Emotet Malware 2020
Emotet, the infamous malware botnet, went silent at the end of October and came back on December 21, 2020. The botnet continues to serve as a platform that installs other malware in the infected systems. Currently, it's being observed delivering Trickbot. Lithuania's National Public Health Center was hit by Emotet. The malware infected their internal networks and began downloading additional files, sending fake emails, and engaged in other types of malicious activity. This caused the institution to temporarily disable their email systems until the malware was removed.
We have been following the botnet operation. In the previous publications, we described the techniques used by Emotet to avoid detection by security products, and how to overcome them and unpack the malware.
In this blog post, the new loader of Emotet will be examined and compared to the previous one. We’ll describe the changes to the unpacking order, new unique properties of the files, and novel obfuscation methods. We’ll also talk about which evasion techniques and indicative features of the malware stayed the same.
Differences
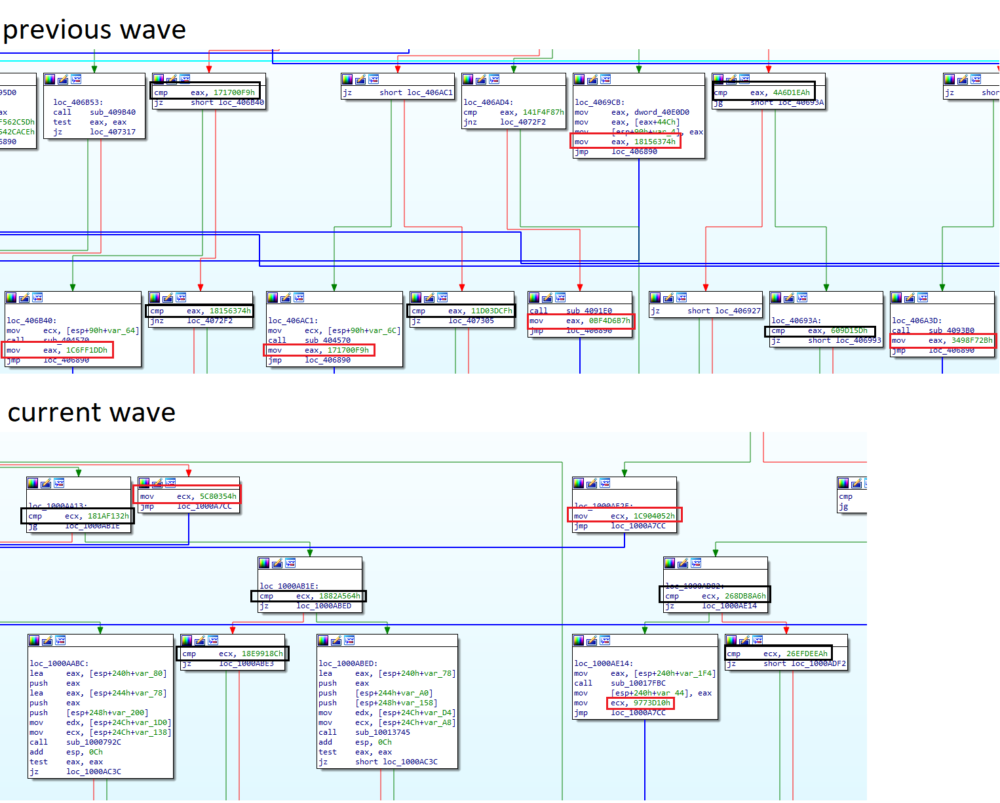
- Execution flow – The malware is packed and there are several steps performed before the final payload is executed.
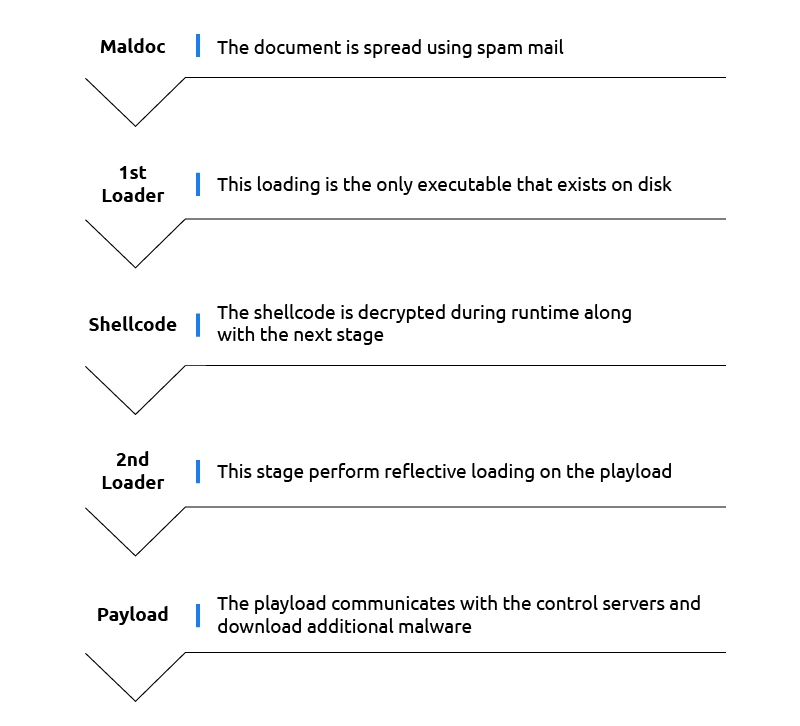
From the samples we recently gathered, the number of steps executed was cut down:
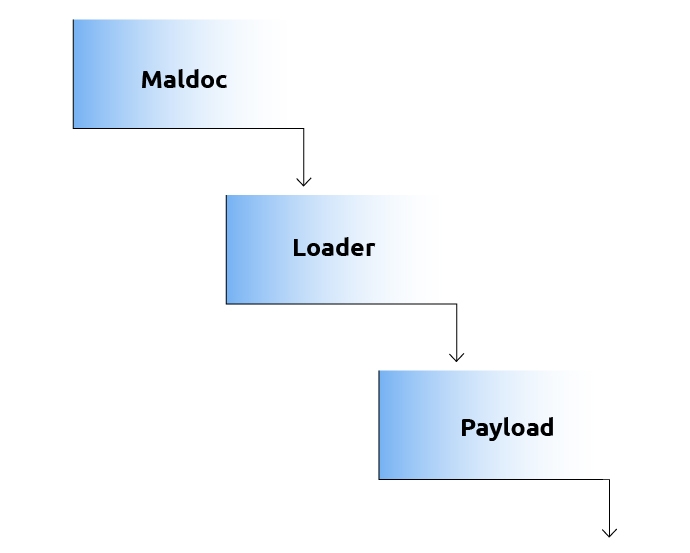
The reason for that is unclear, but our hypothesis is that the longer unpacking process was ineffective at reducing detection rates. Emotet uses a technique called reflective loading to load all of its stages. If a certain security product can detect reflective loading, using it multiple times won’t help to evade it. Another explanation can be that they are trying to evade heuristics that were created specifically for Emotet. The previous execution flow was very long and unique. If their malware is prevented by detecting this specific flow, changing it might help.
2. The Loader – The loader went through a few changes, the first of which is switching from an executable file to a DLL. This DLL has unique exports: “RunDLL” and “Control_RunDLL”. This makes it possible to detect Emotet infections with EDR. If the process rundll32.exe was started with a parameter that matches the export, the system would be infected.
Samples can also be detected with the following YARA rule:
import "pe"
private rule emotet_exports
{
condition:
pe.exports("RunDLL") or pe.exports("Control_RunDLL")
}
private rule is_dll
{
condition:
pe.characteristics & pe.DLL
}
rule emotet
{
condition:
is_dll and emotet_exports
}
We noticed another important change from the samples we manually examined. It looks like some of them do not contain benign code. This technique was used by the malware to reduce the detection rate and bypass security products but has since disappeared.
3. Additional obfuscation – A new code obfuscation technique was observed in payloads extracted from the loaders. They set the value in local variables using many bit-wise operations instead of a single, simple operation. This form of obfuscation makes it is harder to understand the code without executing it and makes the debugging process more tedious.
Similarities
1. Decryption algorithm – The payload is stored as an encrypted resource inside the loader. While performing the research on the previous wave of Emotet, we developed a tool that is able the decrypt and extract the payload statically, without executing the malware. This tool is still viable for recent samples, and this shows the developers did not change the algorithm.
2. Code obfuscation – In addition to the obfuscation described above, there is an obfuscation technique that also existed in the previous version of the payload. The code contains a complicated switch case and unnecessary jump instructions making it harder to understand the natural order of the code.
3. Hidden data – The payload conceals its functionality by not listing any WinAPI import or meaningful string. This subverts the static analysis and forces the researcher to debug the malware to discover this data. The strings are stored in an encrypted form, and the APIs are resolved using a hash of their name. The decryption algorithm of the strings and the hashing algorithm of the APIs stayed the same.
Practice Makes Perfect
By assessing the stages of 2020's new trojan of Emotet, the changes and new techniques used by the malware were identified along with the parts and features that have stayed the same.
Emotet is known as very evasive malware. These modifications indicate a desire to decrease their detection rate as much as possible. The techniques that were found useful for bypassing security products were kept, while the methods that were improved or removed are reflective of an agile methodology of improving on what isn’t sufficiently effective.
Keeping track of modifications in malware such as Emotet is vital because of their wide infection base. New evasion or injection techniques might help the malware to bypass security products and infect many systems.