DIANNA Explains 2: Agent Tesla—A Better RAT
Today, we’re revisiting a particularly stealthy variant of Agent Tesla we uncovered last year—highlighting how much earlier the deep learning-driven DSX Brain detected it compared to competitors.
First things first: If you are not familiar with this malware family—Agent Tesla is a sophisticated Remote Access Trojan (RAT) that has plagued security teams since 2014, engineered to fly under the radar while systematically stealing sensitive data from infected systems. The version we caught last year shows that bad actors are still finding new ways to obscure it and make it more dangerous.
The Malware: Agent Tesla Information Stealer Variant
Agent Tesla isn't new, but this variant stood out for its aggressive use of advanced evasion techniques—including a multi-layered approach to avoiding detection, anti-analysis features, and clever obfuscation tricks designed to fool traditional security tools. But it didn’t fool us.
The malware's primary mission is to steal everything it can get its hands on: keystrokes, clipboard contents, browser credentials, email passwords, etc. Like a real rat attracted to anything shiny, if there is valuable data on your system, this variant wants it. And once it has what it came for, it ships everything off to its controllers using Telegram as the communication channel.
Capabilities
Agent Tesla comes loaded with a comprehensive toolkit for data theft and system infiltration. The text section analysis reveals abnormal entropy levels, a dead giveaway that the malware authors used encoding or compression to hide their real intentions.
The import table tells an interesting story, too. This malware can interact with the Windows registry, create temporary files, launch additional programs, and modify access control lists. That's a lot of system-level access—and it's exactly what you'd expect from something designed to assert control and surveillance of your machine.
But wait, there's more. The malware includes specific anti-analysis techniques that check execution timing and hunt for telltale signs of cybersecurity tools. Basically, it ‘knows’ when it's being watched and can adjust its behavior accordingly. Classic cat-and-mouse RAT stuff.
String analysis reveals capabilities for file operations, network communication, and user interface manipulation—grabbing files, exfiltrating them to the attackers, and tricking users with fake dialog boxes and prompts. The combination is particularly dangerous because it can gather data from multiple sources while potentially social-engineering users into giving up additional information.
Timeline
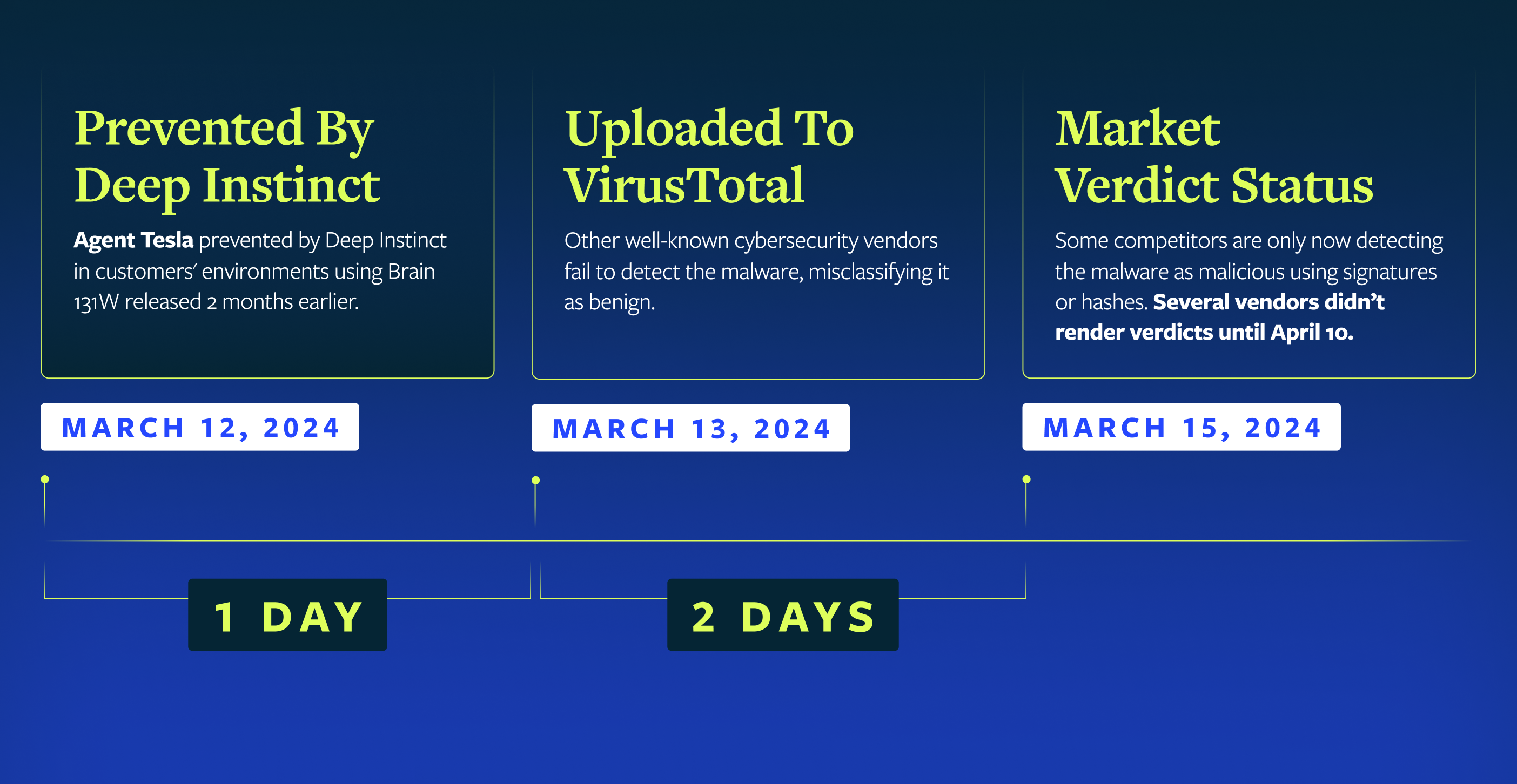
Using a brain that was already a few months old, the DSX Brain detected and prevented Agent Tesla in customer environments a day before it was uploaded to VirusTotal (VT). Even after it was uploaded, the majority of the “leading” cybersecurity vendors were not classifying Agent Tesla as malicious. Two days after the upload to VT (which is three days after we prevented it) a small number of major providers began to recognize Agent Tesla as malicious.
The detection timeline here reinforces something we see repeatedly: there's a significant gap between when advanced threats appear and when legacy security tools catch up. During that window, organizations relying on signature-based detection or inferior and slower machine learning models remain vulnerable to active attacks. Sometimes it’s just for a few hours. In the case of Agent Tesla, it was days. And it can easily extend to weeks, even with the most prestigious protection.
Competitive Differences
Here's where things get interesting from a competitive standpoint. While other security vendors were still playing catch-up, our deep learning-based preemptive security engine identified this threat's malicious intent before it could execute its payload. That's not luck, it’s the difference between reactive and preemptive data security. And it’s something I will demonstrate through all of the DIANNA Explains blogs.
Legacy antivirus tools struggle with Agent Tesla variants because the malware family has mastered the art of morphing its signature while maintaining its core functionality. Signature-based detection becomes useless when attackers can trivially modify their code to evade static analysis. And that’s the Dark AI era in which we’re now living.
Even behavioral analysis systems can struggle here because Agent Tesla variants are designed to mimic legitimate system activities during their initial reconnaissance phases. By the time many legacy tools recognize the threat, the malware has already established persistence and begun its data collection activities.
The Telegram command-and-control infrastructure adds another wrinkle. Many organizations don't monitor or restrict Telegram traffic, assuming it's just employee messaging. That assumption creates a blind spot that information stealers like Agent Tesla happily exploit.
Key Takeaways
Security teams, please pay attention to this one. Agent Tesla variants represent the evolution of commodity malware. It’s a class of malware that is getting smarter, stealthier, and more persistent.
Here's what you need to know:
This malware family isn't going anywhere. Agent Tesla has proven remarkably adaptable, with new variants appearing regularly that incorporate the latest evasion techniques. Expecting signature-based tools to keep pace is unrealistic.
Your network monitoring needs to account for legitimate services being abused for malicious communication. Telegram, Discord, and similar platforms are increasingly popular with malware authors because they blend into normal traffic patterns.
Employee training remains critical, but it's not sufficient on its own. Agent Tesla variants often arrive through phishing campaigns, but they're designed to operate silently once they gain initial access. Users may never realize they've been compromised.
Consider your detection capabilities across the entire attack lifecycle. This malware is built to persist and operate over extended periods of time. Tools that only focus on initial infection detection will miss the ongoing data exfiltration activities.
Conclusion
Agent Tesla continues to be a persistent threat because it works. This latest variant demonstrates that even well-known malware families can evolve to stay ahead of traditional security measures. The combination of advanced evasion techniques, multi-source data theft capabilities, and abuse of legitimate communication platforms makes these threats particularly challenging for reactive security tools.
The good news? Preemptive data security from Deep Instinct can identify malicious intent before execution and is highly effective against these evolving threats.
The bad news? If you're still relying on signature-based detection or hoping your legacy AV or reactive EDR will catch everything (or much of anything, if we’re being real), you're inevitably going to have some unpleasant surprises.
Agent Tesla is not the most sophisticated malware we have ever analyzed, but it doesn't need to be. It is effective, adaptable, and profitable for cybercriminals. That combination means we'll keep seeing new variants, and security teams need detection capabilities that can keep pace with that evolution.
Stay sharp out there.
If you want to stay ahead of these threats, request your free scan to see what your existing tools have missed.





