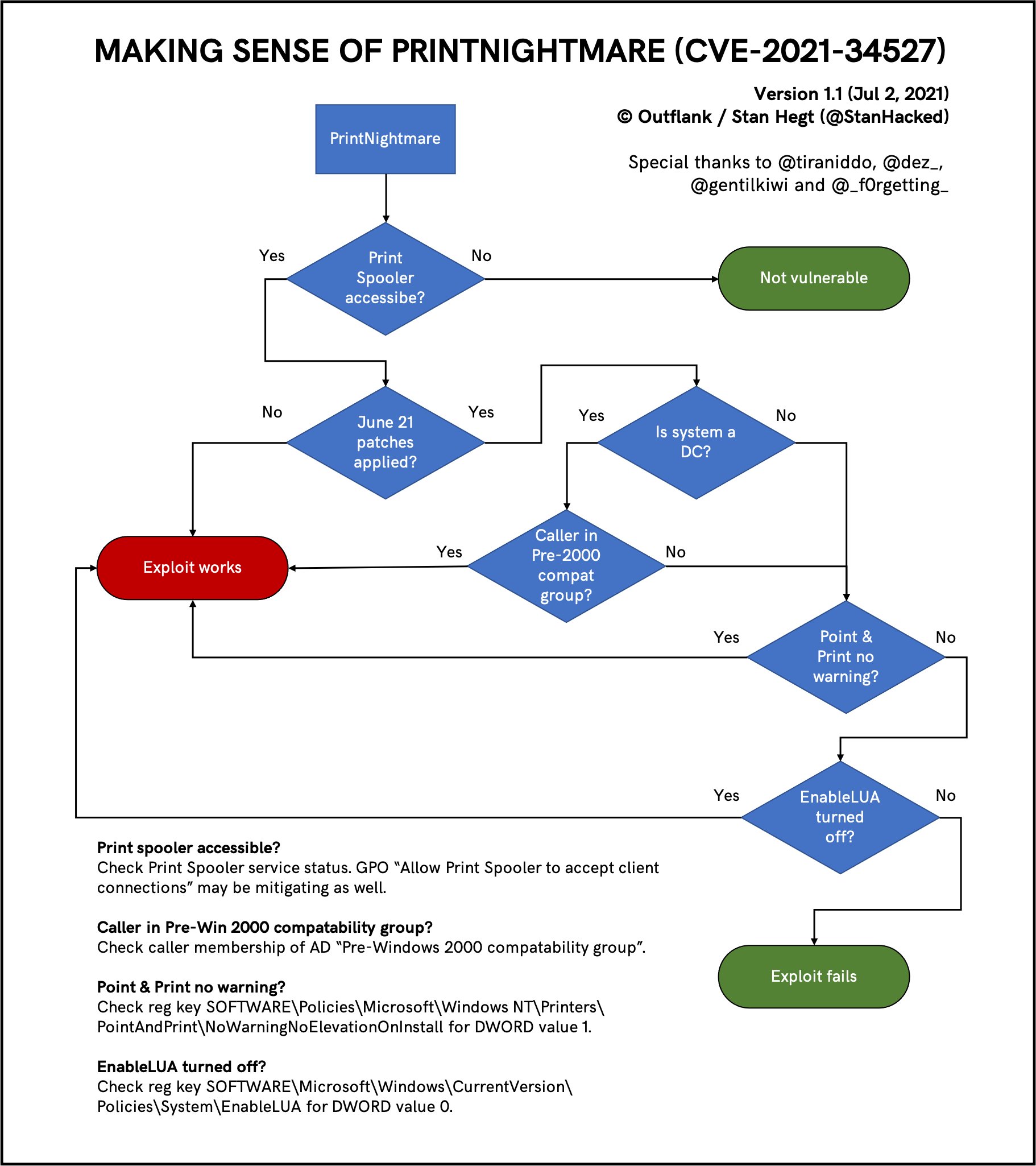
Further mitigations beyond the patch
As you may have noticed in the flow graph, in a case where the print spooler is inaccessible, the entire exploit is irrelevant. Therefore, another way to defend your organization against this exploit is to disable the spooler services on machines where this feature is not required.
Disabling this service can be done via Group Policy on Windows 10 or through PowerShell using two simple commands.
Stopping the service: Stop-Service -Name Spooler -Force
Disabling it from startup: Set-Service -Name Spooler -StartupType Disabled

How can Deep Instinct help you?
The nature of this attack allows bad actors to potentially gain reverse shell to perform scripting-based attacks or use them as droppers for additional payloads.
Deep Instinct has several solutions to handle these attacks. Deep Instinct Script Control policy can block these kinds of attacks. In addition, Deep Instinct prevents malicious scripts in pre-execution through the deep learning that lies at the core of our neural network technology. Not only do we prevent threats of this nature, we prevent zero-day malware and ransomware – and back our no-ransomware promise with a $3M guarantee.
You can learn more about our prevention-first approach in our new eBook, Ransomware: Why Prevention is better than the Cure. Or you can speak with a sales rep by requesting a demo to see our tech in action.
References:
https://twitter.com/gentilkiwi/status/1412771368534528001
https://www.wired.com/story/microsoft-keeps-failing-patch-windows-printnightmare-bug/

