3 Reasons Why Ransomware Rollback is Not An Effective Strategy
“You’re only as good as your last backup” is a phrase all too familiar to any security practitioner or system administrator. Backups have been at the core of disaster recovery plans for as long as they have existed. Whether the issue is a drive that crashes or a ransomware attack, the objective is the same: recover the data and get the organization back on its feet as quickly as possible.
But as anyone involved in this process can attest – this is easier said than done.
There is a misconception being touted that if you get hit by a ransomware attack or infected by other malware, and you stop it soon enough, perhaps after “only four files were encrypted,” you can simply rollback to your last known clean backup. Which begs the question: can you rollback without business impact and be assured that you have completely eradicated the threat?
What is ransomware rollback remediation and what can go wrong?
The concept of “rollback remediation” is an evolution of the classic backup strategy. In this context, organizations use copies of important files stored on the local drive or remote stores to rapidly recover, or “rollback,” unwanted changes. In cybersecurity, those unwanted changes are often the result of ransomware, known or unknown malware, or a fileless or script-based attack.
Endpoint security solutions often leverage shadow copies and use the Volume Shadow Copy Service (VSS). VSS was introduced by Microsoft in Windows Server 2003 to better manage the backup of running applications – but relying on VSS and shadow copies is problematic in cybersecurity. The problem is that backups take up valuable storage space, so the just-in-time nature of VSS turns into a game of cat-and-mouse where it's a race against time to capture the right snapshots before the ransomware (or other malware) begins to encrypt or compromise your systems. And if your shadow copies are deleted, you are left to restore from your master backup.
Some security vendors have followed Microsoft’s lead and created their own file restoration utilities to provide a similar service that creates copies of important files as a hedge against an attacker encrypting or destroying them. But this is more of a hedge, not a solution.
3 Drawbacks to Ransomware Rollback
Why is ransomware rollback not an effective solution? We’ve put together the top 3 reasons why you might want to reconsider rollback as a strategy.
Ransomware Rollback Fact #1: The bad guys know about it, too
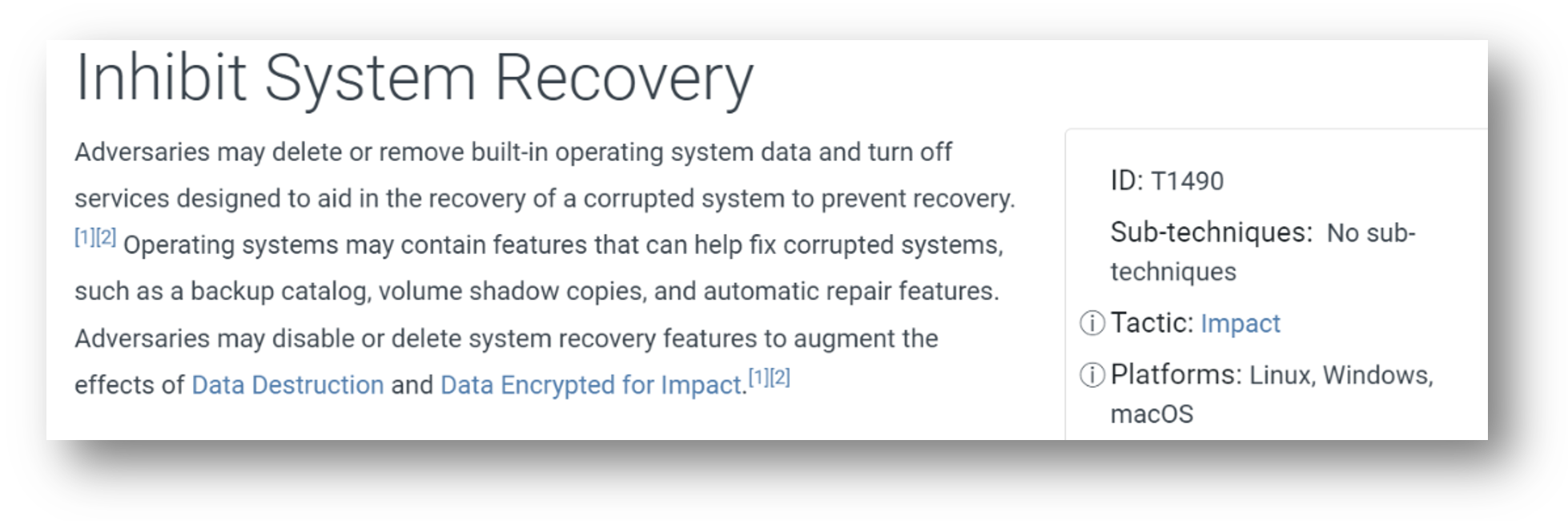
The first challenge with a rollback remediation strategy – ransomware or otherwise – is that threat actors know it’s in your playbook and understand that organizations rely on it to avoid paying a ransom by quickly restoring files to recover from ransomware attacks. Malware authors have leveraged the ‘vssadmin’ command to delete existing shadow copies for years. In fact, it happens so often that MITRE has added the technique to their ATT&CK framework (see Fig. 1 below). In some cases, ransomware has been written to disable VSS and then wait to execute the encryption to make sure any remaining shadow copies are rendered useless. Security researcher Florian Roth released a program called Raccine (ransomware vaccine), that looks for a process that tries to invoke ‘vssadmin delete shadows’ and kills the entire tree.
There are several other methods by which attackers can delete shadow copies.
- Wmic.exe with command line shadowcopy delete
- PowerShell with command line win32_shadowcopy
- Vssadmin.exe with command line resize shadowstorage
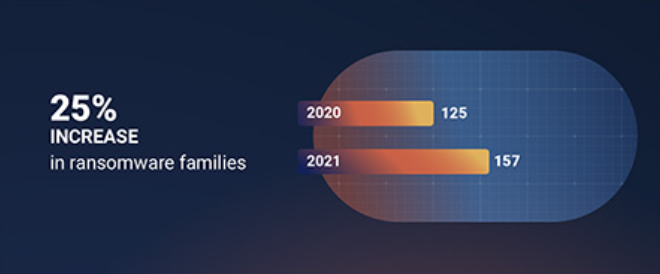
The most common ransomware families, including WannaCry, REvil, Robbinhood, and Conti remove shadow copies and/or disable file recovery features. The Ransomware Spotlight Year End 2021 Report from Ivanti, (see Fig. 2) shows that 32 new ransomware families appeared in 2021 alone (an increase of 25% over the previous year). Every new ransomware family represents an increased risk to an organization’s security, regardless of their backup or rollback strategy.
The recent and highly successful REvil ransomware campaign demonstrated this technique as it proliferated after compromising the Kaseya software distribution platform. As many as 1,500 organizations were affected by this campaign as REvil demanded a whopping $70 million ransom from Kaseya. And as previously mentioned, REvil relies on a mechanism to delete shadow copies, as do most ransomware families.
Ransomware Rollback Fact #2: Restoring files may get you back in business, but the threat remains
Killing the ransomware or other threat in progress and immediately restoring the damaged files is not a best practice. If you use rollback you may succeed in getting back to business with minimal downtime, but do you know if a backdoor was installed? And can you be sure you have eradicated the entire threat? Ransomware malware is not always how an attack is executed. Malware can contain a number of different suspicious threats beyond ransomware such as backdoors, potentially unwanted applications (PUA), and spyware, just to name a few. Any of those threats can be the entry point for ransomware, which is why malware classification is critical to know what it is the attacker is installing.
The prevalence of hybrid attacks that exfiltrate files for extortion before encrypting them brings this issue into sharp relief – just when you think the threat attackers are gone, can you be sure they won’t come back for more?
In the case of ransomware, file encryption is just the obvious final step for an attacker who’s already loose inside the environment. Once an attacker has successfully exerted control over an endpoint, there are many other actions they may have taken – and none of them are good.
When you look at an organization’s policies, nearly every incident response plan starts with “contain the breach,” not “restore the files.” Contain the breach means quickly identifying the attack, understanding its blast radius, and stopping its spread. If you roll back too soon you lose the opportunity to remove the entire threat and understand what else could possibly be affected. Establishing the timeline of point of entry is a critical step.
Once threat actors gain access to environment, a common attack strategy is to “break” the backup process while leaving the illusion that is still functioning properly. At times, attackers may wait 7 to 21 days to execute the attack or encrypt the files. This means that after a threat has been detected, organizations may have to go back days, weeks, or even months to restore systems back to their pre-infection state. The time to restore is measured in days, weeks, and months because servers, databases, and VMs must be rebuilt.
NIST’s incident response guidance for a ransomware attack is clear – containing the entire attack is the first step. Securing backups to prevent corruption is another important early step. Restoring from those backups should only happen after the environment is no longer infected. The reality is that if the attacker still has a foothold, there is nothing stopping them from encrypting again and the next time, they will make sure they kill off the backups.
Ransomware Rollback Fact #3: Ransomware is not the only threat to rollback
When it comes to relying on rollback for remediation, ransomware deleting shadow copies is not the only threat that you need to be concerned with. Newer attacks are corrupting backups or changing the encryption keys of the backup to something unrecoverable. And organizations would be unaware this is taking place unless they performed a backup restoration test, which is rare. Recent attacks include fileless malware and script-based attacks, which are even more difficult to identify and stop because they don’t insert malicious code onto the endpoint, but instead rely on built-in utilities of the system itself.
Specifically, PowerShell and Windows Management Instrumentations (WMI) are two key targets for this type of attack because of their increased privileges on the system. With these toolkits at their fingertips, attackers can easily delete shadow copies, shutdown critical system services, and establish persistence – all without triggering standard anti-virus programs. As mentioned previously, threat actors have been known to make it appear that backups are still up and running, making the job of detecting them even harder.
Preventing the attack avoids messy rollback scenarios
By preventing malware, including ransomware, before it can execute and infect a system, the entire attack chain is broken before it can even begin. Since the malware never launches, it can’t exfiltrate files for future extortion, encrypt files, or take other destructive actions. There is no need to rollback or restore because the system wasn’t infected in the first place.
Traditional EDR solutions are reactive and look for behaviors post-execution, providing attackers with the time they need to begin to breach your environment. Threat actors are constantly developing new attacks that evade detection, and EDR is not enough to stop attacks. For more information, check out the 8 Reasons EDR is Not Enough infographic and eBook.
When an attack is prevented pre-execution, your organization avoids the downstream costs of an active threat, meaning the threat actor never gets inside to disable your backups. While backups are still a vital piece of the security stack, it is far better to prevent an attack before any damage can be done to an organization's systems and data than to rely on a rollback strategy.
Deep Instinct takes a prevention-first approach to stopping ransomware, zero-day vulnerabilities, and other unknown malware pre-execution, reducing your reliance on flawed strategies like rollback. With innovative technology based on the only deep learning framework for cybersecurity, Deep Instinct can prevent >99% of attacks pre-execution, lowering your false positive rate to <0.1% and reducing your overall risk.
Sources
- docs.microsoft.com
Volume Shadow Copy Service deleted after ransomware attack - Backup no longer working - Microsoft Q&A
“Earlier this week the server was compromised by a ransomware attack. When I logged into the server the next day the shadow copies were all gone and also the windows server backup was not working anymore.” - csoonline.com
How to protect backups from ransomware | CSO Online
Ransomware is getting smarter, attacking backups to prevent recovery. Prevent this from happening by taking a few simple steps. - Born's Tech and Windows World
Raccine: Protect volume shadow copies from ransomware
[English]Interesting story - a security researcher has developed a tool called Raccine as a simple protection against ransomware. This should prevent ransomware or other malware from deleting the volume shadow copies on Windows NTFS drives. Ransomware deletes VSS copies when a Windows system is infected. - redcanary.com
It’s all fun and games until ransomware deletes the shadow copies
A malicious batch (.bat) file executed a PowerShell command that downloaded and executed a remotely hosted payload on Pastebin to deploy ransomware. Additionally, it launched the Volume Shadow Service Administration Tool (vssadmin.exe) to remove local shadow copies. - pkware.com
Ransomware Plus Exfiltration: Encrypt Your Data Before Someone Else Does
Starting in late 2019, a hybrid variety of cyberattack has emerged, in which traditional ransomware tactics are combined with data exfiltration. - Evading EDR
https://vanmieghem.io/blueprint-for-evading-edr-in-2022/

