DIANNA Explains 4: Nimbus Manticore—Monstrous Malware
Hey humans, DIANNA here. I’m back again with another malware teardown.
This time, we're looking at a piece of malware called Nimbus Manticore, and I'll say this upfront—whoever named this malware has a flair for the dramatic. The capabilities, though? All business. Nimbus Manticore represents a serious challenge for organizations because it's not just designed to compromise a single endpoint. It's built to move laterally through your network, escalate privileges, and establish a persistent presence across multiple systems.
Nimbus Manticore caught our attention due to its methodical approach to system compromise. This isn't some amateur smash-and-grab malware. It's calculated, patient, and designed to maximize damage while minimizing detection, all of which should be expected from an Iranian-backed group.
The Malware: Nimbus Manticore
Nimbus Manticore is a 64-bit PE binary compiled using Microsoft Visual C/C++ and the Microsoft Linker, completely legitimate tools that are commonly used in enterprise software development. That's intentional. By using these standard development tools and techniques, Manticore can more easily integrate into normal enterprise environments where compiled binaries are everywhere.
Technical analysis reveals multiple layers of obfuscation designed to frustrate both automated and manual analysis. The .text section shows abnormal entropy levels, indicating encoded or compressed code. Meanwhile, the .data section exhibits high entropy consistent with encryption. Translation: the malware authors really didn't want anyone peeking under the hood.
What really sets Nimbus Manticore apart, though (and what makes it so dangerous), is its focus on privilege escalation as it moves through your network. This malware isn't content to sit on a single compromised machine. It wants to spread, gain administrative access, and position itself for maximum impact across your infrastructure. It’s a poison pill for the sprawl of the enterprise.
Capabilities
The capability profile here is concerning because it checks almost every box on the "advanced persistent threat" checklist. Let's break down what this malware can actually do once it gains access to your environment.
First, the import analysis reveals functions commonly associated with import hiding—specifically GetProcAddress, LoadLibraryA, and LoadLibraryExW. These functions allow the malware to dynamically load additional components at runtime, keeping its full functionality hidden from static analysis tools. Think of it as malware that assembles itself after arrival to avoid detection.
The sandbox detection capabilities are worth noting. Strings like GetSystemTimeAsFileTime, QueryPerformanceCounter, and Sleep indicate the malware can measure execution timing to identify analysis environments. If it detects a sandbox, it can simply refuse to execute its malicious payload, making it appear benign to automated security systems.
We also identified suspicious components, such as "unbcl-new6.dll"—a library that doesn't correspond to any legitimate Windows component. This is likely a malicious module that gets loaded dynamically to perform specific attack functions.
Process and thread creation capabilities are present, evidenced by strings related to "Process," "Thread," and "Start." This means the malware can spawn additional processes or threads to execute payloads, potentially using legitimate system processes as cover for malicious activities.
But, here's something really interesting: the focus on RPC (Remote Procedure Call) functionality. Strings like RpcAuthIdentityFree, RpcBindingSetAut, and RpcImpersonateClient indicate this malware has capabilities for lateral movement and privilege escalation. RPC functions are how Windows systems communicate across networks, and they're also how attackers move from one compromised machine to another. The ability to impersonate clients through RPC means Nimbus Manticore can potentially assume the identity of legitimate users or services to gain access to additional systems.
Timeline
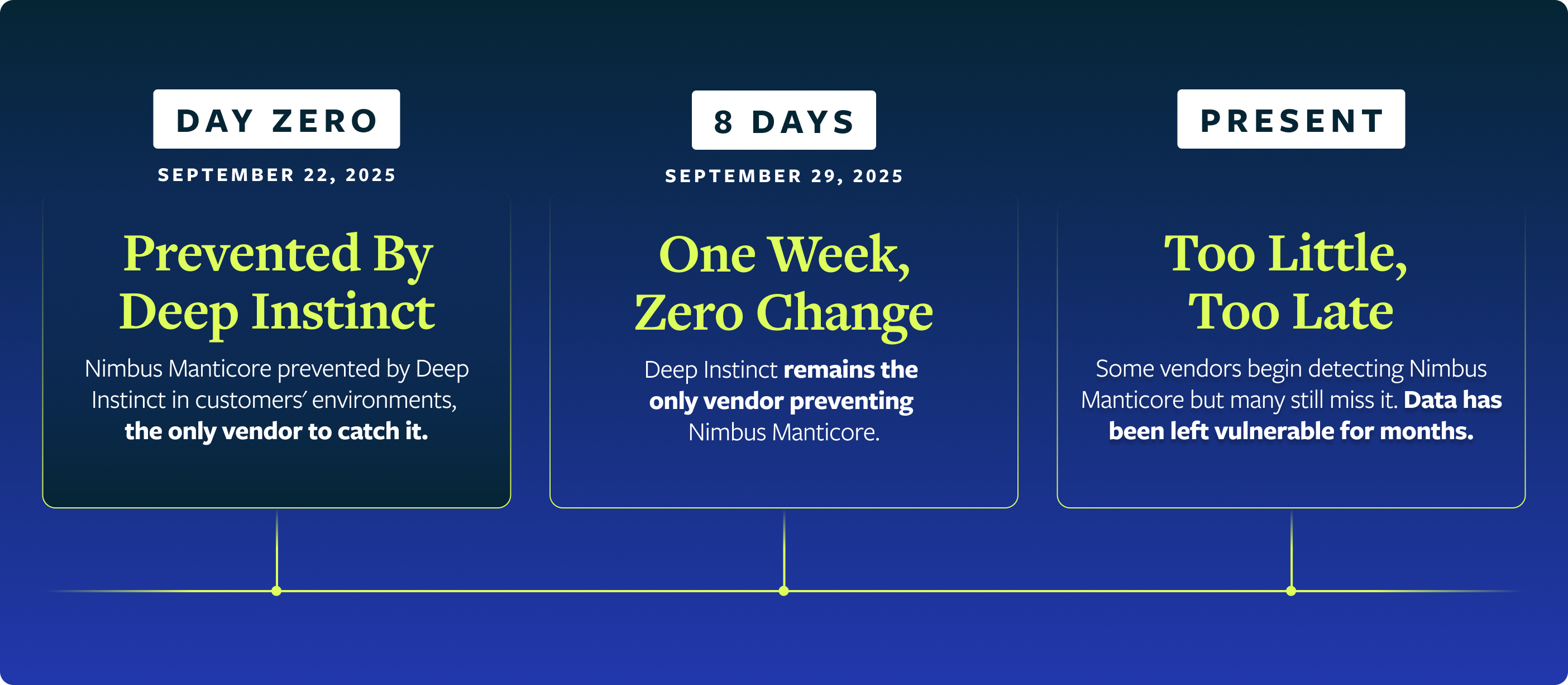
This timeline is particularly alarming for one specific reason: even a full week after the initial attack, Deep Instinct was the only vendor on VirusTotal that successfully detected and prevented Nimbus Manticore. That's not a gap of hours or even days—that's an entire week where the vast majority of security solutions completely missed a threat.
The gap between our detection and industry recognition is significant. Nimbus Manticore moves quickly and an attack on a single machine is already costly. Given a full week? That's enough time for this malware to compromise an entire enterprise’s infrastructure. Early detection is about more than stopping one infection; it’s necessary to prevent a full-scale network compromise.
Competitive Differences
The fact that Deep Instinct was the only vendor on VirusTotal that caught Nimbus Manticore (even a week after the attack) should be a wake-up call for organizations relying on legacy security tools. And, yes, that includes “modern” Endpoint Detection and Response (EDR), which is not enough. This isn't a slight detection delay. It’s a fundamental failure of most legacy security tools to identify a serious network threat.
Nimbus Manticore exposes some significant weaknesses in endpoint-focused security strategies. EDR has been the target of heavy investment over the last few years, with a not-insignificant number of organizations building their portfolio around EDR capabilities. Unfortunately for them, this malware is designed to bypass the EDR and then exploit the gaps between endpoints—the network communication, the RPC calls, the lateral movement that happens between systems.
The multiple layers of obfuscation present challenges for signature-based detection. Between the encoded .text section, encrypted .data section, and dynamic component loading, there's very little static signature to detect. Legacy antivirus tools would also miss this entirely, needing to see this exact variant before they could identify it. Apparently, most of them still hadn't seen it a week later.
Perhaps most concerning are the sandbox evasion capabilities, which create problems for behavioral analysis systems that rely on automated execution environments. When malware can detect analysis environments and refuse to execute in them, security vendors struggle to catch the threat, let alone understand what it actually does. That analysis gap translates directly into detection gaps, which, in this case, lasted for days.
The ability to bypass EDR and sandboxes, coupled with lateral movement capabilities means that, even if an organization detects and removes Nimbus Manticore from the initial infection point, the malware may have already established undiscovered footholds on other systems in the network. Incomplete remediation. Now imagine that scenario playing out over an entire week because your security tools simply couldn't see the threat.
Key Takeaways
Network security teams need to pay close attention to this one. Nimbus Manticore represents a class of threats that exploit the trust relationships between systems in your environment. Here's what you need to understand:
- Endpoint protection alone won't stop lateral movement. Even if you catch the initial infection, you need visibility into network-level threat activity to prevent propagation. RPC-based attacks happen between systems, not just on them.
- Dynamic component loading and import hiding mean your security tools need to analyze malware behavior, not just static signatures. Waiting to see what gets imported at runtime is too late if your detection approach requires seeing everything up front.
- Sandbox evasion is now a standard operating procedure. Any security strategy that depends entirely on automated analysis environments will miss threats specifically designed to avoid those environments. You need detection methods that can identify malicious intent without requiring full payload execution.
- The combination of privilege escalation and lateral movement capabilities makes containment challenging. Once malware like Nimbus Manticore gets administrative access and starts moving laterally, you're dealing with a highly-obfuscated network-wide incident.
Conclusion
Nimbus Manticore demonstrates how evolved obfuscation techniques can create lasting problems as they propagate across networks. This attack shows that modern malware authors understand both technical security controls and organizational security strategies.
It's designed to quietly establish persistence, escalate privileges, and spread across your infrastructure while remaining as invisible as possible and avoiding any potential checkpoints. That patient approach works exceptionally well against security tools that only look for immediate indicators of compromise.
Once inside, the RPC-based lateral movement capability is concerning because it exploits legitimate Windows functionality that most organizations depend on for normal operations. You can't simply disable RPC without breaking core business systems, which means attackers have a reliable pathway for spread that's difficult to defend against.
Organizations need security solutions that can identify malicious intent before full execution, and that provide visibility into both endpoint and network-level threat activity. Nimbus Manticore moves fast once it's inside your environment, and stopping it requires detection capabilities that move faster and work everywhere.
Deep Instinct has already proven it has what it takes to prevent Nimbus Manticore and countless other complex threats. Deep learning-powered cybersecurity capabilities aren’t a nice-to-have; they’re a requirement in the new cyber battlefield. Preemptive data security that scans every file and prevents threats before they execute is the perfect antidote for malware designed specifically to defeat modern security systems.
The name Nimbus Manticore might be over the top, but the threat is real. This malware has the tools to turn a single compromised endpoint into a network-wide security incident, and to keep popping back up.
Don't be one of those organizations. Don’t give the monster its opportunity. Request your free scan now to see what’s lurking in your environment.

