The Russian SpyAgent – a Decade Later and RAT Tools Remain at Risk
Deep Instinct Threat Lab researchers have observed changes in the distribution scheme of SpyAgent (A.K.A. TeamSpy/TVRat/TeamBot/Sheldor), a malware that likely originated over a decade ago based on the historical timeline below.
SpyAgent is a malware that abuses legitimate, well-known remote access tools (RAT). The recent changes observed by our team allow the malware to stay stealthy while bypassing and evading many security products.
Attackers evading existing security controls is a trend we see increasing. This is a problem for the industry as most security solutions that were developed with an “assume breach” mindset will miss these stealthy attacks until is it far too late to stop the damage.
Historical Background on SpyAgent:
- In a report from 2011, a malware named “Sheldor” used DLL search order hijacking to abuse TeamViewer 5.0 for malicious activities.
- In a report from 2013, a malware named “TeamSpy” used DLL search order hijacking to abuse TeamViewer 6.0 for malicious activities. The report also shows a relationship between “Sheldor” and “TeamSpy.”
- In a report from 2016, a malware named “Spy-Agent” used DLL search order hijacking to abuse TeamViewer 6.0 for malicious activities. The report contains unique URI patterns that the malware uses to communicate with the C&C server.
- SpyAgent’s main capabilities are leveraged to enhance the usage of TeamViewer by hooking some of the functions used by legitimate applications.
- The most important thing that SpyAgent does is obtain the client's unique ID, which is required to connect to a computer using TeamViewer.
- Other hooks disable logging and hide the GUI of the application to make it stealthy and avoid detection.
10 years later:
- A report published in 2021 showed that the “Spy-Agent” malware has been observed shifting from hijacking TeamViewer to hijacking “Safib Assistant,” a Russian replica of TeamViewer.
- The report demonstrates the distribution scheme of the malware, using fake crypto applications as a theme.
- The fake applications are actually downloaders of multiple malware families, which include different RATs and stealers, such as RedLine. “SpyAgent” is one of the downloaded malware families.
Recent Changes
In May 2022, a small change was observed in the fake crypto campaign first seen in 2021. Instead of using NSIS or Inno Setup droppers, executable files over 700MB were used to evade detection. This is because many security products limit the size of scanned files to compensate for performance issues. This is similar to the way the “Quartz.dll” SpyAgent files are inflated to 1GB+, as noted in the 2021 report. This is done by simply appending a large overlay of zeros to the file, and this technique allows the file to be compressed to the actual size without the overlay.
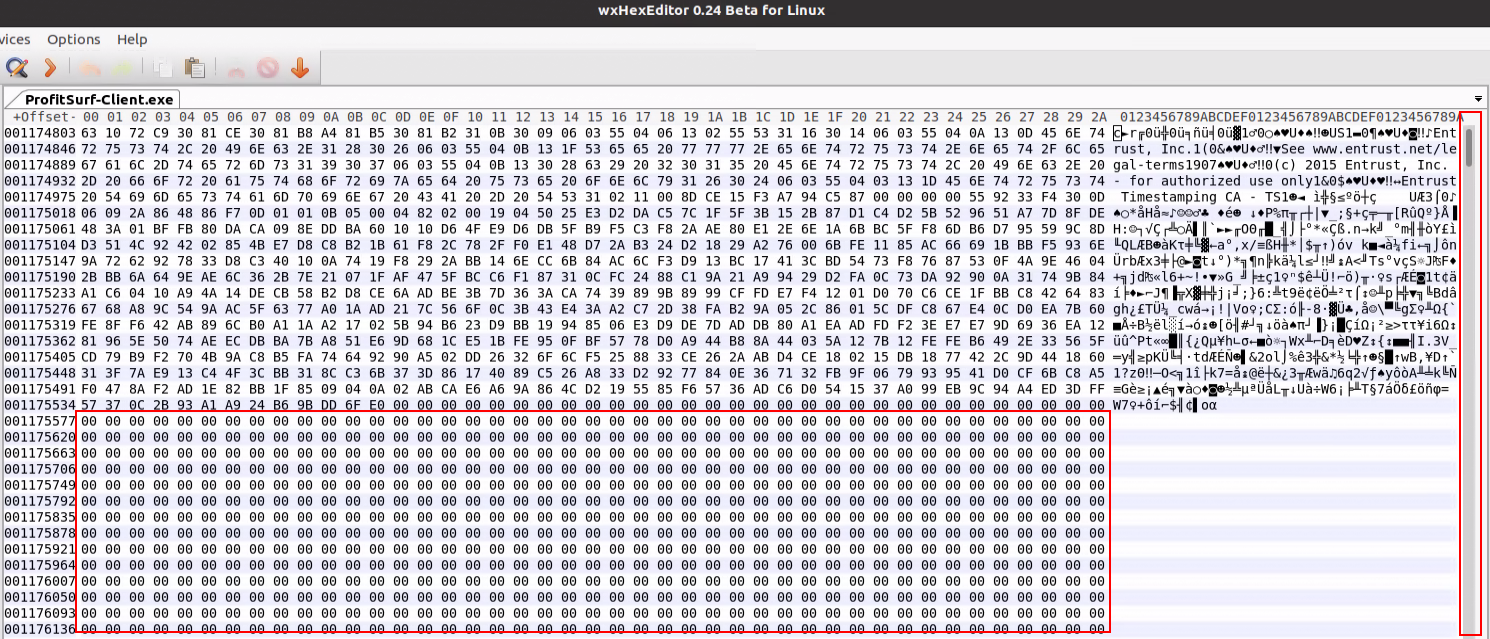
Due to their large size, the files are not stored in public malware repositories or sandboxes.
The large overlayed executables are droppers which use Microsoft’s .NET ClickOnce launch utility “AppLaunch.exe” to download and execute malware files from the web.
More malicious files related to this change can be found by searching the included txt file inside the zip:

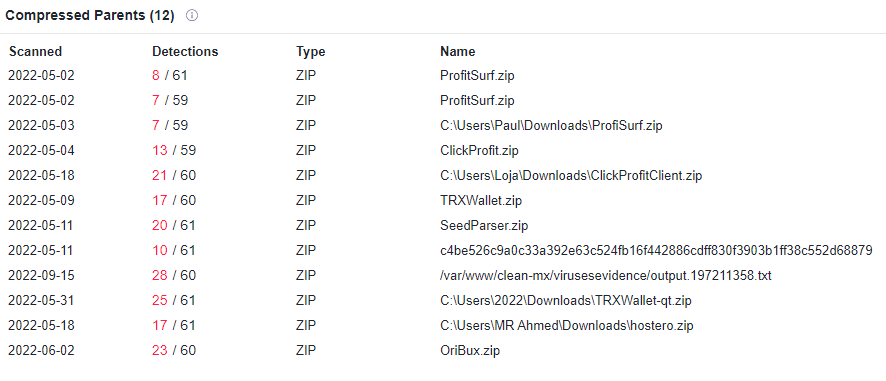
The text translates from Russian into:
- We execute the client inside the archive
- We enter our wallets to receive payments
- We are happy everyday because of the profit!
In June 2022, additional changes were observed.
The SpyAgent theme is no longer related to crypto applications.
The dropper files are once again Inno Setup files, however, they no longer download any additional malware except “SpyAgent” bundled with “Safib Assistant.”
Since “Safib Assistant” is a legitimate tool, similar to TeamViwer, just less known, this change lowers the detection rate for the campaign as the only real malware is “SpyAgent.”
However, as previously was reported, the “SpyAgent” DLL files are very large.
T1027.001 is a known MITRE technique that adversaries use to “decrease the effectiveness of certain tools and detection capabilities that are not designed or configured to scan large files. This may also reduce the likelihood of being collected for analysis. Public file scanning services, such as VirusTotal, limits the maximum size of an uploaded file to be analyzed.”
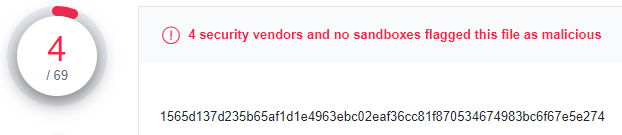
Example file
1565d137d235b65af1d1e4963ebc02eaf36cc81f870534674983bc6f67e5e274 is an Inno Setup file that during the writing of this article was detected by four security vendors:
This file is inside three different zip files, which are not related to a crypto theme.
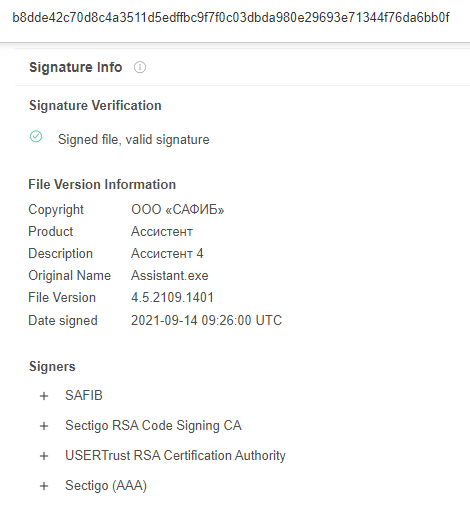
The dropper silently installs “Safib Assistant,” the software’s main executable hash is b8dde42c70d8c4a3511d5edffbc9f7f0c03dbda980e29693e71344f76da6bb0f and it is detected by only two security vendors, although it is not malicious without the SpyAgent DLL:
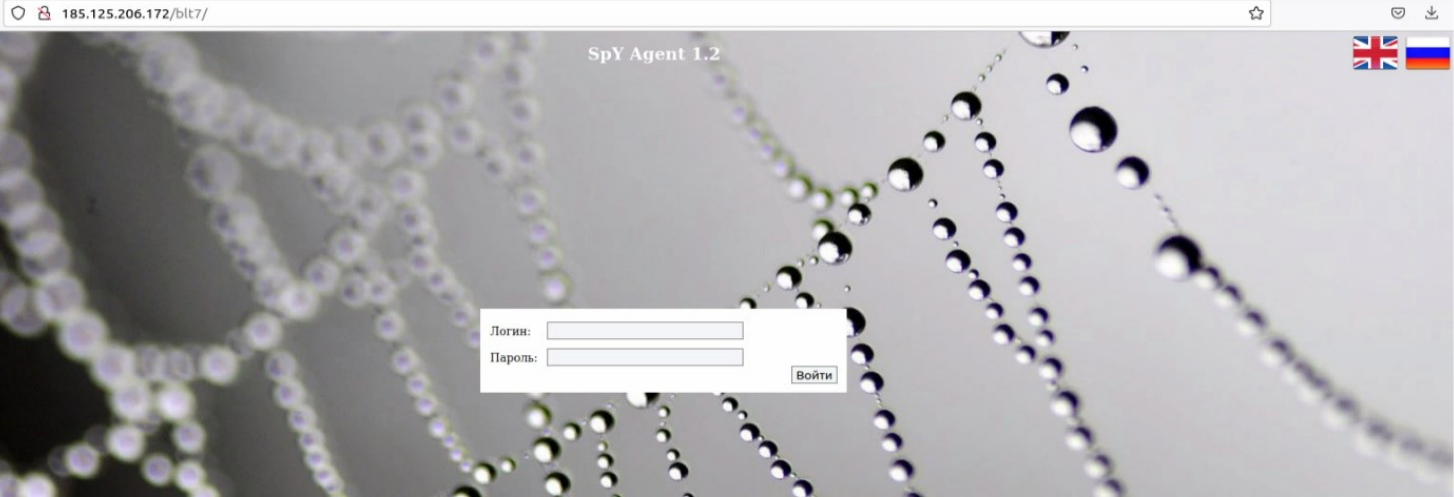
The SpyAgent C&C server is thief[.]lol which resolved during the analysis to the IP address 185.125.206[.]172.
During our investigation, the C&C was still working, allowing us to confirm that the malware bundled with “Safib Assistant” is indeed “SpyAgent:”
Conclusion
Both TeamViewer and “Safib Assistant” are legitimate remote admin tools, however, without the spy-agent malware DLL which adds stealth they are less useful for cybercriminal operations.
On the other hand, there are several other legitimate remote admin tools that don’t require any additional malicious DLL files to be stealthy which are used as-is by cybercriminals.
Deep Instinct classifies such tools as dual-use because they are 3rd-party software that is not necessarily allowed to be used in a corporate network as it can be used maliciously.
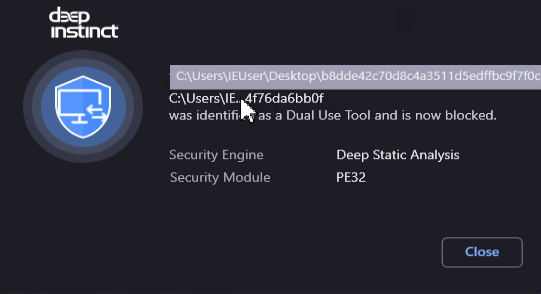
Deep Instinct blocks the Safib Assistant application.
MITRE ATT&CK:
|
|
|
|
|---|---|---|---|
Discovery | T1082 System Information Discovery | SpyAgent computes environment hash as an MD5 of the string created by concatenating the following:
Value 1 = to_uppercase(crc32(HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\MachineGuid)) Value 2 = to_uppercase(crc32(HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProductName)) Value 3 = to_uppercase(crc32(user name)) Value 4 = to_uppercase(crc32(computer name)) | <C&C domain>/<C&C path>?id=<9digit number>&stat=<environment hash> |
Defense Evasion | T1027.001 Obfuscated Files or Information: Binary Padding | SpyAgent’s quartz.dll was artificially inflated to the size of 1GB | e2eea1960d77aa8a7153ff448601974c – 7z file containing “Safib Assistant” bundled with SpyAgent’s quartz.dll |
|
| SpyAgent’s dropper executable was artificially inflated to the size of 700MB | c72710b4c1f85eca7d1441e1191faa9b – zip file containing dropper. |
| T1574.002 Hijack Execution Flow: DLL Side-Loading | SpyAgent hooks and patches various API functions called by the original DLLs used by TeamViewer and Safib Assistant | avicap32.dll quartz.dll |
| T1140 Deobfuscate/Decode Files or Information | SpyAgent comes with a config file (.cfg) that contains an encrypted configuration. The bitmap file (.bmp) is used for deriving the key to decrypt the config file | 80896fc71f5f9825a554858e15988713 – bmp file 6f496789009980fe92070f4e0d670797 – cfg file |
Command and Control | T1219 Remote Access Software | SpyAgent’s quartz.dll uses the “Safib Assistant” | 8002d9e5851728eb024b398cf19de390 - Assistant.exe |
|
| SpyAgent’s avicap32.dll uses TeamViewer | 28c4c35aed7949277a9c68a04a113114 - TeamViewer.exe |
| T1071.001 Web Protocols | SpyAgent uses HTTP for command and control | <C&C domain>/<C&C path>?id=<9digit number>&stat=<environment hash> |
IOC
1565d137d235b65af1d1e4963ebc02eaf36cc81f870534674983bc6f67e5e274
Active Spy Agent C2:
23.19.227[.]217
45.66.151[.]237
108.62.118[.]48
jmai[.]ink