Fileless Malware Attacks
What is a Fileless Malware Attack?
A fileless malware attack, or “executable-less attack”, is an attack during which no portable executable (PE) file is written to and executed from a disk. Moreover, in many attack sequences PE files may be used, but not written to disk, while in some attack sequences no PE files are used during the entire attack.
Fileless malware attacks are more difficult for security solutions to detect than traditional file-based attacks, due to the sophisticated methods of attack.
Advantages of fileless malware attacks
Attackers prefer fileless attack methods for three reasons:
- Static Detection Impossible: Because the malicious logic of the attack usually occurs only in memory, it makes static detection impossible (as no file is saved to the disk).
- Post-Event Analysis Complicated: Since many artifacts related to the attack exist in memory only, they may be overwritten or removed by the time of discovery (for example, through a reboot).
- Simplicity of Scripts and Admin Tools: The use of scripts and admin tools makes it easy for the attackers to hide their presence and purposes. Scripts can be easily obfuscated, and delivered in several stages, while actions performed by admin tools might seem legitimate to an organization.
All the above-mentioned methods enable attackers to hide a large portion of their attacks, which are detectable by organizations only post-compromise.
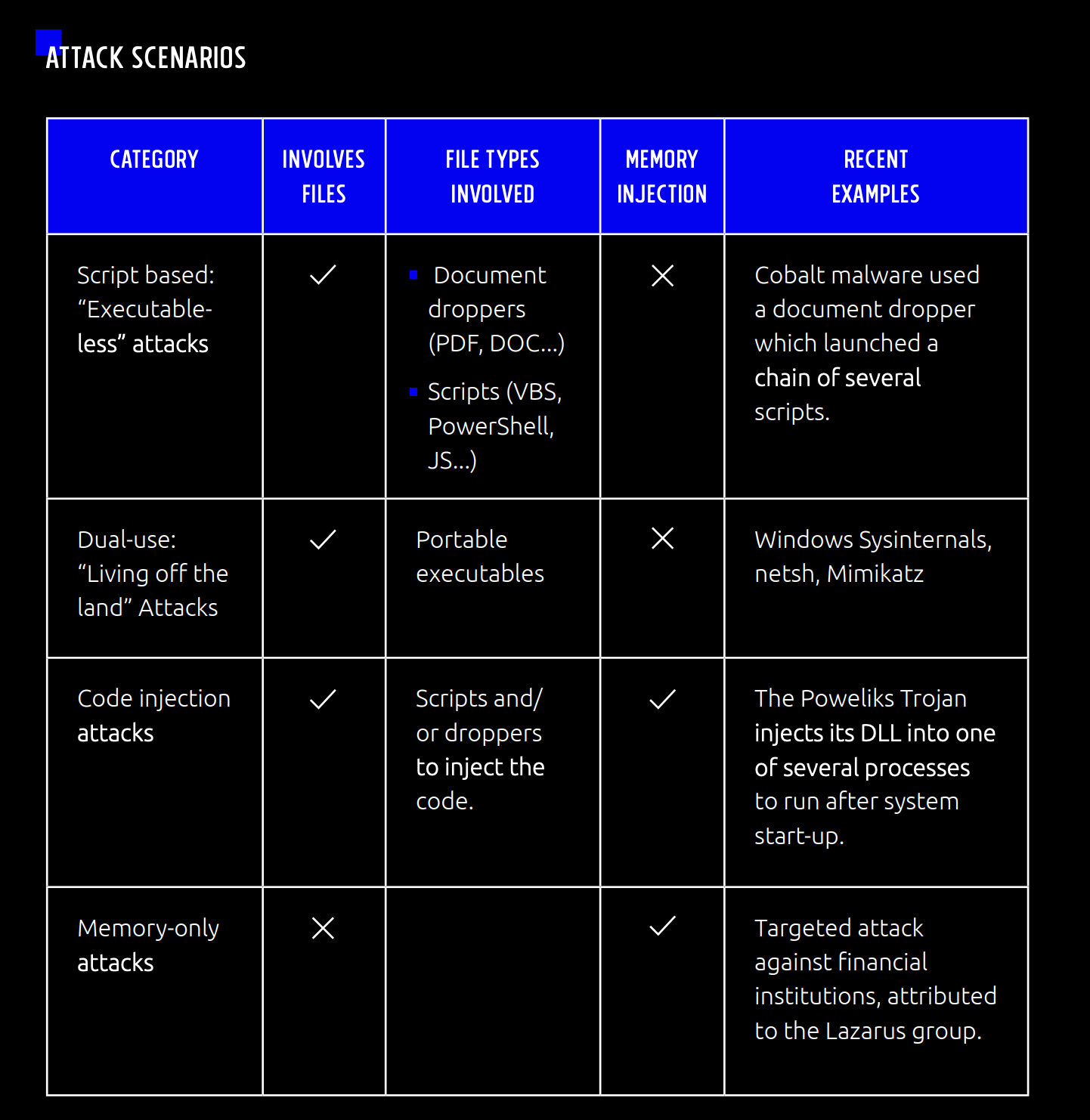
What are different kinds of fileless attacks?
The following attack scenarios fall under the scope of the current accepted definition of a fileless attack:
- Executable-less attacks
- Dual use attacks
- Code injection attacks
- Memory-only attacks
What are Fileless Malware Threats?
Fileless malware attacks pose a threat to organizations and a challenge for security vendors, due to the use of various non-executable file formats for infection, and the ability to execute parts of the malicious logic of the attack in-memory only. Fileless attack techniques were once mostly used by nation-states, but are now commonly adopted by cyber criminals after several high profile groups performed damaging fileless attacks in 2017.
How to protect from fileless malware attacks
There are 6 steps organizations and users can take to protect themselves from files attacks.
- Restrict the use of scripts and scripting languages. Apply different policies to different areas of the network. Allow scripts to run from read-only network locations or access-only specific machines.
- Restrict and monitor the use of Interactive PowerShell and WMI within an organization.
- Block execution of macros, and digitally sign trusted macros.
- Make sure all computers and programs are updated regularly. This will prevent the exploitation of known and patched vulnerabilities.
- Do not click on unknown or untrusted links. Do not open email attachments which are unknown or untrusted. Infection through social engineering is the most common method of infection.
- Deploy an advanced endpoint protection solution which can detect and mitigate fileless attacks. Some advanced endpoint solutions can also enforce all the points mentioned above.
How does Deep Instinct Protect from Fileless Malware Attacks?
Using advanced methodologies and deep learning, Deep Instinct protects its customers from all forms of fileless attacks. Script control mechanisms protect customers from executable-less attacks, code-injection and in-memory attacks, as these attack mechanisms usually rely on scripts during the attack flow. Advanced heuristics, which also protect against file-based attacks, quickly prevent code-injection and in-memory attacks. Finally, Deep Instinct’s unique deep learning model protects against the dual-use tools utilized in living off the land attacks, and against dropper files used in executable-less attacks, blocking these attacks pre-execution.