CVE-2023-23397: Exploitations in the Wild – What You Need to Know
Disclaimer: This blog contains sensitive information but since this information is publicly available and at least partially public knowledge we decided not to redact any information as it would cause this post to be irrelevant. Due to the simplicity of the attack and the fact it does not require user interaction we are urging everyone to patch their systems immediately.
On March 14, 2023, Microsoft released a security fix for an elevation-of-privilege vulnerability (CVE-2023-23397) in Microsoft Outlook.
A specially crafted email can trigger the vulnerability automatically when it is retrieved and processed by the Outlook client. Such an email could lead to exploitation before the email is viewed in the Preview Pane, which allows an attacker to steal credential hashes by forcing the target’s devices to authenticate to an attacker-controlled server.
The Computer Emergency Response Team for Ukraine (CERT-UA) reported the vulnerability to Microsoft. Based on Microsoft Threat Intelligence, a Russia-based threat actor used it in attacks to target and breach the network of several governments, military, energy, and transportation organizations in Europe between April and December 2022.
MDSec already demonstrated a POC of this attack and security researcher @KevTheHermit found a sample of an email attack in the wild.
Deep Instinct Threat Lab found additional samples exploiting this vulnerability including the potential attack that was reported by CERT-UA.
The samples can be grouped into five distinct clusters. Below is a timeline of the attacks:
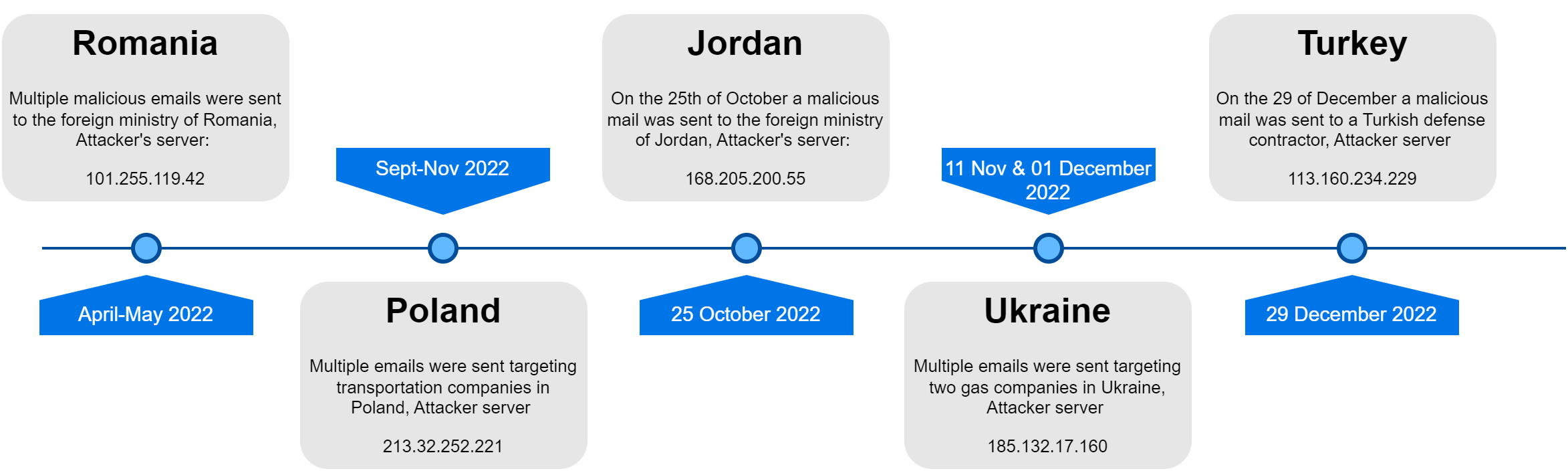
Possible Attribution
Microsoft attributed the attack to a Russian-based threat actor. The attacks on Romania, Poland, and Ukraine align with Russian interests, while the attacks on Jordan and Turkey might be related to a different threat actor.
This attack vector, which leads to NTLM harvesting, was also observed in 2020 by Iranian threat actors. Additionally, Russia and Iran have signed a cyber-cooperation agreement.
The Jordanian foreign ministry has been targeted in the past by Iranian threat actors, which might indicate the vulnerability was shared with the Iranians.
NTLM harvesting could be used either to hash relay attacks or for offline password cracking, indicating that the attacker either had prior access to the attacked organization or they have knowledge of remote-authentication services that do not require multi-factor authentication.
Hunting for the Vulnerability
Microsoft provided a PowerShell script to retroactively search for potentially malicious messages containing the vulnerability. The script looks for three types of messages – note, appointment, and task:
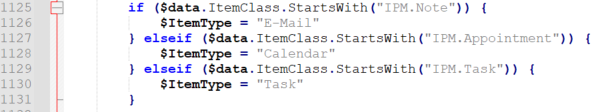
This could indicate that the vulnerability can be triggered by any of those types of messages. If you are using Outlook, you might be familiar with some of them:
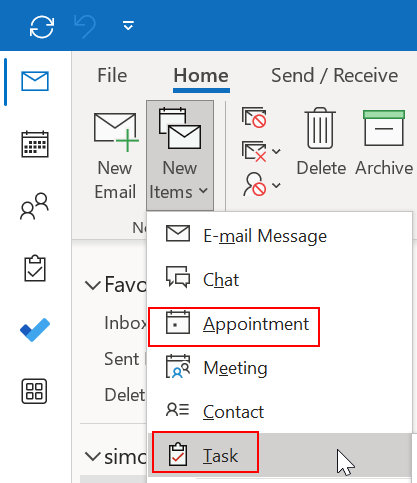
While MDSec used an “appointment” message in their POC, the attacks in the wild used a “task” message:

Using the following query in VirusTotal we found suspected emails with the vulnerability: “content:{490050004d002e005400610073006b00} tag:outlook”
If the email also contains a UNC path this means this is a malicious task using the vulnerability.
However, we found extracts from emails sent to Polish targets dated in the September timeframe that are not found via the query above:
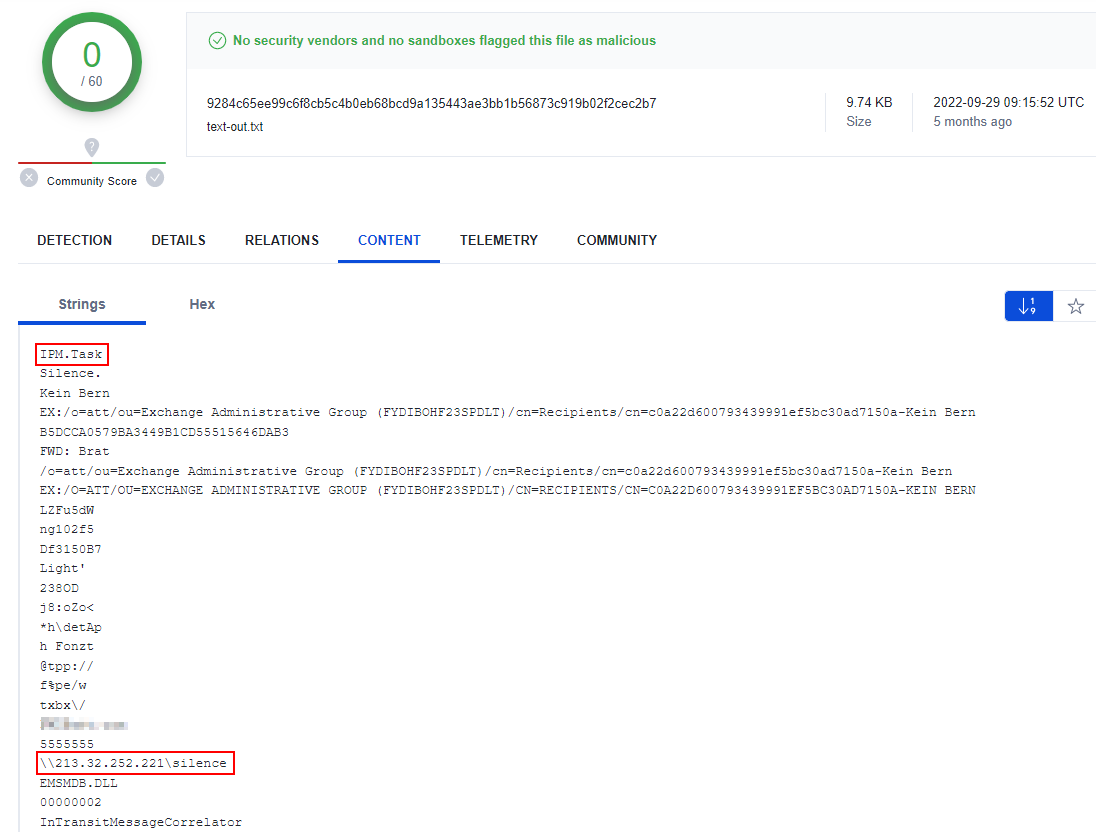
Conclusion
- While we found evidence of attacks starting in April 2022, there is a possibility that it was exploited even earlier.
- Due to the fact that we used only publicly available data the actual scope of attacked targets could be much higher.
- Microsoft attributed the attacks to a Russian-based threat actor; however, public evidence might suggest another threat actor exploited the vulnerability as well.
- Since the attack does not require user interaction, we urge everyone using the Outlook application to patch their systems as soon as possible.
- We also suggest running the PowerShell script provided by Microsoft to find retroactively malicious emails in the exchange server.
IOCs
24.142.165[.]2
101.255.119[.]42
113.160.234[.]229
168.205.200[.]55
181.209.99[.]204
185.132.17[.]160
213.32.252[.]221




